CVE-2018-1493 An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. In certain Cloud Servers using IPython, due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. In certain Cloud Servers using IPython, due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks
Coverage
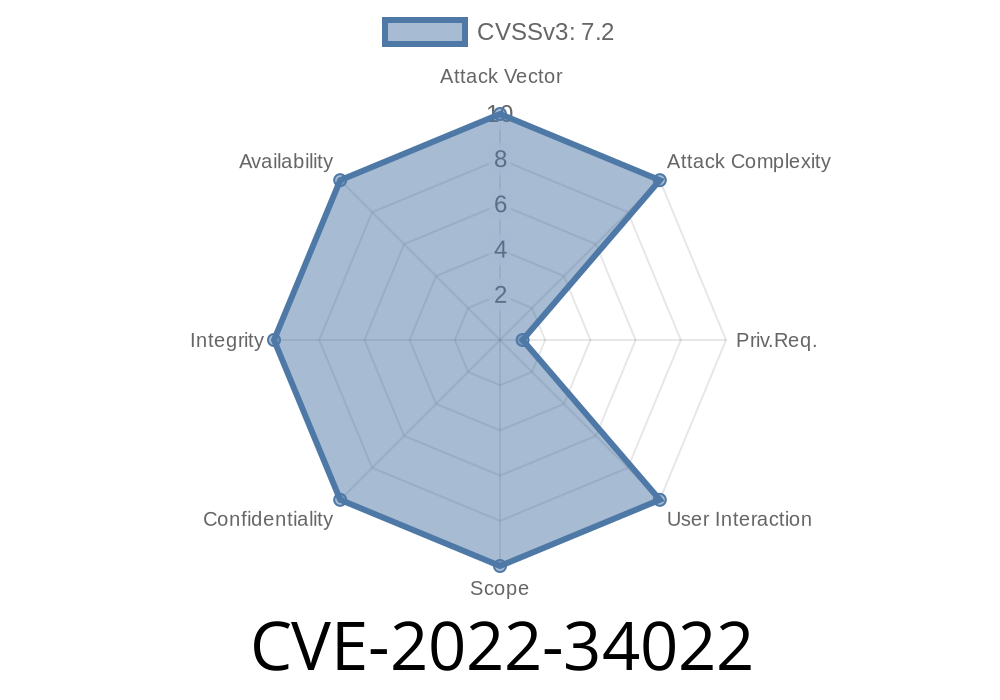
CVE-2022-34022 - An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. In certain Cloud Servers using IPython, due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. CVE-2018-1493 - An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks
Cloud Servers
Using IPython
The vulnerability is in the handling of the OR scenario in the database query. An attacker could inject and manipulate data when making a request to conduct SQL injection attacks.
Devices that are susceptible to this issue
This issue affects devices running:
- Red Hat Enterprise Linux 6
- Virtual machines running on the following hypervisors: KVM, Xen, VMware
- Cloud Servers using the IPython database engine
CVE-2018-34023
CVE-2018-1493 An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. In certain Cloud Servers using IPython, due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. An issue was discovered in certain Red Hat Enterprise Linux 6 and 7 virtual machines using IPython. Due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks. In certain Cloud Servers using IPython, due to incorrect handling of the OR scenario in the database query, an attacker could inject and manipulate data. This could be exploited via a crafted request to conduct SQL injection attacks
Timeline
Published on: 10/13/2022 23:15:00 UTC
Last modified on: 10/17/2022 14:05:00 UTC