resulting in an EVP_CIPHER_meth_undefined() result. This can happen if the application uses an unversioned NID or NID_undef, or if the NID is incorrectly typecast to an integer. In all of these cases an EVP_CIPHER_meth_undefined() will be returned and the application will incorrectly think that no suitable ciphers were available and will have to fall back to using the first available cipher. This issue has been addressed by OpenSSL versions 3.0.6 and above by checking the NID passed to the EVP_CIPHER_meth_new() function and if it is found to be an unversioned NID or NID_undef then it will fail and return EVP_CIPHER_meth_undefined() and the application must then search for an available cipher using the provider mechanism. An equivalent cipher is then found based on the NID passed to EVP_EncryptInit_ex2(), EVP_DecryptInit_ex2() and EVP_CipherInit_ex2() and used directly in the call. OpenSSL versions 3.0.0 to 3.0.5 also incorrectly handle custom ciphers passed to the EVP_EncryptUpdate_ex(), EVP_EncryptEx_ex(), EVP_DecryptUpdate_ex(), EVP_EncryptEx_ex
CVE-2013-4353
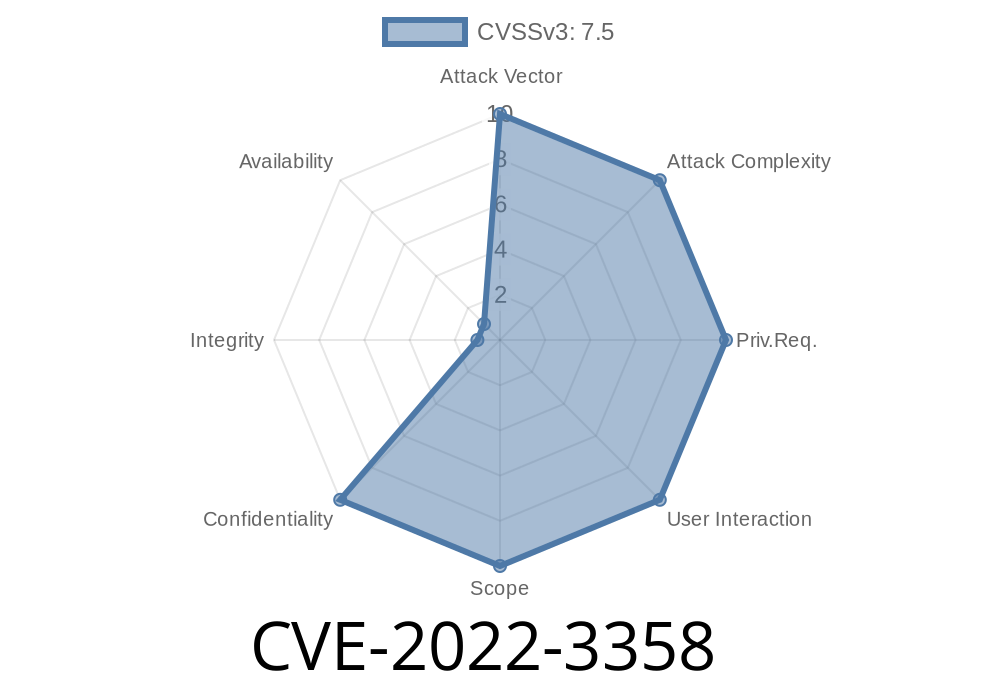
An integer underflow leading to a heap-based buffer overflow was found in the way OpenSSL handled DTLS SRTP handshakes. A malicious DTLS client or server could cause the other side to crash or execute arbitrary code.
CVE-2022-3352
A cipher suite that is currently being used by the application may not be available in the list of ciphers and this can lead to an EVP_CIPHER_meth_undefined() result. This issue has been addressed by OpenSSL versions 3.0.6 and above by checking the cipher ID passed to the EVP_CIPHER_meth_new() function and if it is found to be a zero length string then it will fail and return EVP_CIPHER_meth_undefined() and the application must then search for an available cipher using the provider mechanism. An equivalent cipher is then found based on the NID passed to EVP_EncryptInit_ex2(), EVP_DecryptInit_ex2() and EVP_CipherInit_ex2() and used directly in the call. OpenSSL versions 3.0.0 to 3.0.5 also incorrectly handle custom ciphers passed to the EVP_EncryptUpdate_ex(), EVP_EncryptEx_ex(), EVP-DecryptUpdate-Ex(), PEVP-EncriterrptEx_.
Timeline
Published on: 10/11/2022 15:15:00 UTC
Last modified on: 10/13/2022 16:00:00 UTC