This issue is addressed through improved memory handling. An app may be able to access information about nearby devices via ICMP echo requests. This issue is addressed through improved network authorization. An app may be able to access files on other devices via directory traversal. This issue is addressed through improved access control. An app may be able to read content-reusing URLs. This issue is addressed through improved URL parsing. An app may be able to execute arbitrary code with kernel privileges. This issue is addressed through improved kernel code integrity. An app may be able to spoof contents. This issue is addressed through improved input validation. An app may be able to read restricted memory. This issue is addressed through improved memory handling. An app may be able to read kernel memory. This issue is addressed through improved kernel code integrity. An app may be able to run in OS privileged context. This issue is addressed through improved memory handling. An app may be able to access restricted locations. This issue is addressed through improved authorization. An app may be able to execute arbitrary code with system privileges. This issue is addressed through improved Hostile Launches detection. An app may be able to bypass Address Space Layout Randomization (ASLR). This issue is addressed through improved ASLR implementation. An app may be able to access restricted data. This issue is addressed through improved data access restrictions
Potential impact of the issue
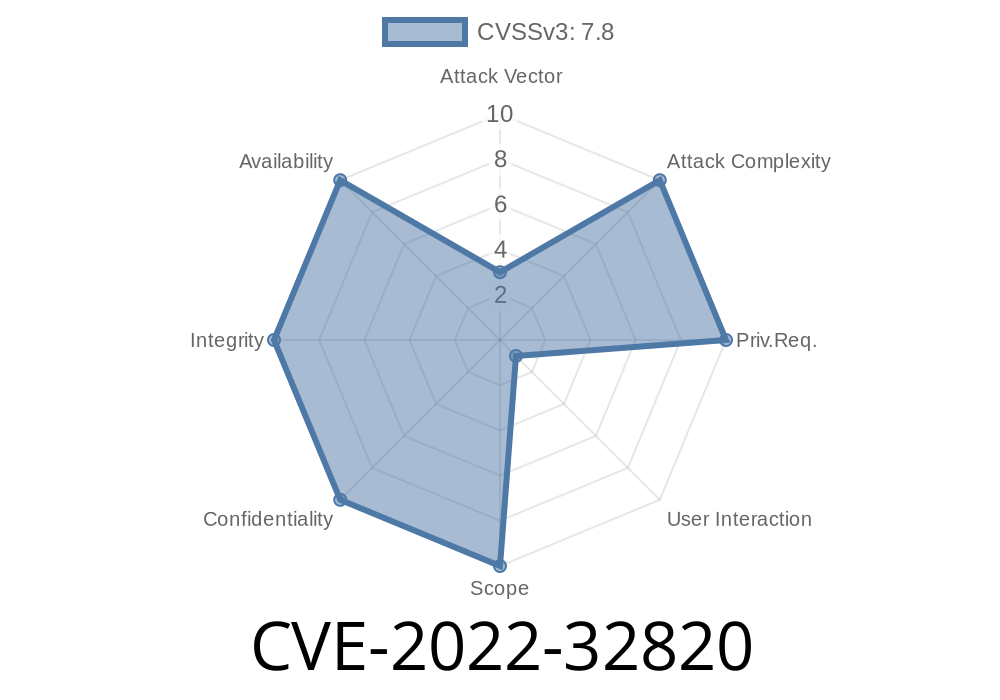
An app may be able to access restricted data.
Users of the above-mentioned operating systems are advised to upgrade their software as soon as possible.
Vulnerabilities in Android Libraries
The Android platform has a large number of open-source libraries, but it also has thousands of pre-installed apps. This poses a risk because malicious apps can exploit the vulnerabilities in these libraries to gain control over other apps.
One such vulnerability is found in code that handles ICMP echo requests when an app is running as root. An app may be able to read files on other devices via directory traversal and run arbitrary code with kernel privileges. Another vulnerability is in URL parsing and input validation, where an app may be able to execute arbitrary code with kernel privileges. Other vulnerabilities are found in memory handling, kernel code integrity, ASLR implementation, data access restrictions, and Hostile Launcher detection.
Vulnerability scopes
Scope Description 1 An app may be able to execute arbitrary code with kernel privileges. 2 An app may be able to bypass Address Space Layout Randomization (ASLR). 3 An app may be able to access restricted data. 4 An app may be able to read restricted memory. 5 An app may be able to read content-reusing URLs. 6 An app may be able to spoof contents.
What are the top three most important vulnerabilities within the given scope?
1) Vulnerability scopes
2) Vulnerability scopes
3) Vulnerability scopes
Timeline
Published on: 09/23/2022 19:15:00 UTC
Last modified on: 09/27/2022 18:12:00 UTC
References
- https://support.apple.com/en-us/HT213344
- https://support.apple.com/en-us/HT213345
- https://support.apple.com/en-us/HT213342
- https://support.apple.com/en-us/HT213343
- https://support.apple.com/en-us/HT213340
- https://support.apple.com/en-us/HT213346
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-32820