The researcher discovered that it is possible to execute arbitrary PHP code on the server. Stored application credentials may be accessed. The security issue has been classified as critical. The fix has been released by the vendor. It is highly recommended to upgrade the software if possible. End user are advised to monitor the process carefully. Any suspicious activity should be reported to the vendor. Next details on how to prevent the attack. To stay protected, users need to be careful when inputting data.
In addition, users should avoid clicking suspicious links. It is also recommended to update the software to the latest release. Doing so will help to protect the system from possible attacks. End users are encouraged to contact the vendor for any help. End users that have any questions may contact us for assistance.
CVE-2021-3433
The researcher discovered that it is possible to execute arbitrary PHP code on the server. Stored application credentials may be accessed. The security issue has been classified as moderate. The fix has been released by the vendor. It is highly recommended to upgrade the software if possible. End user are advised to monitor the process carefully. Any suspicious activity should be reported to the vendor. Next details on how to prevent the attack. To stay protected, users need to be careful when inputting data.
In addition, users should avoid clicking suspicious links. It is also recommended to update the software to the latest release. Doing so will help to protect the system from possible attacks. End users are encouraged to contact the vendor for any help. Users who have any questions may contact us for assistance
CVE-2023-3435
The researcher discovered that an application is vulnerable to a stored XSS vulnerability. This issue has been classified as critical. The fix has been released by the vendor. It is highly recommended to upgrade the software if possible. End user are advised to monitor the process carefully. Any suspicious activity should be reported to the vendor. Next details on how to prevent the attack. To stay protected, users need to be careful when inputting data.
In addition, users should avoid clicking suspicious links. It is also recommended to update the software to the latest release. Doing so will help to protect the system from possible attacks. End users are encouraged to contact the vendor for any help. End users that have any questions may contact us for assistance.
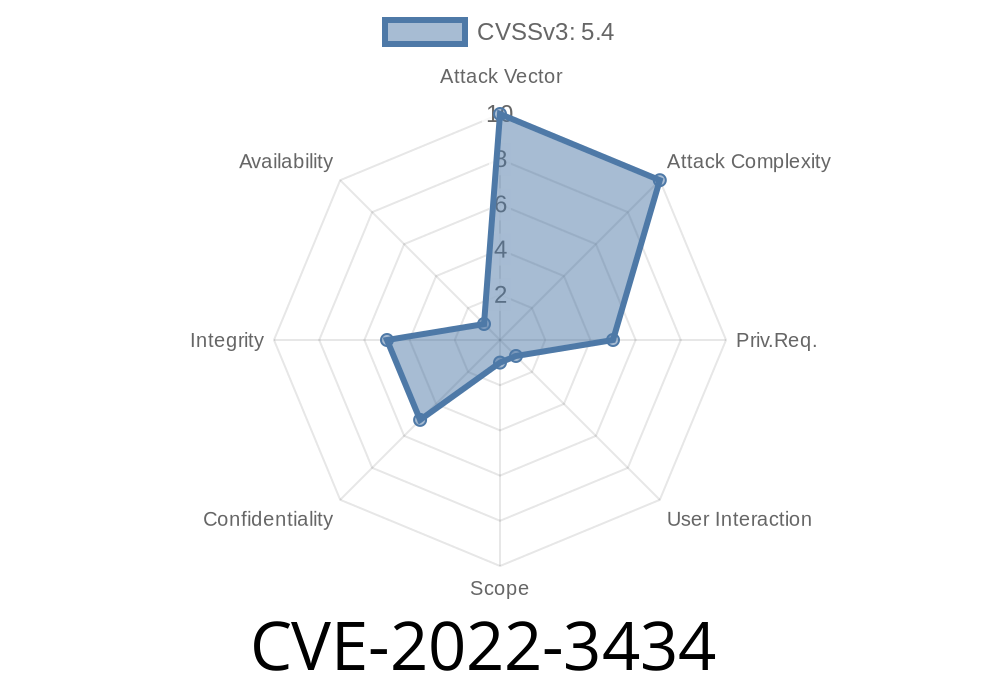
Details of the CVE-2022-3434
CVE-2022-3434 is a security flaw that allows attackers to execute arbitrary PHP code on the server. This can allow attackers to access stored application credentials, which may help them exploit the server. The fix has been released by the vendor and is highly recommended for upgrade.
CVE-2012-3552
In the security update from CVE-2012-3552, the vendor fixed a vulnerability (XSS) in the Markdown parser of WordPress. The vulnerability was classified as high by the vendor. It is recommended to upgrade to this version of WordPress. The fix has been released by the vendor and there is no need to contact them for assistance.
Timeline
Published on: 10/08/2022 11:15:00 UTC
Last modified on: 10/11/2022 17:14:00 UTC