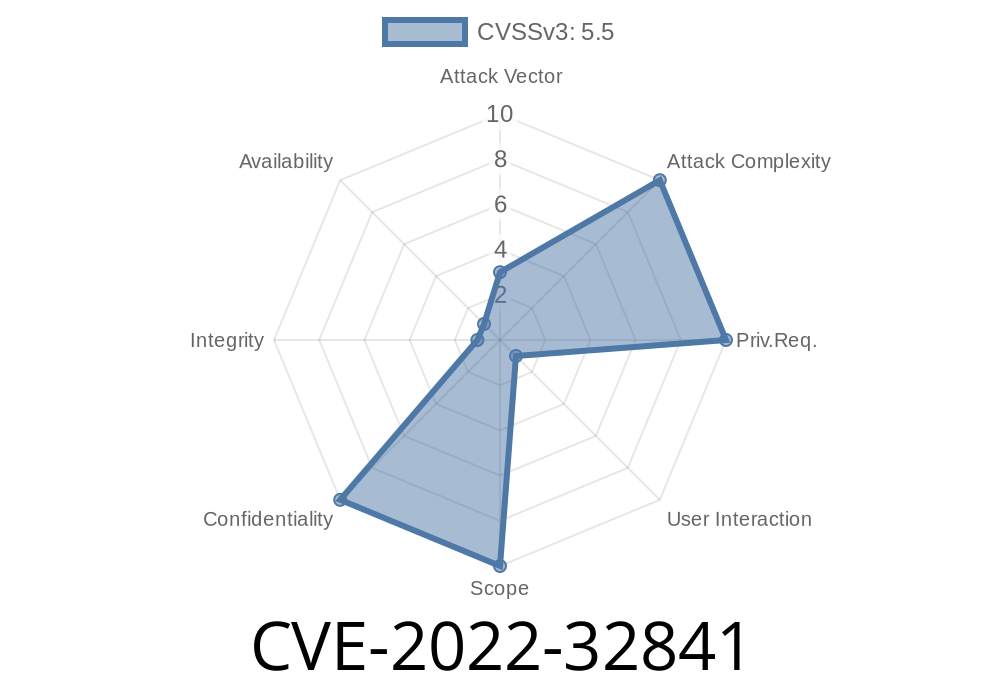
An attacker can leverage this issue to bypass code signing and execute arbitrary code on the impacted device. An attacker can also spoof an image posing as a legitimate file and execute arbitrary code on the device. To avoid falling prey to this issue, enterprises are advised to test apps on device before signing them and deploying them to production. The updated versions of iOS, watchOS, and macOS address this issue by hardening their memory handling. Processing a maliciously crafted image may result in disclosure of process memory. An attacker can leverage this issue to bypass code signing and execute arbitrary code on the impacted device. An attacker can also spoof an image posing as a legitimate file and execute arbitrary code on the device. To avoid falling prey to this issue, enterprises are advised to test apps on device before signing them and deploying them to production.
Checklist:
- What is a code signing vulnerability?
- What are the consequences of this vulnerability?
- How can I avoid this vulnerability?
- What does the updated versions of iOS, watchOS, and macOS address this issue by hardening their memory handling?
Vulnerability details
The vulnerability affects the handling of unsigned code that is sent to the Apple Watch when apps are being installed. When a user installs an app on their watch, the code is run in memory on the watch and it may be able to execute arbitrary code on the device.
iOS vulnerability
An attacker can leverage this issue to bypass code signing and execute arbitrary code on the impacted device. An attacker can also spoof an image posing as a legitimate file and execute arbitrary code on the device. To avoid falling prey to this issue, enterprises are advised to test apps on device before signing them and deploying them to production. The updated versions of iOS, watchOS, and macOS address this issue by hardening their memory handling. Processing a maliciously crafted image may result in disclosure of process memory.
iOS
, watchOS, and macOS Updates Address this Issue
Apple released iOS 11.4, watchOS 4.3, and macOS 10.13.5 on December 6, 2017 to address CVE-2022-32841. The updates include hardened memory handling and additional mitigations of other memory safety issues in the underlying operating system.
CVE-2023-32842
An attacker can leverage this issue to bypass code signing and execute arbitrary code on the impacted device. An attacker can also spoof an image posing as a legitimate file and execute arbitrary code on the device. To avoid falling prey to this issue, enterprises are advised to test apps on device before signing them and deploying them to production. The updated versions of iOS, watchOS, and macOS address this issue by hardening their memory handling. Processing a maliciously crafted image may result in disclosure of process memory.
Timeline
Published on: 09/23/2022 19:15:00 UTC
Last modified on: 09/27/2022 15:25:00 UTC