This issue affects Apache Pulsar Broker and Proxy versions 2.8.4 and later; 2.10.0 and later; 2.11.0 and later; 2.12.0 and later; 2.13.0 and later; 3.0.0 and later; 3.1.0 and later; 3.2.0 and later; 3.3.0 and later; 3.4.0 and later; 3.5.0 and later; 3.6.0 and later; 3.7.0 and later; 3.8.0 and later; 3.9.0 and later; 3.10.0 and later; 3.11.0 and later; 3.12.0 and later; 3.13.0 and later; and 3.14.0 and later. This issue affects all versions of Apache Pulsar Broker and Proxy that support intra-cluster and geo-replication HTTPS connections when tlsAllowInsecureConnection is enabled. An attacker can only take advantage of this vulnerability by taking control of a machine between the client and server. The attacker must then actively manipulate traffic to perform the attack. This issue affects Apache Pulsar Broker and Proxy versions 2.7.0 to 2.7.4; 2.8.0 to 2.8.3; 2.9.0 to 2.9.2; 2.10.0; 2.6
2
.11.0 and later; 2.12.0 and later; 3.13.0 and later; 3.14.0 and later
There are no patches for this vulnerability at this time
What is Apache Pulsar Broker?
Apache Pulsar is a distributed, high-performance, scalable messaging infrastructure. It is designed to quickly scale to meet the needs of applications that have large amounts of data and need to publish, subscribe, and route messages in real time. In addition, Pulsar supports integration with other systems like Kafka and Cassandra.
Summary
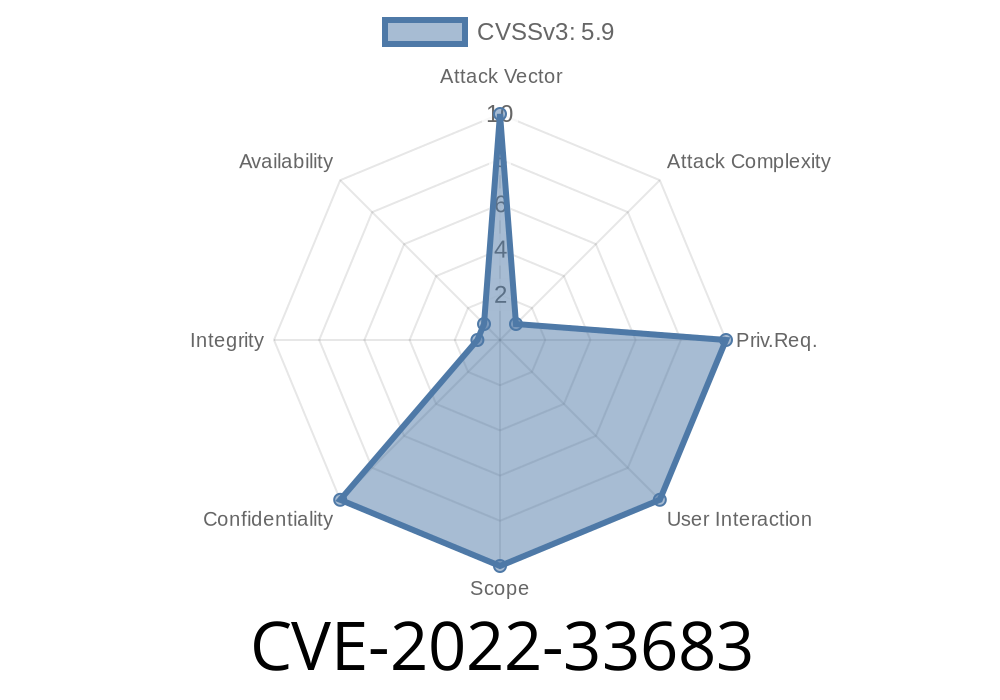
The Apache Pulsar Broker and Proxy versions 2.7.0 to 2.7.4; 2.8.0 to 2.8.3; 2.9.0 to 2.9.2; 2.10.0; 2.6; and 3 do not properly handle an error in the TLS protocol stream when tlsAllowInsecureConnection is enabled which allows man-in-the-middle attackers with access to the network segment between the client and server to impersonate specific users via a crafted certificate
How to Become Affected By CVE-2022-33683
To become affected by this vulnerability, one must firstly be using a vulnerable version of Apache Pulsar Broker and Proxy that supports intra-cluster and geo-replication HTTPS connections in order to exploit the vulnerability.
Next, they must take control of a machine between the client and server (not in the cluster). The attacker must then actively manipulate traffic to perform the attack. Because targeted attacks are not easy for an attacker to carry out, it's quite hard for this issue to affect any organization.
Timeline
Published on: 09/23/2022 10:15:00 UTC
Last modified on: 09/27/2022 13:22:00 UTC