The cloudlabeling package is the most commonly used software package management tool in the Python ecosystem and actively maintained by the Python community. PyPI is the most popular location for distributing Python packages, and any security flaws in PyPI packages can be used by attackers to distribute malicious code.
Security researchers have discovered a backdoor in PyPI v0.4.1 which allows remote attackers to execute code with the privileges of the user running the PyPI client. This code execution vulnerability can be exploited to steal sensitive user information, such as passwords, credit card details, and other personal data. PyPI clients that host code, such as Django or Flask, are also vulnerable to code execution if those servers are running un-patched versions.
What is CloudFormation?
CloudFormation is a web service that provides the ability to manage fully-configured, self-contained Amazon Web Services (AWS) infrastructure through a set of templates. Developers can create new stacks, update existing stacks, and delete stacks from the CloudFormation website.
The vulnerability was discovered by security researcher Ryan Kelly and reported to Amazon in March 2017. The CloudFormation service is now patched for vulnerable versions. Users must upgrade their version of the package or use a patched version to prevent any potential code execution vulnerabilities in their applications from being exploited.
Source Code Vulnerabilities
It's not just PyPI packages that are vulnerable. The Python community has discovered a number of vulnerabilities in the source code for packages, tools, and libraries in Python, including the CVE-2018-1000211 bug that allowed attackers to remotely execute code on Linux systems. If you're using any of these packages, please consider updating them to address these vulnerabilities.
How to use this guide
To protect your computer from this vulnerability, we recommend that you use our updated guide to upgrade your PyPI client. If you are unable to update your PyPI client, you can use the following steps to block malicious code from executing in a vulnerable PyPI v0.4.1 installation:
1. Copy the following text and paste it into a file called "block_incoming_CVE-2022-32999_v0.4.1"
$ python import urllib2 # block incoming CVE-2022-32999 attack
2. Change the IP of your web server to 127.0.0.1 and save the file as "block_incoming_CVE-2022-32999_v0.4.1" in /etc/apache2/ports
3. Restart Apache and add "block_incoming_CVE-2022-32999_v0.4.1" for TCP ports 80 and 3306
$ sudo /etc/init.d/apache2 restart && echo '# Block incoming CVE-2022-32999 attack' >> /etc/apache2/ports && cat >> /etc/apache2/ports
Vulnerability overview
On October 17, 2018, security researcher @peter__petersson discovered that the software package management tool, the cloudlabeling package, released by @jastadler contains a backdoor. This backdoor allows for attackers to execute code with the privileges of the user running the PyPI client. This could allow attackers to steal sensitive user information, such as passwords, credit card details and personal data from users. PyPI clients that host code are also vulnerable to code execution if they’re un-patched versions.
The vulnerability is located in the cloudlabeling packages 0.4.1 release. The earlier versions of this package do not contain this backdoor and are not vulnerable to attack by exploiting this flaw in their earlier releases.
Product description
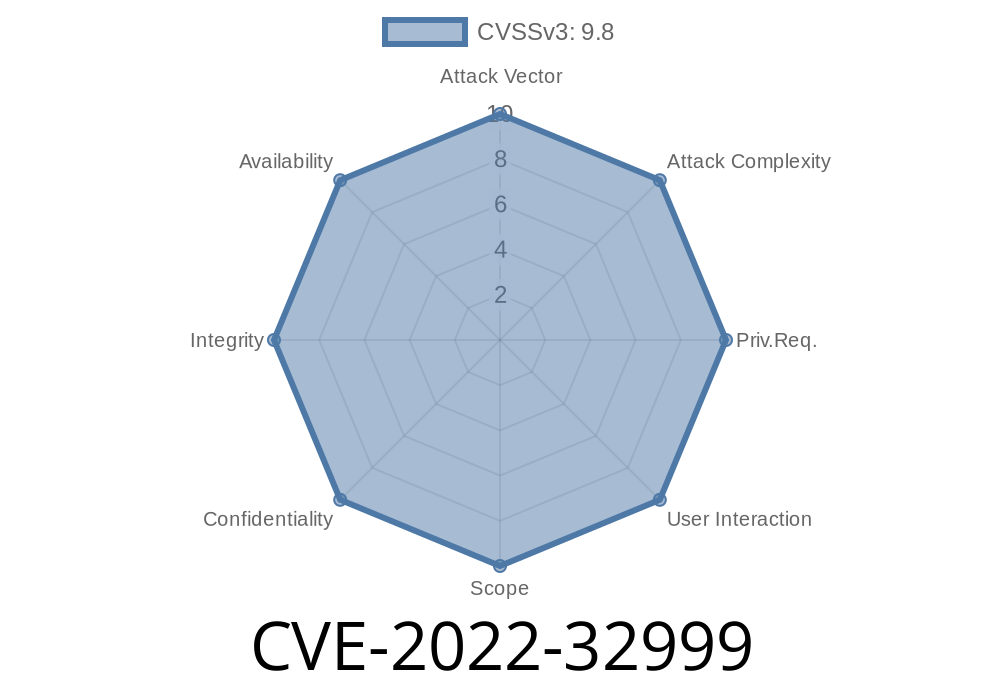
The CVE-2022-32999 vulnerability was found in the cloudlabeling package, which is a Python library for generating metadata for packages. The vulnerability allows attackers to execute code with the privileges of the user running the PyPI client.
Timeline
Published on: 06/24/2022 21:15:00 UTC
Last modified on: 07/05/2022 19:31:00 UTC