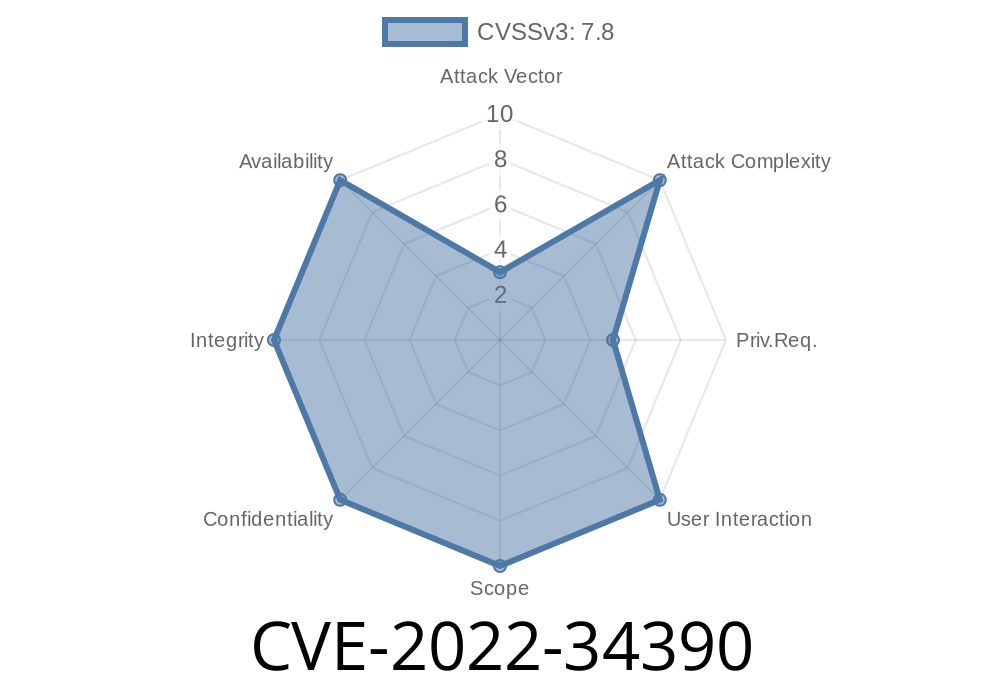
The vulnerability exists due to the fact that the code in Dell BIOS does not validate the length of the data which is received from the SMI handler. A remote attacker could send a specially crafted SMI which may lead to execution of arbitrary code in the SMRAM of the system. System administrators should be cautious of remote SMI requests from untrusted sources. Dell has released updated BIOS versions for XPS 15 9570 and Inspiron 15 8570. Users are recommended to update their systems as soon as possible.
Dell XPS 9380-D004: SMB Remote Code Execution Vulnerability
A new vulnerability has been identified in Dell BIOS and could allow a remote attacker to execute arbitrary code on the systems. The vulnerability exists due to the fact that the code in Dell BIOS does not validate the length of the data which is received from the SMI handler. A remote attacker could send a specially crafted SMI which may lead to execution of arbitrary code in the SMRAM of the system. System administrators should be cautious of remote SMI requests from untrusted sources. Dell has released updated BIOS versions for XPS 15 9570 and Inspiron 15 8570. Users are recommended to update their systems as soon as possible.
Vulnerability Finding Tips
The SMI handler simply takes a string of length 0 and grabs the first four bytes of memory. It then puts them into a buffer, which it passes onto the BIOS. The problem is that no check is done on the length of the buffer before it's passed to the BIOS. So, if an attacker sends a string that's more than 4 bytes long to this function, they will be able to execute their own code in SMRAM without needing any other privileges or access to hardware.
This vulnerability is caused by a design decision by Dell which led to an exploitable condition.
If you're working on finding vulnerabilities like this one, keep these tips in mind:
- Think about what parts of your platform are most susceptible to outside attacks due to lack of security controls.
- Gather data about attack surface size and perimeter defenses you have in place around your application or OS.
- Try to understand where attackers would prefer to exploit your application or OS as it's goes from benign to malicious behavior.
Timeline
Published on: 10/12/2022 20:15:00 UTC
Last modified on: 10/13/2022 18:25:00 UTC