This has been fixed in these versions. Apache Tomcat 9.0.0-M1, 8.5.0-8, 8.0.18, 7.x versions and earlier are vulnerable.
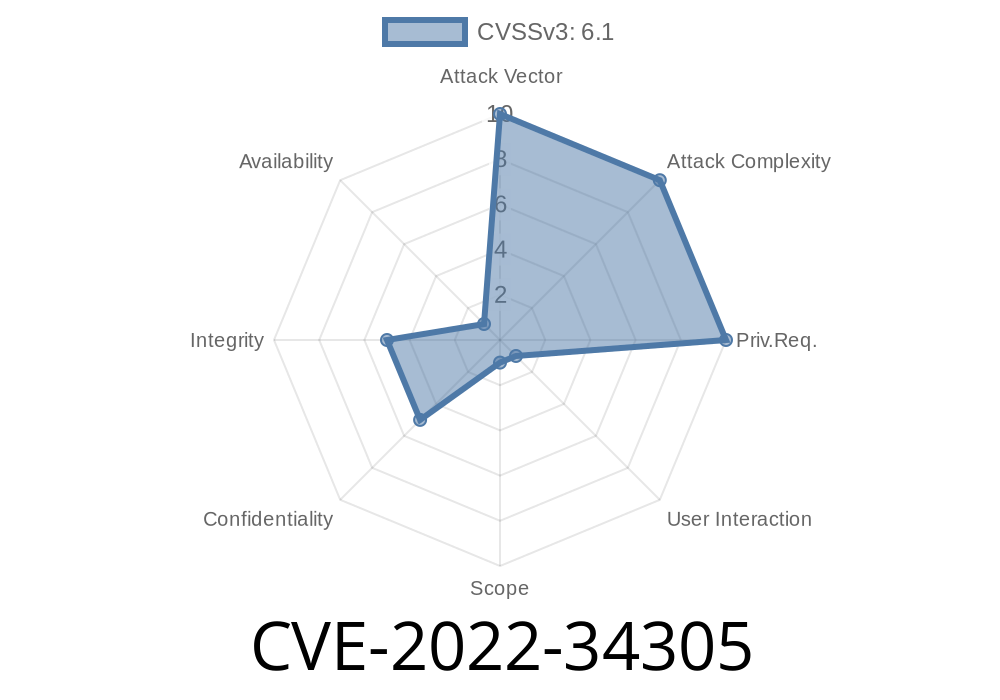
An attacker can inject arbitrary JavaScript into the request path using an insecurelyFormed request such as GET /?user=%{http_user_input} . Apache Tomcat does not sanitize the user input before sending it to the backend. This could lead to a Cross-site scripting (XSS) attack.
An attacker could exploit this vulnerability to conduct a XSS attack against a system or application that handles user input.
Apache Tomcat does not restrict access to administrator-configured applications. This may lead to Cross-site request forgery (CSRF) attacks.
Apache Tomcat does not enforce the HTTP Methods that are allowed on resources. This may lead to Cross-site request forgery (CSRF) attacks.
Apache Tomcat does not perform request filtering. This may lead to Cross-site request forgery (CSRF) attacks.
Apache Tomcat does not limit the number of requests that can be sent per minute. This may lead to Denial of service (DoS) attacks.
An exploit of this vulnerability requires no authentication. An attacker would only need to submit a request to the vulnerable system.
What is Apache Tomcat and how does it help us?
Apache Tomcat is a free, open-source software implementation of the Java Servlet and JavaServer Pages (JSP) technologies. It was originally developed by Apache Software Foundation for use on the Apache HTTP Server, but is now used by many other web servers and application servers.
Tomcat is used in many high-profile websites such as Facebook, Wikipedia, Google, Twitter and PayPal.
What is Apache Tomcat?
Apache Tomcat is an open-source software implementation of the Java Servlet and JavaServer Pages (JSP) technologies for servlet-based web applications. It is primarily developed by Apache Software Foundation.
Apache Tomcat is used to serve dynamic web content via HTTP and HTTPS, as well as providing common functionality for those who want to build a single-tier or multi-tiered integration between Java and HTTP servers.
Tomcat runs on most operating systems using a variety of implementations including the original code from Apache, JBoss, Microsoft Windows Server 2003 with IIS 5.0 or later, IBM WebSphere 7.0 with HTTP Dynamic Server or later, Novell NetWare 6.5 SP2 or later, Red Hat Enterprise Linux AS 4+, SuSE Linux 9+ or 10+, and Sun Microsystems Solaris 10+.
Timeline
Published on: 06/23/2022 11:15:00 UTC
Last modified on: 08/21/2022 05:15:00 UTC