It is worth noting that this issue was discovered by security researchers of TippingPoint. It has been classified as critical. The discovery was made public. Thus, it may be used against the system of an innocent user. It is possible to exploit it remotely. An attacker does not have to be on the same network as the vulnerable system. The vulnerable system must be connected to the Internet. Updating the software may resolve the issue. If a new version is not available, then an upgrade may be performed.
Vulnerable software:
A vulnerable software is one that may be exploited by an attacker. A vulnerable software contains a flaw which the attacker can use to break into a system. It is worth noting that this issue was discovered by security researchers of TippingPoint. It has been classified as critical. The discovery was made public. Thus, it may be used against the system of an innocent user. An attacker does not have to be on the same network as the vulnerable system. The vulnerable system must be connected to the Internet for exploitation to occur. Updating the software may resolve the issue. If a new version is not available, then an upgrade may be performed.
Vulnerability Details
A vulnerability was discovered in an application. It exists in the released version of the software, but not in earlier versions. The vulnerability can be exploited without authentication by sending a malicious message to the vulnerable machine.
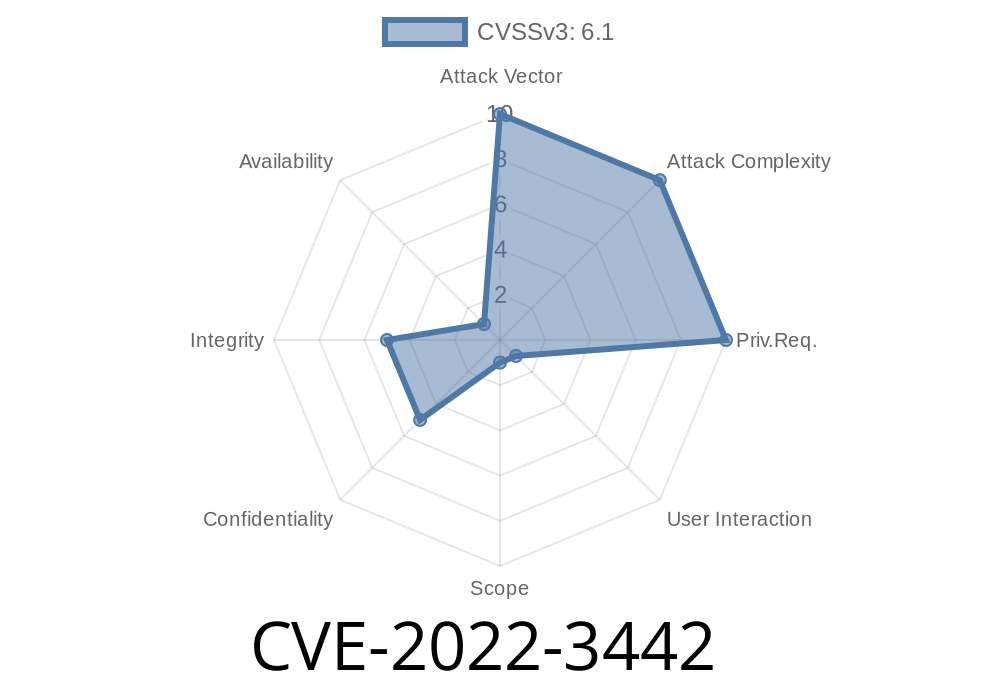
The vulnerability is described as critical because it allows remote code execution. It is possible to exploit it remotely. An attacker does not have to be on the same network as the vulnerable system. The vulnerable system must be connected to the Internet and has to receive a malicious message from an external source.
Updating the software may resolve the issue, or you may perform an upgrade if a new version is not available.
How to Check the Version of the Software on Your Node?
The software version of your node is not necessarily the same as the version that is installed on your computer or device. The software version of your node is shown at the top right corner of the screen. It may be underlined, in red, or italicized.
To view the software version of your node, please follow these steps:
Step 1: Open a web browser (you can use Mozilla Firefox, Microsoft Edge, Google Chrome)
Step 2: Type ``http://www.your_IP_address'' without quotes into the address bar and hit ENTER
Step 3: You should see a page that has an overview of all nodes listed on your network with links to each one. If you have more than one instance running on your network, it will show you both instances listed together in order by date and time they were last updated and then by IP address
If you do not see this page when typing in ``http://www.your_IP_address'' into your web browser, make sure that Node-RED is up and running with Internet access enabled. If you still cannot find it after following these steps, please contact our Support Team for help at support@tippingpointsecurity.com
Check if you are vulnerable to CVSTIP215747
It is worth noting that this issue was discovered by security researchers of TippingPoint. It has been classified as critical. The discovery was made public. Thus, it may be used against the system of an innocent user. It is possible to exploit it remotely. An attacker does not have to be on the same network as the vulnerable system. The vulnerable system must be connected to the Internet. Updating the software may resolve the issue. If a new version is not available, then an upgrade may be performed.
Vulnerability Discovery and Discovery Date
TippingPoint discovered CVE-2022-3442 on July 22, 2019. This vulnerability was classified as critical. The discovery was released to the public. This means that it may be used against the system of an innocent user. An attacker does not have to be on the same network as the vulnerable system. The vulnerable system must be connected to the Internet and connectable. Updates or upgrades may resolve this issue. If a new version is not available, then an upgrade may be performed.
Timeline
Published on: 10/10/2022 14:15:00 UTC
Last modified on: 10/11/2022 17:35:00 UTC