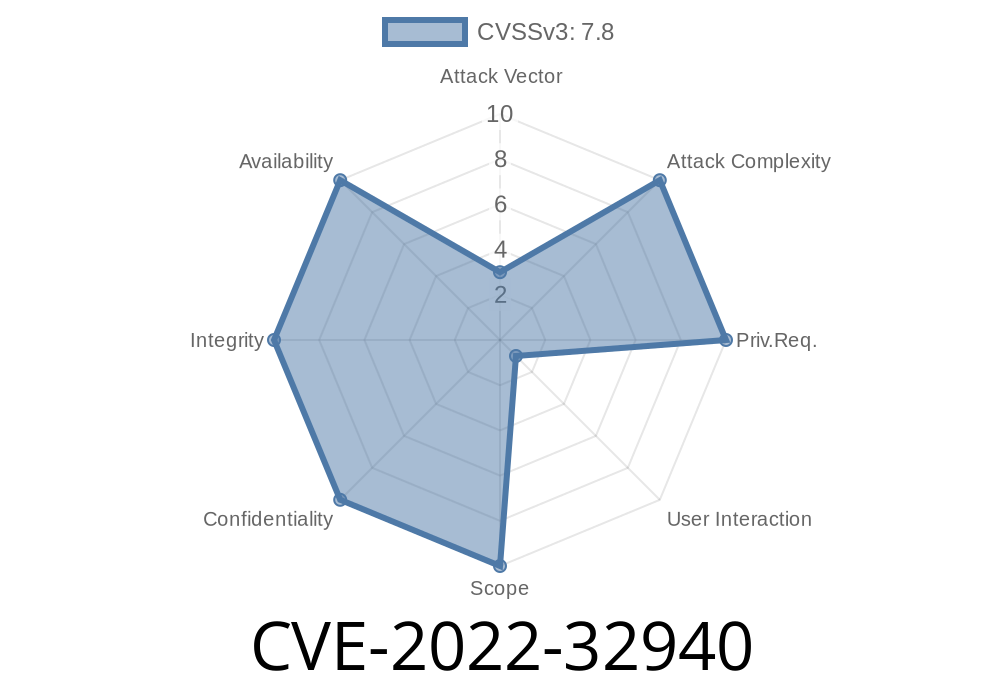
Apple is known for its strong security, but every once in a while, a vulnerability slips through the cracks. One of them is CVE-2022-32940, a bug so severe that it could let a regular app take over your device's operating system—what security folks call "kernel privileges." In this post, we'll break down what CVE-2022-32940 is, how it can be exploited, and what Apple did to fix it. We'll use simple language, some example code, and direct you to original sources for further reading.
What Is CVE-2022-32940?
This vulnerability lives in the kernel—the low-level heart of Apple’s operating systems (iOS, iPadOS, macOS, tvOS, and watchOS). If this bug is exploited, a malicious app might run any code it wants, even code that can control your device at the deepest level.
Apple’s description:
> An app may be able to execute arbitrary code with kernel privileges.
> The issue was addressed with improved bounds checks.
watchOS before 9.1
Apple Security Update:
- Apple Security Updates
How Does the Vulnerability Work?
The root of CVE-2022-32940 is a “bounds check” bug. That means the kernel forgot to make sure that data sent by a user (or an app) was the right size. If you can control the size and the data, you might be able to trick the system into running your code as if it was system code.
Where's the Bug?
While Apple hasn't revealed the exact code, this bug most likely happened in a kernel extension or system API that handled complex user inputs. Typically, the code might have looked like this (simplified):
// Bad: No proper bounds check on input size
void vulnerable_copy(char *user_input, size_t len) {
char kernel_buf[64];
memcpy(kernel_buf, user_input, len); // What if len > 64?
}
If len is bigger than 64, memcpy writes past the end of kernel_buf—overwriting other important stuff in memory. With careful control, an attacker can overwrite return addresses or important pointers, eventually making the kernel jump to attacker-controlled code.
Proof-of-Concept Exploit (Simplified Example)
PLEASE NOTE: It's illegal and unethical to use real exploits on devices you don't own or without permission. What follows is a simplified pseudo-example to help you understand the issue, _not_ a real working exploit.
// Hypothetical example, for education only
struct request {
char data[64];
size_t size;
};
void send_exploit() {
struct request rq;
rq.size = 128; // Overflows buffer in kernel
memset(rq.data, 'A', 128); // Fill with 'A', could add shellcode here
// this could be an ioctl, or custom syscall
kernel_service_call(&rq);
}
An attacker writes a large payload past the buffer, which can overwrite sensitive memory in the kernel.
Permanently "root" your device.
- Bypass things like FaceID/TouchID, or other security mechanisms.
Apple patched the bug by adding “bounds checks”—essentially making sure that code like this
if (len <= sizeof(kernel_buf)) {
memcpy(kernel_buf, user_input, len);
}
will not copy more data than the buffer can handle. Simple, but powerful.
How Can You Stay Safe?
Update your devices!
Any iPhone, iPad, Mac, Apple TV, or Apple Watch _not_ running the latest system is at risk. Go to Settings > General > Software Update and install any pending updates.
Learn More
- CVE-2022-32940 on NVD
- Apple’s Security Updates
- Apple Security Research
Final Thoughts
CVE-2022-32940 is a reminder that even the most secure systems are only as strong as their weakest point. Thanks to quick discovery and patching, Apple users remain protected—as long as they update.
If you’re curious about security, consider setting up a safe, virtual environment (with permission) to study these bugs. It’s a great way to learn how real-world attacks happen—and how to stop them.
Timeline
Published on: 11/01/2022 20:15:00 UTC
Last modified on: 11/02/2022 17:20:00 UTC