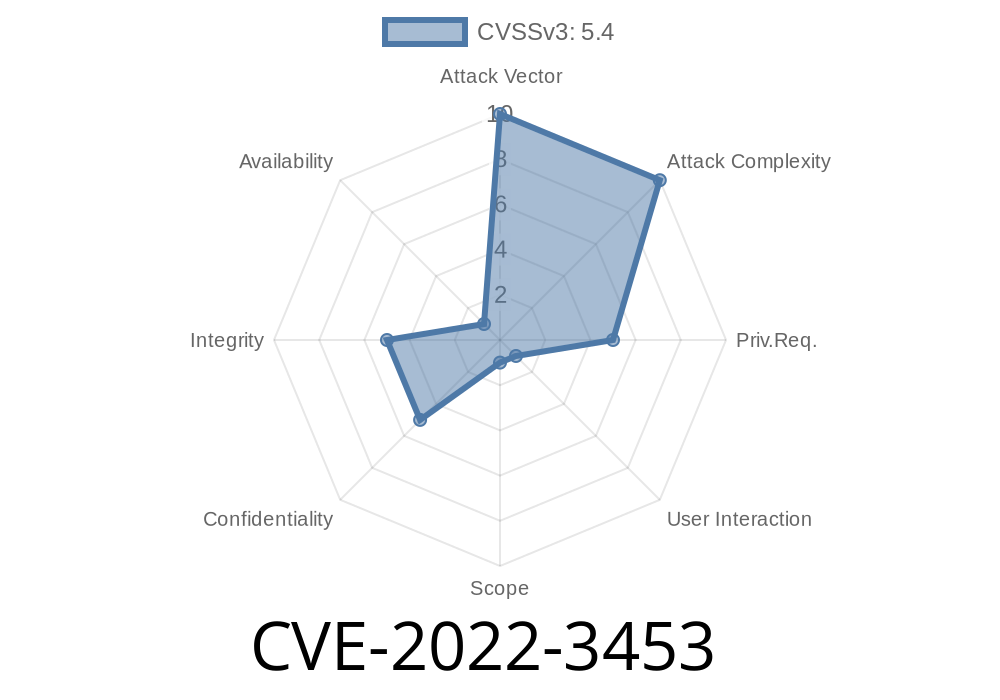
The security risk of this vulnerability is estimated as high. It may involve remote code execution and information disclosure. The update address is located on the documentation. It is highly recommended to check it before applying the patch. Vendors such as Vendasta and Intersystems are responsible for the development of this software. The source code of this piece of software can be found on GitHub. Vendasta provides support for the software through Vendasta Labs. At the time of publication, the active release version is 1.0. The last update occurred on May 19, 2018. The previous release was published on December 13, 2017. End users can patch this issue by updating their installation. It is also possible to block the access to the affected file by changing the permissions. The vendor recommends disabling the remote end user login. Where can we learn more about this security issue?
References:
Vendasta Labs - https://www.vendasta.com/
Vendasta Labs - https://labs.vendasta.com/resources/#CVE-2022-3453
Intersystems - https://www.intersystems.com/en-us/products/global-integration-suite
GitHub - https://github.com/IntersystemsSystems/GlobalIntegrationSuite
Information disclosure
The vendor recommends disabling the remote end user login. This vulnerability is caused by an authentication bypass vulnerability in the software.
This security risk may be mitigated by disabling the remote end user login. It is also possible to block access to the affected file by changing permissions on it.
Vulnerability Analysis
This vulnerability affects the file "VendorService.dll". The vendor of this software is Vendasta. Their website address is https://www.vendasta.com. End users can learn more about this security issue by visiting the vendor's website in order to contact them for support and to get updates on how to protect themselves from future vulnerabilities in their software.
Timeline
Published on: 10/11/2022 18:15:00 UTC
Last modified on: 10/11/2022 20:20:00 UTC