---
In October 2022, security researchers found a critical vulnerability in Google Chrome: CVE-2022-3448. If you’re curious about the risks, how it worked, and even what an attack might look like, you’re in the right place. I’ll break it down with plain words, references, and actual exploit concepts for this dangerous browser flaw.
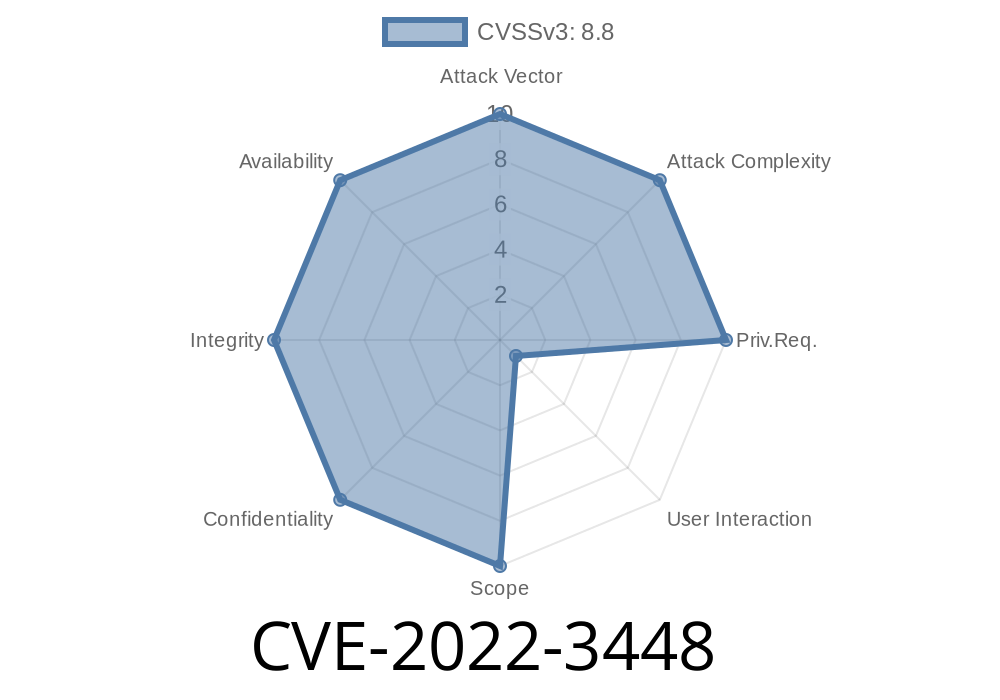
What Is CVE-2022-3448?
CVE-2022-3448 is a “use-after-free” vulnerability in Chrome’s Permissions API—a system web pages use to ask for things like geolocation, camera, etc. The bug existed in versions before 106..5249.119.
A “use-after-free” means Chrome tried to use a chunk of memory after it was already freed, which can let hackers corrupt data and, in many cases, run their own code.
Why is it Dangerous?
A remote attacker could send a web page with malicious code. If the victim interacts with it “the right way” (using some clicks or UI gestures), that page could trigger heap corruption. With extra effort, this can lead to running malware on your system—just by opening a web page.
Severity: High
(See Chromium’s own report: Chromium Bug 1368574)
Simple Demo: Triggering the Use-After-Free (Simplified!)
Below is a simplified illustration (for learning!) of how JavaScript code might trigger the bug. This isn’t a weaponized exploit, just a teaching code example.
<!-- This is a simplified example for educational use only! -->
<!DOCTYPE html>
<html>
<body>
<button id="testBtn">Trigger Permissions API Bug</button>
<script>
let resolveFunc;
function requestPermission() {
navigator.permissions.query({name: 'geolocation'})
.then(r => {
// Here the original object is used; a bug in Chrome might free it before this runs!
resolveFunc = r;
});
}
document.getElementById('testBtn').onclick = function() {
for (let i = ; i < 100; i++) {
requestPermission();
}
// Some crafted actions to speed up GC and possible freeing.
setTimeout(() => {
// Try to interact with the potentially-freed object.
if(resolveFunc) {
try {
console.log(resolveFunc.state);
} catch(e) {
console.error("Crash or use-after-free:", e);
}
}
}, 100);
}
</script>
</body>
</html>
Note: Real exploits involve more advanced techniques, such as heap grooming and shellcode. This is an educational pattern, not a working hack.
Any system: Windows, Mac, Linux—all Chrome browsers vulnerable before v106..5249.119.
- Social engineering: User must engage with page for attack to work (like a click or permission request dialog).
Fix and Mitigation
Fix Version: Chrome 106..5249.119 and above.
References
- Chromium Security Bug 1368574 (official report)
- CVE Details for CVE-2022-3448
- Stable Channel Update for Desktop - Google Chrome Releases
Final Thoughts
The use-after-free bug in Chrome’s Permissions API was a big deal because it allowed hackers to take over your machine with just a web link and a click. These kinds of bugs remind us all—keep your browser up to date, and watch what you click!
If you want deeper technical details, see the Chromium patch for the fix.
Stay safe and always keep browsers patched. Even little dialog boxes can hide big dangers!
Timeline
Published on: 11/09/2022 19:15:00 UTC
Last modified on: 11/11/2022 02:17:00 UTC