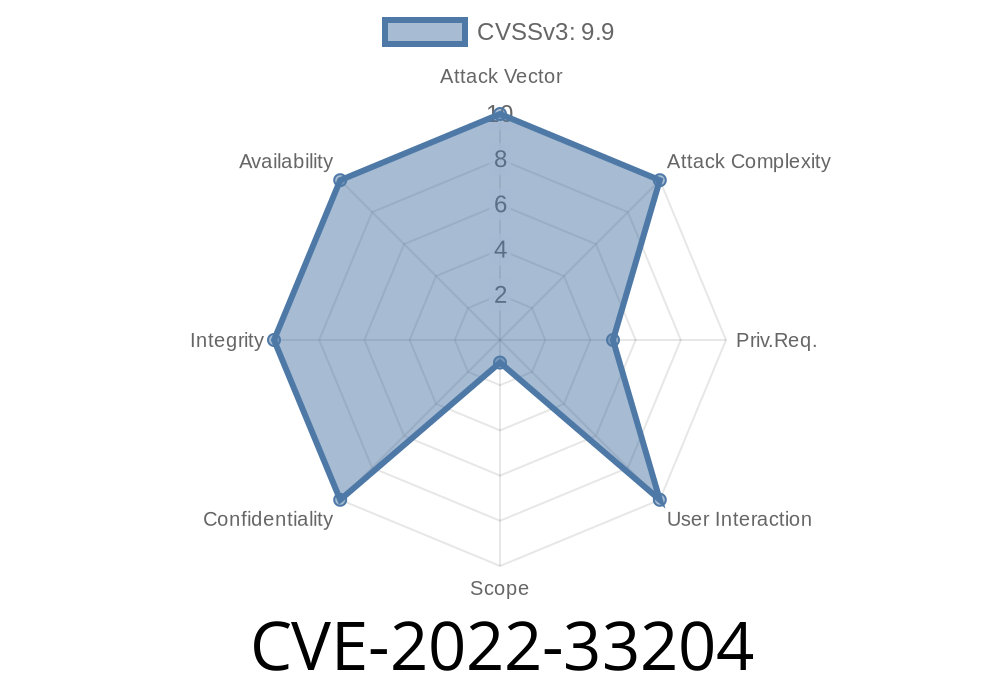
An attacker can send a specially-crafted HTTP request to trigger these vulnerabilities. In order to exploit this vulnerability, the attacker needs to make authenticated HTTP requests to the vulnerable system. The attacker can make authenticated HTTP requests to trigger these vulnerabilities.
An attacker can make authenticated HTTP requests to trigger these vulnerabilities. These vulnerabilities exists in the web interface /wirelessConnect functionality of Abode Systems, Inc. iota All-In-One Security Kit 6.9X and 6.9Z. A specially-crafted HTTP request can lead to arbitrary command execution. An attacker can make an authenticated HTTP request to trigger these vulnerabilities.This vulnerability focuses on the unsafe use of the `ssid_hex` HTTP parameter to construct an OS Command at offset `0x19afc0` of the `/root/hpgw` binary included in firmware 6.9Z.An attacker can send a specially-crafted HTTP request to trigger these vulnerabilities. In order to exploit this vulnerability, the attacker needs to make authenticated HTTP requests to the vulnerable system. The attacker can make authenticated HTTP requests to trigger these vulnerabilities.An attacker can make authenticated HTTP requests to trigger these vulnerabilities. OS Command injection is a type of security vulnerability that allows an attacker to inject commands into the operating system. An attacker can inject commands into a system by sending specially crafted requests to the system.
OS Command Injection is a type of security vulnerability that allows an attacker to inject commands into the operating system. The attacker can inject commands into a system by sending specially crafted requests to the system.
An attacker can make authenticated HTTP requests to trigger these vulnerabilities. These vulnerabilities exist in the web interface /wirelessConnect functionality of Abode Systems, Inc. iota All-In-One Security Kit 6.9X and 6.9Z.
An attacker can make authenticated HTTP requests to trigger these vulnerabilities. OS Command injection is a type of security vulnerability that allows an attacker to inject commands
into the operating system. An attacker can inject commands into a system by sending specially crafted requests to the system.
OS Command injection is a type of security vulnerability that allows an attacker to inject commands into the operating system.
In order to exploit this vulnerability, the attacker needs to make authenticated HTTP requests to the vulnerable system. The attacker can make authenticated HTTP requests to trigger these vulnerabilities.
An attacker can make an authenticated HTTP request to trigger these vulnerabilities.
An attacker can make authenticated HTTP requests to trigger these vulnerabilities. This vulnerability focuses on the unsafe use of the `ssid_hex` HTTP parameter to construct an OS Command at offset `0x19afc0` of the `/root/hpgw` binary included in firmware 6.9Z. An attacker can send a specially-crafted HTTP request to trigger these vulnerabilities by extracting OS Commands from `/root/hpgw`. Abode Systems, Inc.'s iota All-In-One Security Kit 6.9X and 6.9Z have multiple remote exploitable vulnerabilities that attackers could exploit by sending specially crafted HTTP requests
OS Command Injection
OS Command Injection is a type of security vulnerability that allows an attacker to inject commands into the operating system. An attacker can inject commands into a system by sending specially crafted requests to the system. For example, an attack can be performed by sending specially constructed HTTP requests to the vulnerable device.
By crafting an HTTP request, an attacker can send commands and execute arbitrary code on the server. This is typically accomplished with two common methods: exploitation of a buffer overflow vulnerability or exploitation of a command execution vulnerability.
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 10/27/2022 13:24:00 UTC