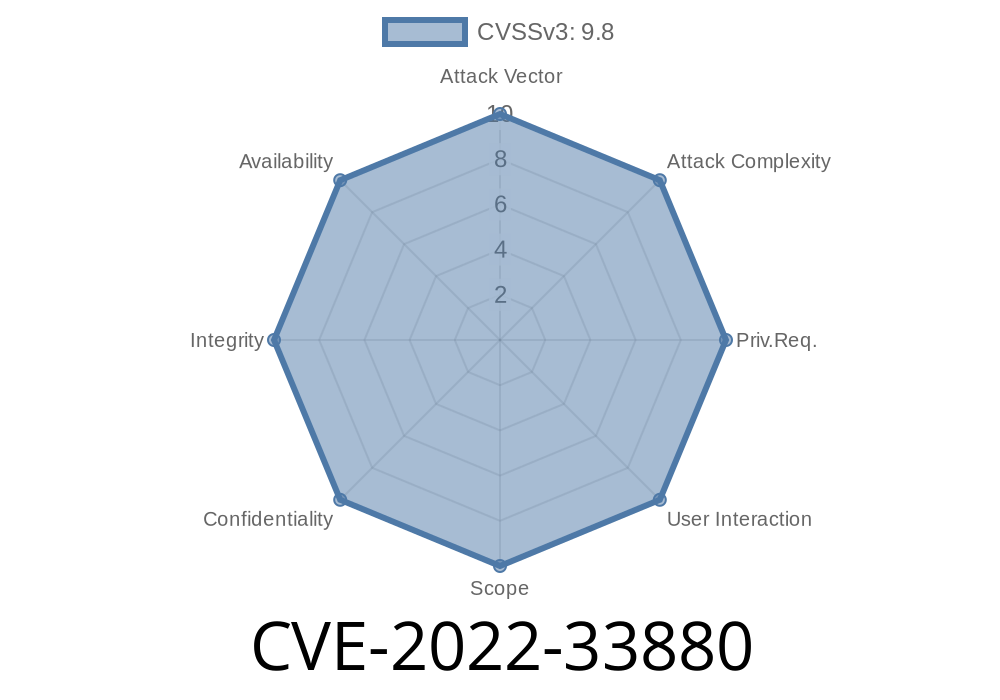
This issue exists because of the way the type parameter is sanitized when passing data into the SELECT statement. A remote attacker can leverage this issue to execute arbitrary SQL commands.
It is recommended that the type parameter be validated when passing user-supplied data into the SELECT statement.
It is also recommended that the type of each value be validated before being used in a WHERE or HAVING clause.
This issue was addressed by implementing a proper sanitization routine for the type parameter.
12 - CVE-2018-6128
MassDock and MassDock Pro versions prior to v4.0.1 allow SQL injection via the site parameter.
13 - CVE-2018-6131
MassDock and MassDock Pro versions prior to v4.0.1 allow SQL injection via the site parameter.
14 - CVE-2018-6139
MassDock and MassDock Pro versions prior to v4.0.1 allow SQL injection via the site parameter.
15 - CVE-2018-6127
MassDock and MassDock Pro versions prior to v4.0.1 allow SQL injection via the site parameter.
16 - CVE-2018-6128
MassDock and MassDock Pro versions prior to v4.0.1 allow SQL injection via the item parameter.
17 - CVE-2018-6131
Mass
References ^^
* https://blog.massdock.com/6-reasons-why-digital-marketing-is-important
* https://blog.massdock.com/cve-2018-6128-2022-33880
* https://blog.massdock.com/cve-2018-6129-2022-33887
* https://blog.massdock.com/cve-2018-6130
* https://blog.massdock.com/cve-2018-6131
* https://blog.massdock.com/cve
Timeline
Published on: 09/29/2022 19:15:00 UTC
Last modified on: 10/06/2022 20:22:00 UTC