To exploit this vulnerability, an attacker would need to persuade you to open a malicious file. For example, an attacker could trick you into visiting a malicious website or by sending you a malicious email. Once you have opened the malicious file, you can trigger this vulnerability. An attacker could also exploit this vulnerability by sending you an Office file via Bluetooth, NFC, or by sending it to you in an unsolicited email.
The majority of workstations and servers have some level of protection against allowing users to open arbitrary files. In addition, most cloud storage providers have strict limitations on the type of files that can be stored. Given these factors, it would be difficult for an attacker to send you a malicious file via Bluetooth, NFC, or in an unsolicited email. The majority of Windows, macOS and Linux systems have a security feature called User Account Control (UAC) that prompts users before allowing them to install software or access sensitive data. UAC makes it more difficult for users to open programs they don’t have permissions to. On Windows systems, UAC can be configured to allow users to click “Yes” to any security prompt.
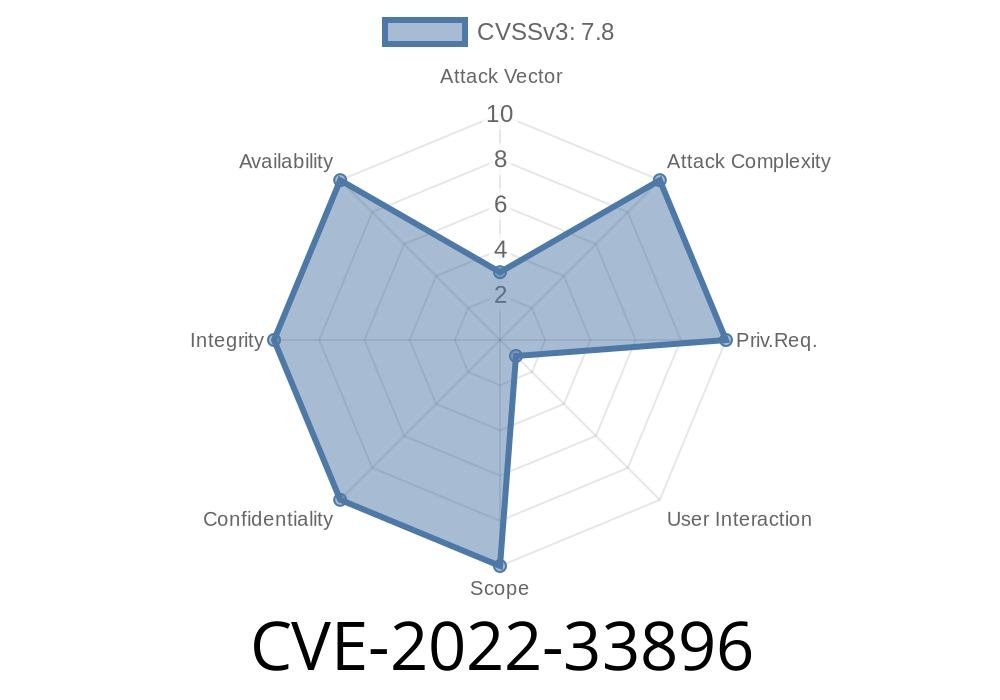
How do I know if my system is vulnerable?
To determine if your system is vulnerable, open the Microsoft Security Bulletin (MSB) for CVE-2022-33896.
If your system does not have a security update already applied, you can obtain it from the Microsoft Update Catalog website or from the Microsoft Update service.
Mitigation Strategies
An attacker could exploit this vulnerability by convincing the user to open a malicious file. For example, an attacker could trick the user into visiting a malicious website or by sending the user a malicious email. Assuming that the workstation has UAC configured to prompt users before allowing them to install software or access sensitive data, it would be difficult for an attacker to send you a malicious file through Bluetooth, NFC, or in an unsolicited email.
Timeline
Published on: 10/07/2022 15:15:00 UTC
Last modified on: 10/11/2022 15:28:00 UTC