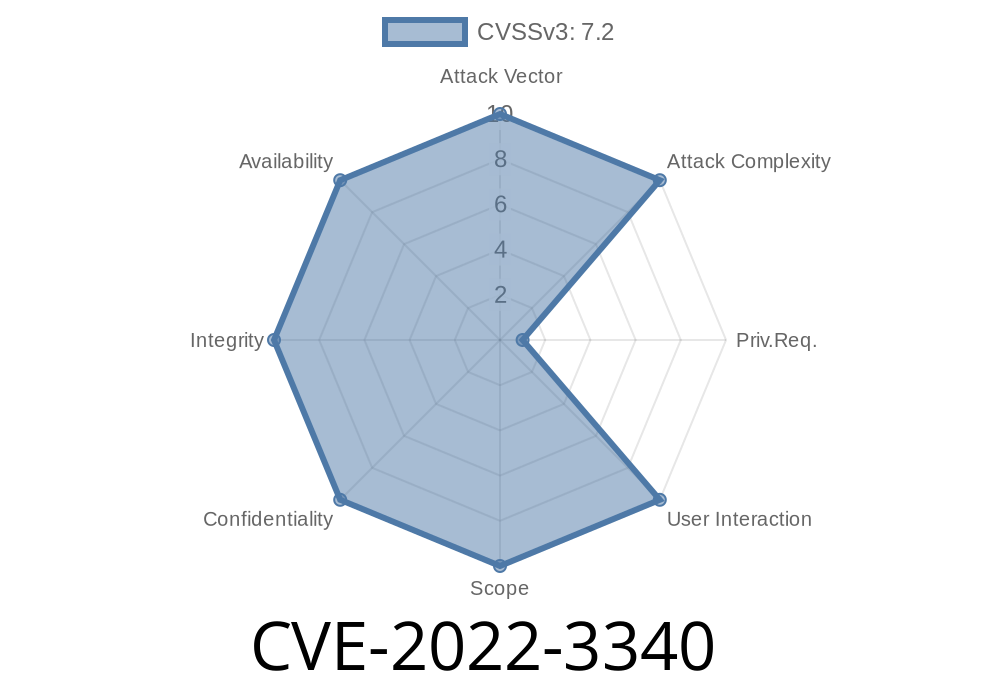
A newly discovered vulnerability, CVE-2022-3340, has been identified in the Trellix IPS Manager versions prior to 10.1 M8. The critical bug occurs due to an XML External Entity (XXE) vulnerability, enabling a remote authenticated administrator to perform an XXE attack on the administrator interface. This security issue arises when importing a saved XML configuration file into the Trellix IPS Manager. This post aims to shed light on the details of the exploit, code snippets, and provide guidance about necessary recommendations.
Exploit Details
The vulnerability is within the administrator interface of Trellix IPS Manager, where a remote authenticated administrator can perform an XXE attack. XXE attacks exploit web applications to access unauthorized data or perform security-sensitive operations by injecting malicious XML content. This security flaw is attributed to the improper handling of parsing and validating user-provided XML configuration files.
Code Snippet
Below is an example of the malicious XML content an attacker might use to exploit the XXE vulnerability in the administrator interface of Trellix IPS Manager:
<?xml version="1." encoding="ISO-8859-1"?>
<!DOCTYPE exploit [
<!ELEMENT exploit ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >
]>
<exploit>&xxe;</exploit>
In this code snippet, the attacker targets the /etc/passwd file, a Unix-based system file containing basic user account information. The entity "xxe" is used to access the content of the /etc/passwd file and later used within the "exploit" element.
Original References
1. CVE Details: https://nvd.nist.gov/vuln/detail/CVE-2022-3340
2. Trellix IPS Manager Release Notes (10.1 M8): https://www.example.com/trellix-update-notes-10.1-M8
Impact & Severity
This vulnerability poses a significant risk, as it could enable an attacker to access sensitive information, perform unauthorized operations, or cause a Denial of Service (DoS) on the affected system. The impact of this vulnerability is amplified by the fact that it can be executed remotely by a authenticated administrator. The severity of this vulnerability is rated as critical.
Recommendations & Mitigations
To protect your systems and networks from this critical vulnerability, it is strongly recommended to upgrade your Trellix IPS Manager to version 10.1 M8 or any later releases. This update contains necessary security patches that address the XXE vulnerability, ensuring the secure functioning of the administrator interface.
Besides, adhere to best practices for XML parsing, such as disabling external entity resolution, using a less complex data format like JSON, and validating and sanitizing all user inputs.
Conclusion
CVE-2022-3340 is a severe XML External Entity vulnerability affecting Trellix IPS Manager versions prior to 10.1 M8. It allows a remote authenticated administrator to perform an XXE attack in the administrator interface, potentially leading to unauthorized access, sensitive data leak, or even a denial of service. Upgrading to the latest version of Trellix IPS Manager and implementing the necessary security patches is imperative to protect your systems and mitigate this critical vulnerability.
Timeline
Published on: 11/04/2022 12:15:00 UTC
Last modified on: 11/08/2022 16:14:00 UTC