This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364
Summary
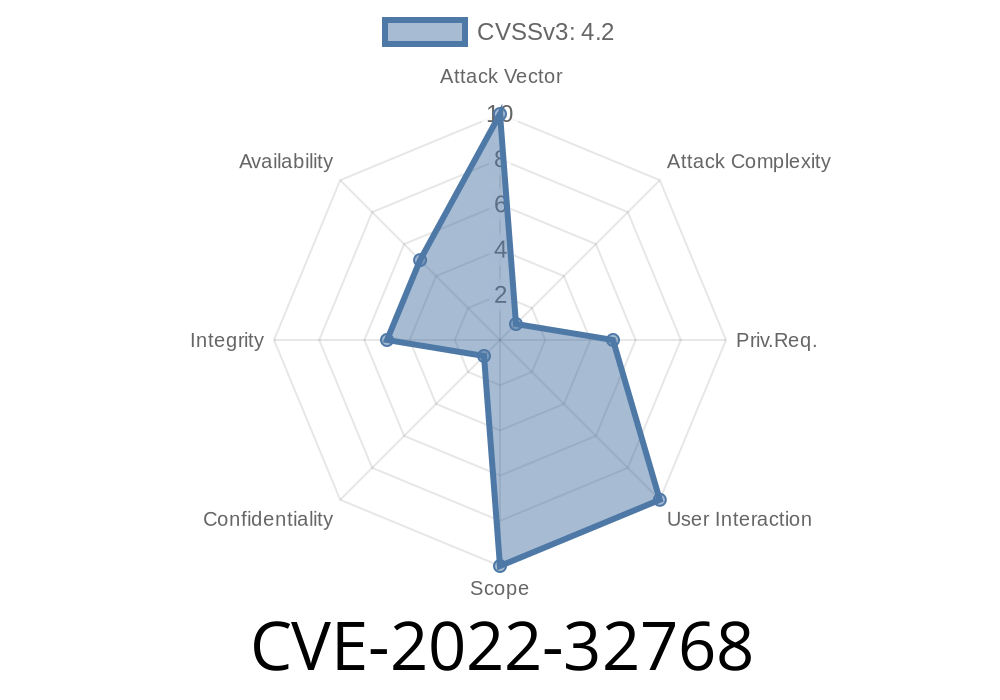
The CVE-2022-32768 vulnerability is a remote code execution vulnerability that can be exploited by an attacker by sending an HTTP request to the vulnerable plugin. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability.
This vulnerability affects versions 11.6 and dev master commit 3f7c0364 of the AVideo plugin for WordPress, which are both vulnerable to multiple authentication bypass vulnerabilities.
CVE-2019-32769
This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364
Vulnerability Scenario##
A Video plugin that can be exploited by a cross-site scripting attack.
Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter. Multiple authentication bypass vulnerabilities exist in the object id handling functionality of WWBN AVideo 11.6 and dev master commit 3f7c0364. An authenticated user can send an HTTP request to trigger this vulnerability. This can be exploited by an attacker by sending an HTTP request to the vulnerable plugin with a specially-crafted parameter
Timeline
Published on: 08/22/2022 19:15:00 UTC
Last modified on: 08/24/2022 18:15:00 UTC