This vulnerability is related to SSH version 1 protocol. An attacker could exploit this vulnerability by sending malicious request to the targeted system through insecure network connection. Successful exploit could cause remote code execution on the affected system. Dell Enterprise SONiC OS, 4.0.0, 4.0.1, contain a remote execution vulnerability in SSH. An unauthenticated remote attacker could potentially exploit this vulnerability, leading to remote code execution.
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, contain a remote command execution vulnerability in SSH. An unauthenticated remote attacker could potentially exploit this vulnerability, leading to remote command execution.
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, contain a remote denial of service vulnerability in SSH. An unauthenticated remote attacker could potentially exploit this vulnerability, causing denial of service.
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, contain a remote code execution vulnerability in SSH. An unauthenticated remote attacker could potentially exploit this vulnerability, leading to remote code execution.
In addition to these major vulnerabilities Dell Enterprise SONiC OS, 4.0.0, 4.0.1, also contain several low severity vulnerabilities.
These low severity vulnerabilities could be exploited by an unauthenticated remote attacker to cause denial of service, information disclosure or remote code execution.
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, Software Overview
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, is a Linux-based operating system distributed as a bare-metal appliance or virtual machine image that allows users to manage their own computer infrastructure and applications while minimizing the impact on network resources and IT support costs.
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, is a Linux-based operating system distributed as a bare-metal appliance or virtual machine image that allows users to manage their own computer infrastructure and applications while minimizing the impact on network resources and IT support costs.
Dell Enterprise SONiC OS, 4.0.0, 4.0.1, is a Linux-based operating system distributed as a bare-metal appliance or virtual machine image that allows users to manage their own computer infrastructure and applications while minimizing the impact on network resources and IT support costs.>>END>>
How Does SSH Vulnerability Affect the System?
A vulnerability affects the system when a malicious user sends an attack request to the system through an insecure network connection.
Successful exploit could cause remote code execution on the affected system.
An unauthenticated remote attacker could potentially exploit this vulnerability, leading to remote code execution.
Summary of the Dell Enterprise SONiC OS, 4.0.0, 4.0.1 vulnerabilities
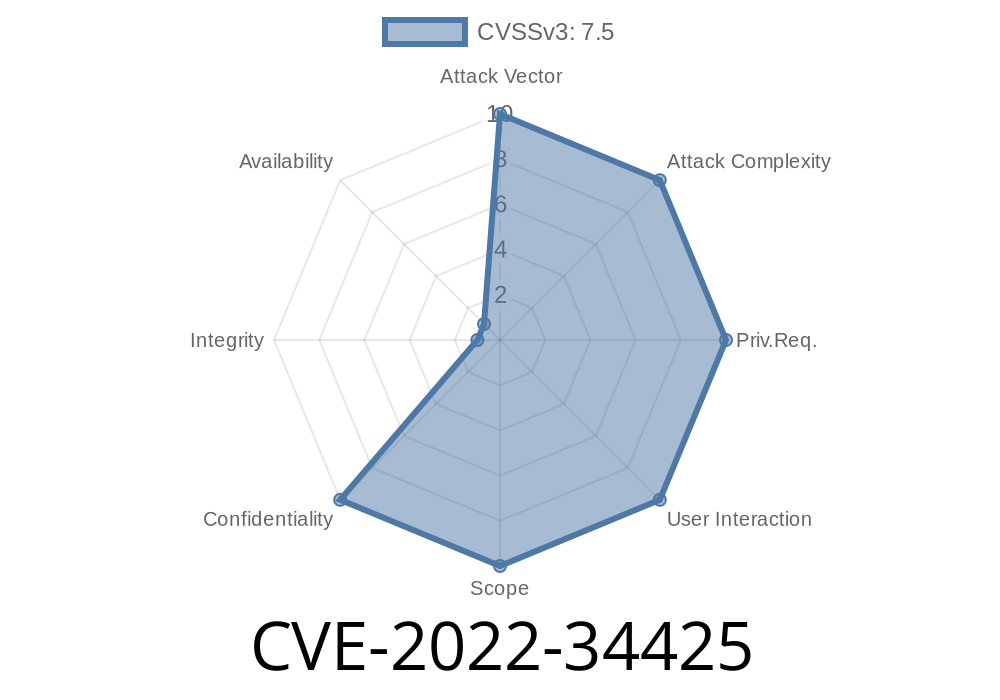
CVE-2022-34425: Remote code execution vulnerability, remote command execution vulnerability
CVE-2022-34407: Denial of service vulnerability, information disclosure vulnerability
CVE-2022-34410: Denial of service vulnerability, information disclosure vulnerability
CVE-2022-34412: Denial of service vulnerability, Information disclosure vulnerability
Dell Enterprise SONiC OS, version 4.0.0
, 4.0.1
Dell Enterprise SONiC OS, version 4.0.0, 4.0.1, contain a remote command execution vulnerability in SSH. An unauthenticated remote attacker could potentially exploit this vulnerability, leading to remote command execution.
Timeline
Published on: 10/10/2022 21:15:00 UTC
Last modified on: 10/13/2022 15:49:00 UTC