Google Chrome is one of the most-used web browsers worldwide, trusted by billions for everything from browsing to online banking. However, even robust software can have vulnerabilities. One such issue was discovered in 2022: CVE-2022-3315, a type confusion bug in Blink, Chrome’s rendering engine. This post breaks down the details, exploit concepts, and offers direct code snippets so even intermediate users can understand what happened.
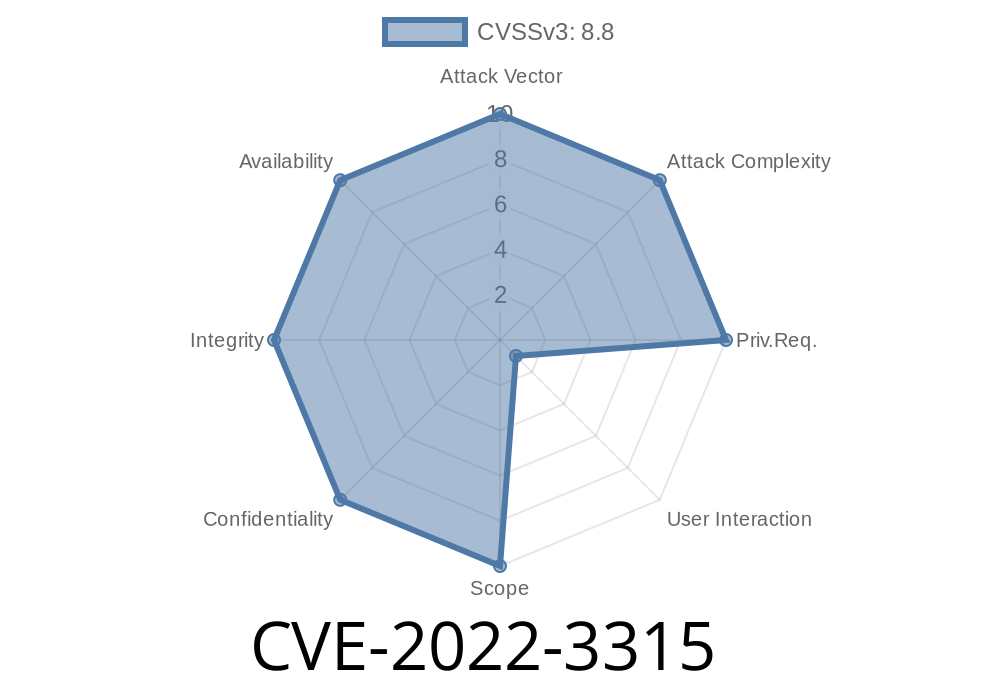
*Severity: Low (but still interesting!).*
What is CVE-2022-3315?
At its core, this is a type confusion vulnerability in the Blink component of Google Chrome versions prior to 106..5249.62. Type confusion means the browser was tricked into treating one kind of object as if it were a different kind, leading to undefined behavior. If properly exploited, this could trigger heap corruption, potentially letting remote attackers crash the browser or execute arbitrary code by getting you to visit a malicious HTML page.
Official advisories:
- Chromium Issue 1359023
- Google Chrome Release Notes
- NVD Entry
How Blink Type Confusion Happens
Consider how JavaScript is handled by a browser. Chrome’s Blink engine manages HTML, CSS, and JS, converting them into visuals and actions. Type confusion bugs often occur when the browser assumes an object is one thing, but a crafty bit of code manipulates it into another.
For CVE-2022-3315, no full public PoC exists (thanks to responsible disclosure) but here’s an abstracted example somewhat similar to the way these vulnerabilities get triggered:
Example Code Snippet
Suppose a hypothetical Blink bug where an element’s internal type is confused after modifying DOM in a tricky way:
<script>
function triggerTypeConfusion() {
let div = document.createElement("div");
document.body.appendChild(div);
// Step 1: Setup with known type
div.setAttribute("id", "test-div");
// Step 2: Rapidly change its structure
div.innerHTML = "<input type='text'>";
// Step 3: Force a reflow and access as a different type
for (let i = ; i < 10000; ++i) {
div.offsetHeight; // force layout recalculation
}
// Step 4: Potential access with wrong assumption about 'div'
div.someBlinkOnlyFunction(); // non-standard, for demonstration
}
triggerTypeConfusion();
</script>
*Note: This is conceptual – the real bug would involve subtle C++ logic in Blink not visible from JavaScript. However, crafted HTML and scripting like above often triggers these bugs.*
Real Exploitation Flow
- Remote exploit potential: An attacker hosts a malicious HTML/JS page, then tricks you into visiting.
The HTML page manipulates DOM elements to confuse the type system in Blink’s internals.
- Heap corruption is triggered, possibly leading to memory disclosure, browser crash, or code execution in rare cases.
Google marked this as low severity because exploiting it beyond a browser crash (DoS) would be tough, thanks to Chrome’s sandboxing and modern mitigations.
How Google Fixed It
The patch for CVE-2022-3315 added better type checks in the relevant Blink source files, making sure internal objects are always treated with their correct types.
You can see reference to the fix in Chromium commit – but source is definitely C++ dense.
Update, update, update. Chrome patched version 106..5249.62 and above.
- Avoid clicking suspicious links or running untrusted HTML/JS in your browser.
References & Further Reading
- NVD Details: CVE-2022-3315
- Chromium Bug 1359023
- Chrome Security Fixes September 2022
- Type Confusion Primer (project Zero)
Summary:
CVE-2022-3315 is a classic example of a “minor” but interesting browser bug: a type confusion in Blink that could corrupt memory when opening a crafted web page. While hard to exploit for anything beyond crashing the browser, it underscores why browser updates matter. If you want to see what goes wrong under the browser hood, study these bugs – they're foundational for browser security research!
Timeline
Published on: 11/01/2022 20:15:00 UTC
Last modified on: 12/08/2022 21:54:00 UTC