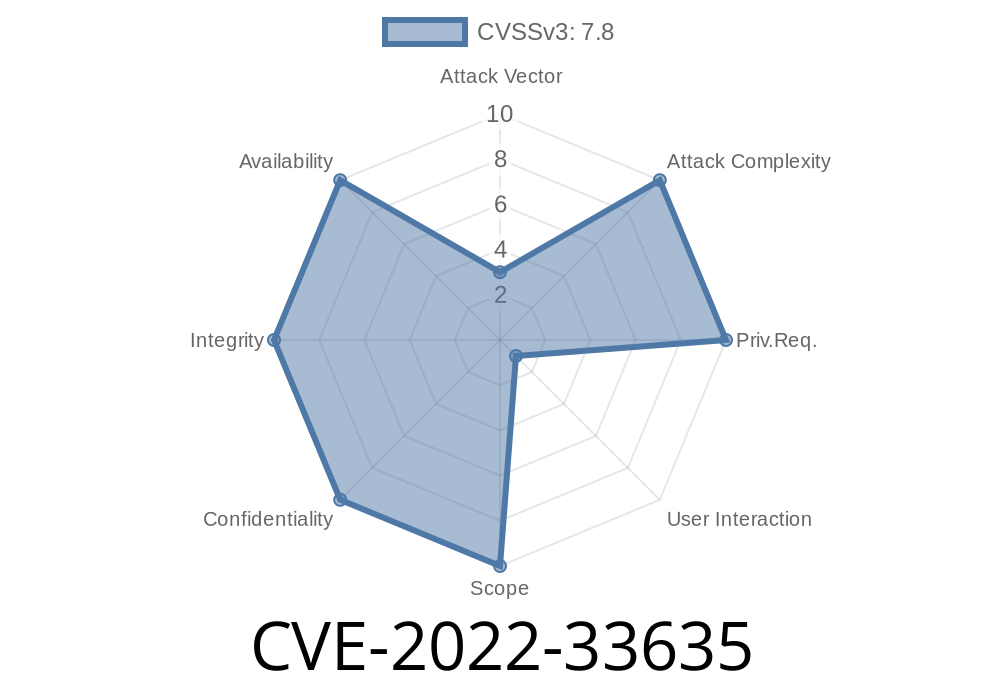
The vulnerability is caused due to improper input validation in Windows GDI+. The attacker can exploit this flaw to execute malicious code in the victims’ system.
To exploit this vulnerability an attacker needs to entice a victim to open malicious email or visit a malicious website. Moreover, the attacker must also have a mal-functioning Windows system on their hand.
How Do Attackers Exploit This Vulnerability?
Attackers are sending emails with specially crafted binary files to get the users to open them.
In addition to this, attackers are also placing specially crafted hyperlinks on webpages to get the users to visit the malicious webpage.
In both the scenarios, attackers are sending the mal-functioning Windows system to the victims.
When the victim opens the malicious email or visits the malicious website, the malicious Windows system is also sent to the victims.
Once the Windows system is received by the victim, the attacker can exploit this vulnerability in the Windows system.
What are the Consequences of Exploiting this Vulnerability?
In case an attacker gains access to the system, they can carry out various actions.
In addition to this, the attacker can also take control of the affected system.
How to protect your system from this Vulnerability?
In order to protect your system from this vulnerability, you need to keep your Windows system updated. Moreover, you also need to keep your Windows system updated.
Windows Update
We recommend that you download and install the latest updates of Windows as soon as they become available.
Once the updates are downloaded, you can proceed to install them.
Only after installing the updates will you be protected from this vulnerability.
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/11/2022 19:16:00 UTC