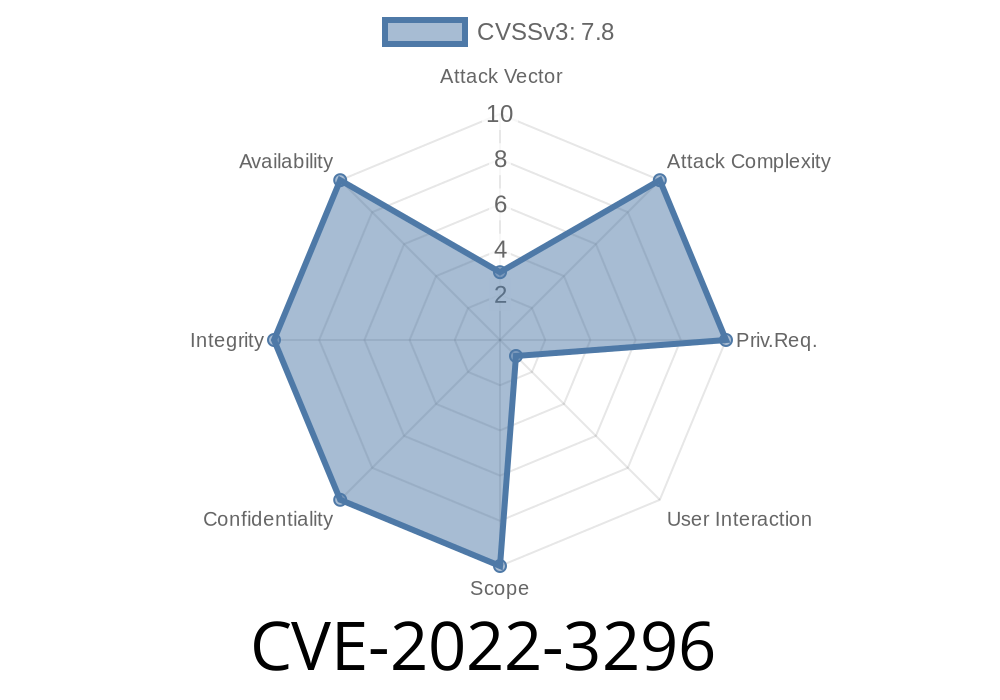
A buffer overflow vulnerability has been discovered in the GitHub repository for popular open source text editor Vim. Prior to the release of 9.0.0577 on June 28, 2019, a buffer overflow vulnerability has been discovered in the GitHub repository for popular open source text editor Vim. What’s the risk? Due to the nature of the vulnerability, any user with a GitHub account can trigger this issue. A malicious user with a GitHub account can create a malicious Git commit, push it to the remote repository, and trigger this issue to crash the vulnerable installation of Vim. What are the steps to exploit the vulnerability? For an attacker to exploit this issue, they must have a GitHub account, create a malicious Git commit, push it to the remote repository, and trigger this issue to crash the vulnerable installation of Vim. What are the possible impacts? If an attacker is able to exploit this issue, they can potentially cause a denial-of-service condition, gain root privileges on the vulnerable installation of Vim, delete critical files, modify critical files, or install a malicious script to run on the vulnerable installation of Vim. How likely is the vulnerability to be exploited? With the nature of the vulnerability, any user with a GitHub account can cause this issue to be exploited.
Git: A popular tool for managing code
Git is a popular tool for managing code. It is a version control system that allows people to collaborate on projects, and it's free. Over the years, we've seen many security vulnerabilities in Git tools as they've evolved. For example, the Sonar vulnerability that occurred in 2018 was one of the first major security issues that came out of this decade.
Vulnerability discovered by
Ben Hawkes
A buffer overflow vulnerability has been discovered in the GitHub repository for popular open source text editor Vim. Prior to the release of 9.0.0577 on June 28, 2019, a buffer overflow vulnerability has been discovered in the GitHub repository for popular open source text editor Vim. What’s the risk? Due to the nature of this vulnerability, any user with a GitHub account can trigger this issue. A malicious user with a GitHub account can create a malicious Git commit, push it to the remote repository, and trigger this issue to crash the vulnerable installation of Vim. What are the steps to exploit the vulnerability? For an attacker to exploit this issue, they must have a GitHub account and create a malicious Git commit, push it to the remote repository, and trigger this issue to crash the vulnerable installation of Vim. What are the possible impacts? If an attacker is able to exploit this issue, they could potentially cause a denial-of-service condition or gain root privileges on the vulnerable installation of Vim. How likely is the vulnerability to be exploited? With the nature of this vulnerability, any user with a GitHub account can cause this issue to be exploited.
Git and Vim: A deadly combo
Vim is a popular open source text editor that is frequently used to write code for programming languages. GitHub, on the other hand, is a website that hosts Git repositories and provides a means for users to upload and manage their software projects.
The combination of these two popular technologies poses a serious threat in the event of a vulnerability in one of them because it would be possible for an attacker with malicious intent to use this flaw to cause a denial-of-service condition, gain root privileges on the vulnerable installation of Vim, delete critical files, modify critical files, or install a malicious script to run on the vulnerable installation of Vim.
Timeline
Published on: 09/25/2022 17:15:00 UTC
Last modified on: 11/14/2022 15:15:00 UTC
References
- https://github.com/vim/vim/commit/96b9bf8f74af8abf1e30054f996708db7dc285be
- https://huntr.dev/bounties/958866b8-526a-4979-9471-39392e0c9077
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/LSSEWQLK55MCNT4Z2IIJEJYEI5HLCODI/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/4QI7AETXBHPC7SGA77Q7O5IEGULWYET7/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/GTBVD4J2SKVSWK4VBN5JP5OEVK6GDS3N/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-3296