In addition, a new kernel security feature was introduced in this release to protect against these attacks. The new feature, known as “SMRAM protection”, prevents SMRAM from being written to by a malicious application. Note that due to the way in which the SMRAM is accessed by Intel® NVS components, SMRAM protection will not work for validated applications that use the Intel NVS components for DMA. As a result, in order to protect against DMA attack, validated applications must use the new feature known as “SMRAM protection”. The new feature, known as “SMRAM protection”, prevents SMRAM from being written to by a malicious application. Note that due to the way in which the SMRAM is accessed by Intel NVS components, SMRAM protection will not work for validated applications that use the Intel NVS components for DMA. As a result, in order to protect against DMA attack, validated applications must use the new feature known as “SMRAM protection”. As a best practice, validated software should not use the Intel NVS component for DMA if it is not required. This will reduce the risk of DMA attack.
Strengthen the System Integrity Protection
Intel NVS components cannot be used for DMA attacks because of the new feature, known as “SMRAM protection”.
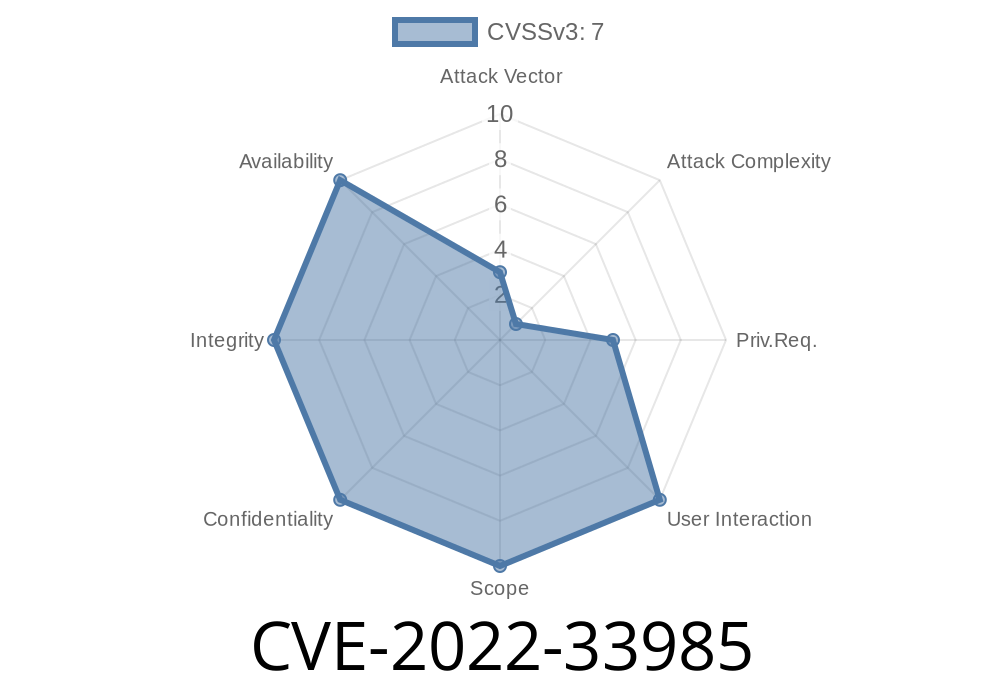
This release also includes a number of other security improvements to protect against vulnerabilities such as the "CVE-2022-33985" vulnerability, which is described in detail in the Security Update Guide (Version 20).
Install the SLPK and STPM updates on your systems
Security updates are a vital part of the latest Intel Security Patch Tuesday release. The latest releases includes Intel Advanced Threat Protection (Intel ATP) software, which provides additional protection to help detect and prevent attacks and intrusions.
The following security updates are available:
- Intel NCSI Update SLPK - Software Local Kernel Extension (SLPK) update
- Intel NCSI Update STPM - Software Test and Measurement Package (STPM) update
- Small Business Technology Protection Program (S-BTP) update
- Microsoft Windows* OS patch
Intel® Software Guard Extensions (SGX)
The new operating system version also includes a new feature known as “Intel Software Guard Extensions (SGX)”. The SGX feature provides a safe environment for applications to store sensitive data and run untrusted code. This can be used by applications to help create a secure sandbox in which they can run untrusted code.
New Features Introduced in Intel® NVDIMM-N Sch-Atm-DIMM
The new release of Intel® NVDIMM-N Sch-Atm-DIMM (SMRAM) includes the following new features:
A new kernel security feature that prevents SMRAM from being written to by a malicious application. This is achieved by the “SMRAM protection” feature which was introduced in this release. Note that due to the way in which the SMRAM is accessed by Intel NVS components, SMRAM protection will not work for validated applications that use the Intel NVS components for DMA. As a result, in order to protect against DMA attack, validated applications must use the new feature known as “SMRAM protection”.
A new feature involving Error Corrections Code (ECC) calculation speed improvement on Intel Core™ i7 vPro processors.
Note that this release does not include any changes to ECC calculation speed on other processor families or platforms.
How to identify a vulnerable VM?
To identify a vulnerable VM, run the following command:
psrset -o efi-vendor
If the value returned is "Intel", then the system is vulnerable to an EFI DMA attack. Note that this vulnerability applies to all systems running on Intel processors.
Timeline
Published on: 11/15/2022 00:15:00 UTC
Last modified on: 11/17/2022 22:18:00 UTC