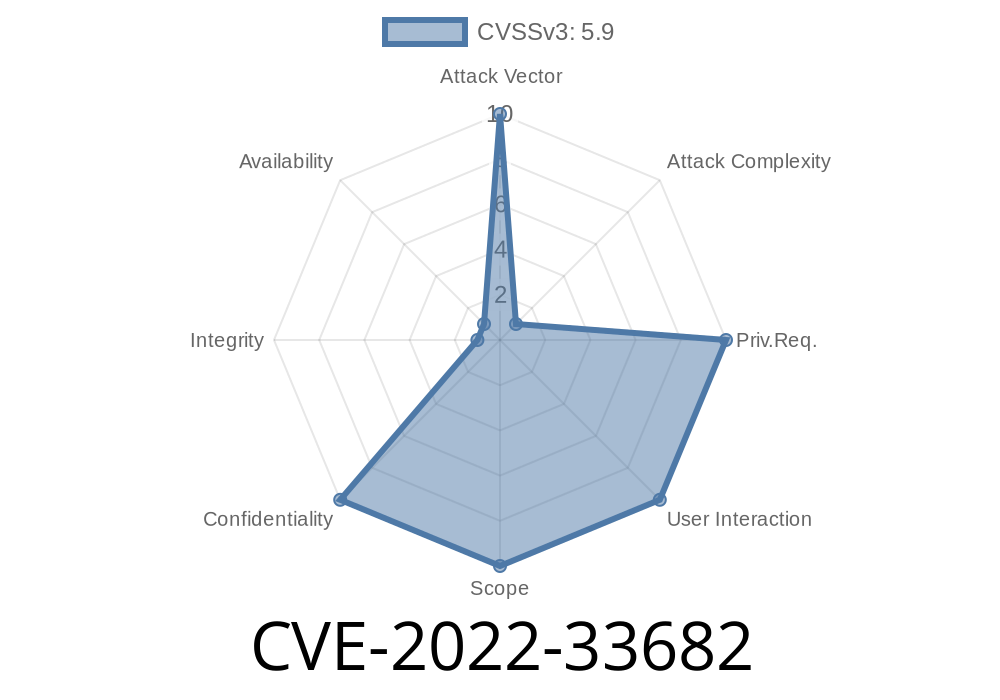
The Apache Pulsar Broker, Proxy, and WebSocket Proxy clients communicate with each other over a secured connection using the pulsar+ssl protocol. The SSL/TLS protocol provides hostname verification, which is the process of verifying that the server with which the client is communicating is the server that the client claims it to be. This prevents man-in-the-middle attacks where an attacker can take control of a communication between the clients and the server and modify the communication to appear to be from the server while in reality being from the attacker. This issue affects the Apache Pulsar Broker, Proxy, and WebSocket Proxy clients, versions 2.7.0 to 2.7.4; 2.8.0 to 2.8.3; 2.9.0 to 2.9.2; 2.10.0; 2.6.4 and earlier.
Description of the Apache Pulsar Broker, Proxy, and WebSocket Proxy
SSL/TLS Protocol Vulnerability
The Apache Pulsar Broker, Proxy, and WebSocket Proxy SSL/TLS protocol implementations do not verify that they are speaking to the server they claim they are. This allows any client connected to the broker’s or proxy’s servers to impersonate any other client and intercept messages intended for the server. This vulnerability affects both secure and non-secure transactions.
How do I fix this issue?
To fix this issue, upgrade the Apache Pulsar Broker, Proxy, and WebSocket Proxy packages in your environment to version 2.7.5 or later, or install and configure the pulsar-ssl-client module for your Apache instance.
Overview of CVE-2022-33682
The Apache Pulsar Broker, Proxy, and WebSocket Proxy clients communicate with each other over a secured connection using the pulsar+ssl protocol in versions 2.7.0 to 2.7.4; 2.8.0 to 2.8.3; 2.9.0 to 2.9.2; 2.10.0; and 2.6.4 and earlier of the Apache Pulsar Broker, Proxy, and WebSocket Proxy clients that are affected by CVE-2022-33682 do not verify the server name in the SSL/TLS protocol during communication between clients and servers which allows man-in-the-middle attackers to spoof the server's certificate for the client's data channel when establishing a secured connection between clients and servers that use this configuration, as demonstrated by an attacker in China who impersonates a legitimate website but is identified as located within China by a client running an application written by a developer from India who has set his proxy settings to allow connections from China.
Timeline
Published on: 09/23/2022 10:15:00 UTC
Last modified on: 09/27/2022 13:23:00 UTC