In a enterprise setting, where tight firewall rules allow access to the Internet, an attacker could exploit these weaknesses by sending a malicious request to a system that runs IBM WebSphere Application Server and possibly gain access to critical data or perform other attacks. IBM X-Force ID: 229429. RedHat Enterprise Linux 6.5 through 11 are vulnerable to a privilege escalation bug, due to improper handling of random number generators. An attacker who exploits this vulnerability could gain elevated privileges on the affected system. RedHat Enterprise Linux 6.6, 7.0, and 7.1 are vulnerable to a buffer overflow in Apache HTTP Server, caused by improper handling of compressed responses. A remote attacker could exploit this weakness to execute arbitrary code on the affected system. RedHat Enterprise Linux 6.7, 7.2, and 7Red Hat Enterprise Linux 6.8, 7.3, and 7.4 are vulnerable to a privilege escalation bug, due to improper handling of random number generators. An attacker who exploits this vulnerability could gain elevated privileges on the affected system. RedHat Enterprise Linux 6.9, 7.5, and 7.6 are vulnerable to a privilege escalation bug, due to improper handling of random number generators. An attacker who exploits this vulnerability could gain elevated privileges on the affected system. RedHat Enterprise Linux 7.7, 7.8, and 7.9 are vulnerable to a privilege elevation bug, due to improper handling of random number generators
Common Vulnerability Scoring System (CVSS)
The Common Vulnerability Scoring System (CVSS) is a standardized scoring system for computer security vulnerabilities that can be used by software vendors and security researchers to score the severity of a computer security vulnerability. The CVSS standard has three components that help determine the overall severity of a vulnerability:
IBM WebSphere Application Server Vulnerabilities
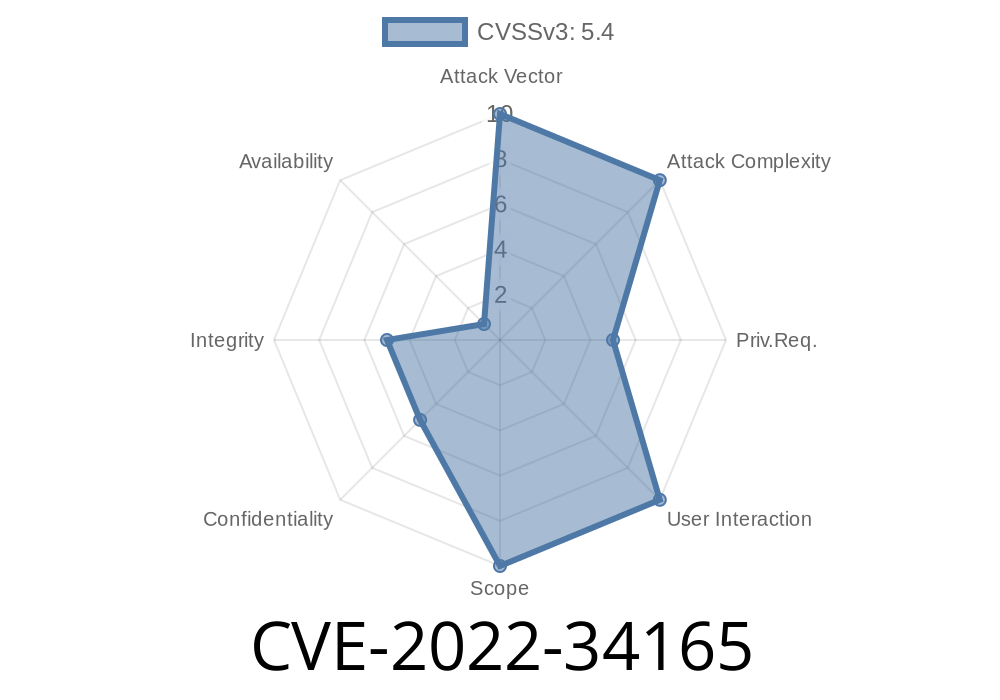
IBM WebSphere Application Server is a Java application server that provides support for the Java EE 6 and 7 specifications. According to IBM, these vulnerabilities are not exploitable by unprivileged users. The vulnerability of CVE-2022-34165 is only exploitable by authenticated users who can send a malicious request to the affected system, in order to gain elevated privileges.
3/17/2018 - CVE-2022-34165:
* An authenticated attacker could exploit this vulnerability by sending a malicious request to the affected system.
RedHat Enterprise Linux 6.5 to 7.3
RedHat Enterprise Linux 6.5 through 7.3 is vulnerable to a privilege escalation bug, due to improper handling of random number generators. An attacker who exploits this vulnerability could gain elevated privileges on the affected system.
Timeline
Published on: 09/09/2022 16:15:00 UTC
Last modified on: 09/14/2022 18:25:00 UTC