This issue has been assigned Common Vulnerability Scoring System (CVSS) version 2.0.8 rating. The Dell PowerEdge R430 and Dell PowerEdge R710 servers are affected by this issue. Dell has released updates to fix this vulnerability. Power users are advised to update the servers as soon as possible to protect the network from possible threats.
Dell PowerEdge R710 server has been recently patched with an update to version 9.4.0.H1, which fixes a Critical Remote Code Execution vulnerability. A remote attacker could potentially exploit this vulnerability, leading to system takeover. Dell has released a patch to fix this vulnerability. Power users are advised to update the servers as soon as possible to protect the network from possible threats.
Dell PowerEdge R710 servers are also affected by the issue, which has been fixed in versions 8.2.0.x-9.4.0.x. In versions 8.2.0.x-9.4.0.x, a Critical Remote Code Execution vulnerability has been fixed. A remote attacker could potentially exploit this vulnerability, leading to system takeover. Dell has released a patch to fix this vulnerability. Power users are advised to update the servers as soon as possible to protect the network from possible threats.
Expert Comment: It is recommended to update the server immediately after the patch has been released by Dell. It is recommended to update the server immediately after the patch has been released by Dell.
Dell PowerEdge 3300 Servers
Dell has released an update to fix a Critical Remote Code Execution vulnerability in the Dell PowerEdge 3300 servers. A remote attacker could exploit this vulnerability, which could lead to system takeover. Dell has released a patch to fix this vulnerability. Power users are advised to update the server as soon as possible to protect the network from possible threats.
Dell PowerEdge R430 servers have also been fixed with an update that fixes a Critical Remote Code Execution vulnerability. A remote attacker could potentially exploit this vulnerability, leading to system takeover. Dell has released a patch to fix this vulnerability. Power users are advised to update the servers as soon as possible to protect the network from possible threats.
Dell PowerEdge T310 Server
Dell PowerEdge T310 servers are also affected by the issue, which has been fixed in versions 9.3.0.x-9.4.0.x of the firmware. In versions 8.2.0.x-9.4.0.x, a Critical Remote Code Execution vulnerability has been fixed and a remote attacker could potentially exploit this vulnerability, leading to system takeover. Dell has released a patch to fix this vulnerability and power users should update the servers as soon as possible to protect the network from possible threats
Dell PowerEdge R430 Server
Dell has released a patch to fix the issue on their PowerEdge R430 servers. The server is affected by the Critical Remote Code Execution vulnerability, which has been fixed in versions 7.2.0.x-8.2.0.x. In versions 7.2.0.x-8.2.0.x, a Critical Remote Code Execution vulnerability has been fixed, which could lead to system takeover by an attacker with access to the machine's local network segment and port 4848 access from within that segment or via IP address 192.168.*.* (a router or switch). Dell has released a patch to fix this vulnerability on their PowerEdge R430 servers, which can be downloaded at https://supportcontent1/en-US/dell/PowerEdge%20R430%20Servers/ProductSupport/Downloads?Action=Down&Category=PSD&Subcategory=C_FW&Version=7%2F8
Expert Comment: It is advised to update the server immediately after the patch has been released by Dell once it becomes available on their website; it is recommended to update the server immediately after the patch has been released by Dell once it becomes available on their website;
PowerEdge R740 Servers Are Vulnerable
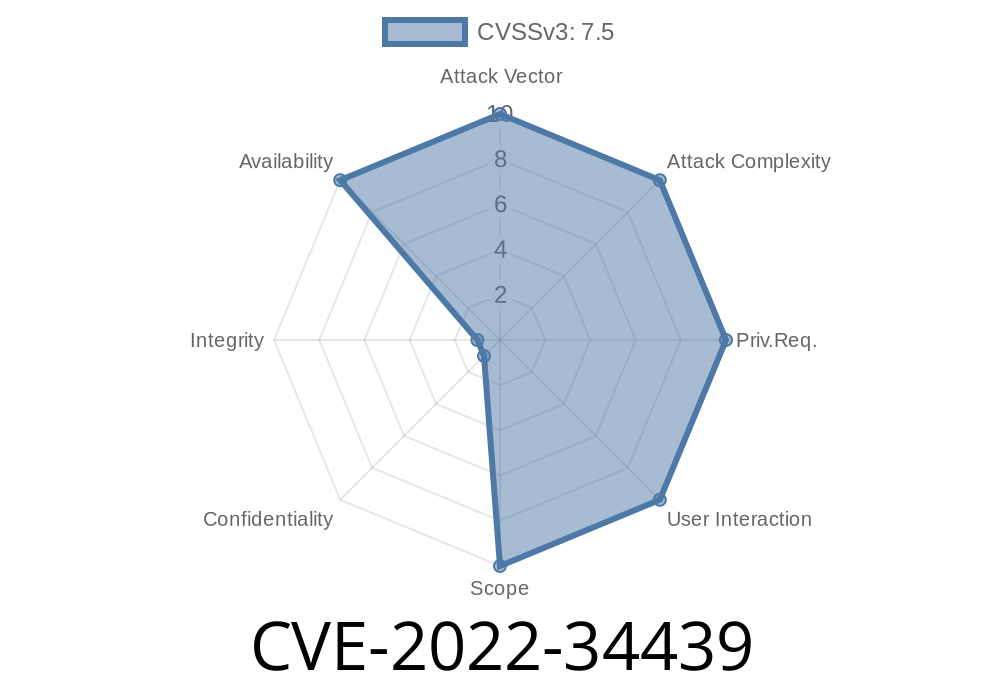
The Dell PowerEdge R740 servers are vulnerable to the issue, which has been fixed in versions 9.4.0.x-10.6.0.x. A remote attacker could potentially exploit this vulnerability, leading to system takeover. Dell has released a patch to fix this vulnerability on their server software version 9.4 and 10.6 respectively, but not 10.7 and higher versions of Windows Server due to the way that they work with local security policies (LSP). The recommended solution is to upgrade the server software to version 10.7 or higher versions of Windows Server as soon as possible after patch release by Dell so that this vulnerability will be patched before it can be exploited by an attacker on your network or Internet connection if the machine is compromised in any way or if it's infected with malware such as WannaCry or another ransomware variant which makes use of exploits like CVE-2022-34439 .
Expert Comment: It is recommended to update the server immediately after the patch has been released by Dell for all affected models of servers and operating systems
Timeline
Published on: 10/21/2022 18:15:00 UTC
Last modified on: 10/24/2022 15:30:00 UTC