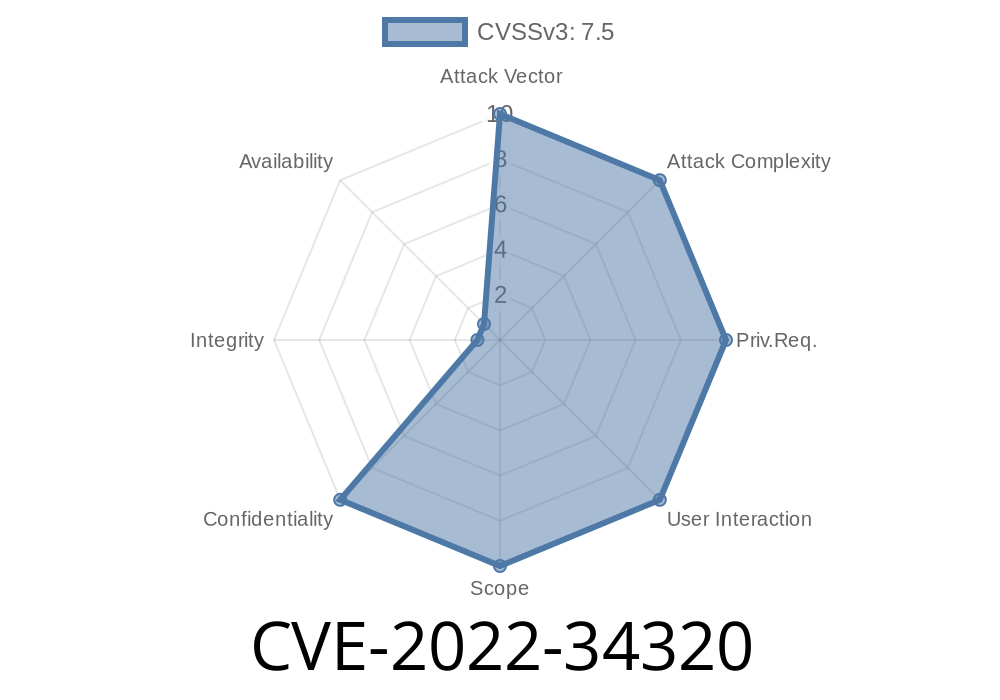
This weakness exists in the Message Send Protocol (MSP) of the CICS Transaction Server (TS) software. The MSP is used to transfer data between CICS processes, such as when you send a message from one process to another. If exploited, this weakness could allow an attacker to read or modify data in other CICS processes that are using the MSP. An attacker would have to be on the same network as the affected process in order to exploit this weakness.
Overview of CVE-2022-34320
CICS Transaction Server (TS) software is a component of CICS that manages data in a transaction processing environment. It consists of many components, including the Message Send Protocol (MSP) component. The MSP component is used to transfer data between CICS processes, such as when you send a message from one process to another. If exploited, this weakness could allow an attacker to read or modify data in other CICS processes that are using the MSP. An attacker would have to be on the same network as the affected process in order to exploit this weakness.
CVE-2023-34325
This weakness exists in the Message Send Protocol (MSP) of the CICS Transaction Server (TS) software. The MSP is used to transfer data between CICS processes, such as when you send a message from one process to another. If exploited, this weakness could allow an attacker to read or modify data in other CICS processes that are using the MSP. An attacker would have to be on the same network as the affected process in order to exploit this weakness.
Details
The vulnerability is present in the Message Send Protocol (MSP) of the CICS Transaction Server (TS) software. The MSP is used to transfer data between CICS processes, such as when you send a message from one process to another. If exploited, this weakness could allow an attacker to read or modify data in other CICS processes that are using the MSP. An attacker would have to be on the same network as the affected process in order to exploit this weakness.
Timeline
Published on: 11/14/2022 20:15:00 UTC
Last modified on: 11/16/2022 19:25:00 UTC