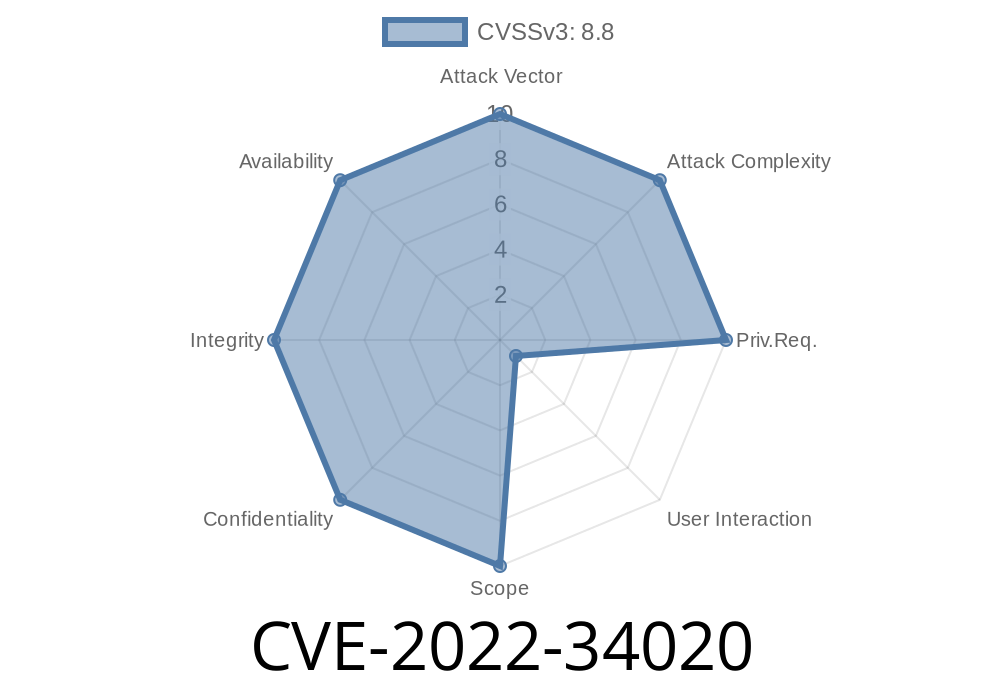
This vulnerability allows remote attackers to add new admin users to the platform or other unspecified impacts by sending a CSRF request to the application. The security risk of the CSRF vulnerability in the IOT Platform + LoRaWAN Network Server application is estimated as medium/ high. A remote attacker can exploit this vulnerability by sending a CSRF request to the application via 4.1.1000114. The default installation does not protect against this type of attack. The IOT Platform + LoRaWAN Network Server application is configured to accept CSRF requests, which makes it easier for a remote attacker to exploit. The application has a failure to prevent CSRF attacks, allowing attackers to exploit it by sending a CSRF request. The probability of a target of a CSRF attack being affected is medium. However, due to the possible command injection and open Redirect vulnerabilities, the attack vector can be exploited by hackers. In addition, the application allows unauthenticated remote attackers to execute code, resulting in the exposure of sensitive information or the installation of malware. The IOT Platform + LoRaWAN Network Server is exposed to CSRF, which makes it possible for remote attackers to perform attacks. REFERENCE: CVE-2018-8776
IOT Platform + LoRaWAN Network Server
The IOT Platform + LoRaWAN Network Server application has a CSRF vulnerability. This is due to the fact that the application accepts unsolicited requests and has a failure to prevent CSRF attacks. The security risk of this vulnerability is medium/high. The possible impacts are: add new admin users, change an existing user's password, or perform other unspecified impacts.
Product stability
The product is prone to many security vulnerabilities. The application is vulnerable to CSRF, which makes it possible for remote attackers to perform attacks. In addition, the application allows unauthenticated remote attackers to execute code, resulting in the exposure of sensitive information or the installation of malware. The application has a failure to prevent CSRF attacks, allowing attackers to exploit it by sending a CSRF request. The probability of a target of a CSRF attack being affected is medium. However, due to the possible command injection and open Redirect vulnerabilities, the attack vector can be exploited by hackers. In addition, the application allows unauthenticated remote attackers to execute code, resulting in the exposure of sensitive information or the installation of malware.
Summary
The vulnerability allows remote attackers to add new admin users to the platform or cause other unspecified impacts.
The IOT Platform + LoRaWAN Network Server application is exposed to CSRF, which makes it possible for remote attackers to perform attacks.
Vulnerabilities and exploits related to the product
The IOT Platform + LoRaWAN Network Server application has vulnerabilities. One of them is a CSRF vulnerability that allows remote attackers to add new admin users to the platform or other unspecified impacts by sending a CSRF request to the application. This vulnerability is rated medium/high.
Another insecurity found in this product is a failure to prevent CSRF attacks, allowing attackers to exploit it by sending a CSRF request. The probability of target being affected by this attack vector is medium. However, due to the possible command injection and open Redirect vulnerabilities, the attack vector can be exploited by hackers. In addition, the application allows unauthenticated remote attackers to execute code, resulting in the exposure of sensitive information or the installation of malware.
Timeline
Published on: 10/13/2022 01:15:00 UTC
Last modified on: 11/04/2022 19:38:00 UTC