Microsoft. This issue affects all Windows 10 versions, from the Creators Update (version 1703) onwards. At the moment, it is unknown how frequently these attacks occur for each version of Windows and for each driver. When it happens, data corruption can occur in a variety of ways and cause a variety of issues from unbootable systems to unexpected behaviour. The issue has been assigned the following reference ID: CVE-2018-8789. It is important to note that in order for this issue to occur, a DMA attacker must control both the DMA source and DMA destination in a Windows system. This means that the issue can happen for any DMA driver (not just the Storage Security commandDxe driver). At the moment, it is unknown how frequently these attacks occur for each version of Windows and for each driver. When they happen, data corruption can occur in a variety of ways and cause a variety of issues from unbootable systems to unexpected behaviour. The issue has been assigned the following reference ID:It is important to note that in order for this issue to occur, a DMA attacker must control both the DMA source and DMA destination in a Windows system. This means that the issue can happen for any DMA driver (not just the Storage Security commandDxe driver). How to determine if your system is vulnerable: The easiest way to determine if your system is vulnerable to this issue is by installing any DMA-targeted driver, such as Storage Security
Storage Security command Dxe driver
Storage Security command Dxe driver
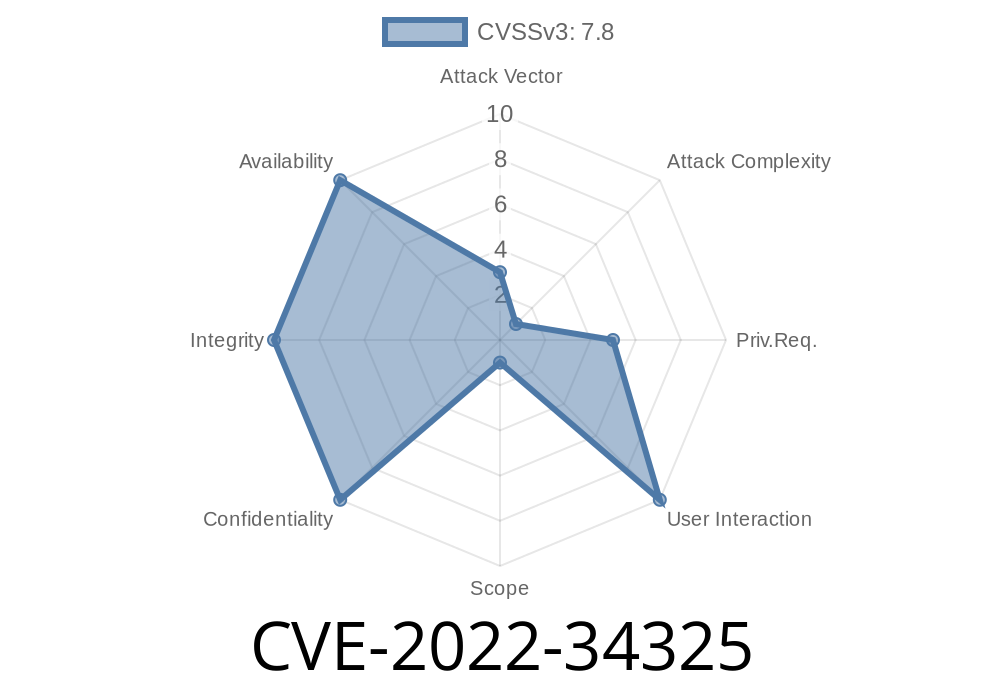
Intel. This issue affects all Intel processors from the Ivy Bridge generation onwards. At the moment, it is unknown how frequently these attacks occur for each processor. When it happens, data corruption can occur in a variety of ways and cause a variety of issues from unbootable systems to unexpected behaviour. The issue has been assigned the following reference ID:CVE-2022-34325. It is important to note that in order for this issue to occur, a DMA attacker must control both the DMA source and DMA destination in a Windows system. This means that the issue can happen for any DMA driver (not just the Storage Security commandDxe driver). At the moment, it is unknown how frequently these attacks occur for each processor. When they happen, data corruption can occur in a variety of ways and cause a variety of issues from unbootable systems to unexpected behaviour. The issue has been assigned the following reference ID:It is important to note that in order for this issue to occur, a DMA attacker must control both the DMA source and DMA destination in a Windows system. This means that the issue can happen for any DMA driver (not just the Storage Security commandDxe driver). How to determine if your system is vulnerable: The easiest way to determine if your system is vulnerable to this issue is by installing any DMA-targeted device such as an Intel® SSD or Optane™ SSD attached via PCI Express
Microsoft Windows 10 Device Management Framework Overview
The Microsoft Windows 10 Device Management Framework provides a flexible, extensible architecture that is designed to make it easy to customize the device management experience. It supports multiple methods of provisioning and managing devices, including on-premises systems such as Intune and MDM server deployments with System Center Configuration Manager (SCCM) and Mobile Device Management (MDM) solutions.
Windows 10 Device Management also encompasses the role of Cloud Service Providers (CSPs), who help enterprises meet their business goals by providing Windows 10 device provisioning services in the cloud. This architecture enables partner technologies to be used together at scale without sacrificing flexibility or control.
Microsoft Windows Storage Security command DMA Arbitrary Code Execution Vulnerability
DMA stands for Direct Memory Access. It's the method by which a program can directly access or read/write data in memory without involving the processor. The issue with this driver is that it uses DMA to perform operations on any file, regardless of whether the system has permissions to access that file. This means that an attacker could use this issue to gain control of a system even if there are no open SMB shares or other services running on the system. At the moment, it is unknown how frequently these attacks occur for each version of Windows and for each driver. When they happen, data corruption can occur in a variety of ways and cause a variety of issues from unbootable systems to unexpected behaviour. The issue has been assigned the following reference ID: CVE-2018-8789 . It is important to note that in order for this issue to occur, a DMA attacker must control both the DMA source and DMA destination in a Windows system. This means that the issue can happen for any DMA driver (not just Storage Security).
How to determine if your system is vulnerable: The easiest way to determine if your system is vulnerable to this issue is by installing any DMA-targeted driver, such as Storage Security commandDxe.
Storage Security commandDxe driver
When a driver is installed, Windows will automatically scan the device for any DMA-targeted drivers. If it detects a DMA-targeted driver, the system will warn that an issue has been found.
How do I know if my system is vulnerable?
The easiest way to determine if your system is vulnerable to this issue is by installing any DMA-targeted driver, such as Storage Security commandDxe. If you install the driver, then a DMA exploit may occur. The easiest way to check for the presence of an issue is by booting into Safe Mode or disabling the driver.
You can also use Driver Verifier in Windows 10 to ensure that no issues have been introduced with installed drivers during their installation process.
Timeline
Published on: 11/14/2022 23:15:00 UTC
Last modified on: 11/17/2022 21:02:00 UTC