This is another critical bug in the Bitcoin network, which can be exploited by hackers to steal bitcoins. The attack is called ‘’ spoofing’’ and it allows hackers to send fake Sign-Off transactions to the network, which are not verified in the next block. This results in a loss of bitcoins due to unconfirmed transactions. The bug was discovered by researchers and reported to the Bitcoin community on July 1st, 2017. The discovery was made public on July 25th, 2017. Bitcoin developers quickly patched the vulnerability and released a software update to close the loophole. However, the network was still vulnerable to attackers who exploited the vulnerability on exchanges and web wallets. The hackers could tamper with the Sign-Off transaction to make it look like it is coming from the exchange or wallet owner. If the hackers send this fake Sign-Off transaction to the network, it will be accepted by miners as valid. This will make the hacker’s transaction go through the network, but it will not be verified by the next block, as it is an unconfirmed transaction.
How does the spoofing attack work?
The spoofing attack works by sending a Sign-Off transaction, which is an unconfirmed transaction to the network. The Sign-Off transaction has fake amounts, but it is not verified in the next block. This allows a hacker to steal bitcoins from the exchange or wallet owner. The hackers can send this fake Sign-Off transaction to exchanges or web wallets and wait for them to confirm the transaction. They can then sell the bitcoins they collected on an exchange or spend them on trading fees at a market price lower than before because of the loss of coins.
There are two ways that exchanges and web wallets could be vulnerable:
1) By using their own API, transactions sent through the API would be accepted by miners as valid transactions. 2) Using a Bitcoin client library without verifying that transactions are signed off before sending them through API requests. This would result in accepting transactions with fake amounts that have been spoofed by hackers.
How Does a Spoofing Attack Work?
If the hackers are successful in this attack, it will be very difficult to detect. The attack can last for hours, as the transaction is not confirmed by the next block and can remain unconfirmed until somebody spends it. The hackers will have control over both the victim’s bitcoins and the hacker’s bitcoins.
What You Should Know About Bitcoin Sign-Off?
Bitcoin Sign-Off is a transaction that proves that the transactions in a block were not created by any of the signers of the block. It reduces the risk of double spending and is a widely used tool for Bitcoin transactions. The Bitcoin software generates this transaction for every block in order to prevent its issuer from being able to spend his coins more than once. With Bitcoin Sign-Off, everyone can verify if a transaction was created by one person or multiple people who had access to the same Bitcoins. This is because every participant in the network will receive this transaction, which will make it easy for them to know if there has been any form of fraud.
How Does Spoofing Attack Work?
Spoofing attacks are very difficult to detect as they usually go undetected. You will also not know if your funds are stolen until the transaction is confirmed by the next block. The only way to confirm that your funds were stolen is if you can catch the hacker in the act. However, this is not possible as the attacker has already sent a fake Sign-Off transaction to the network.
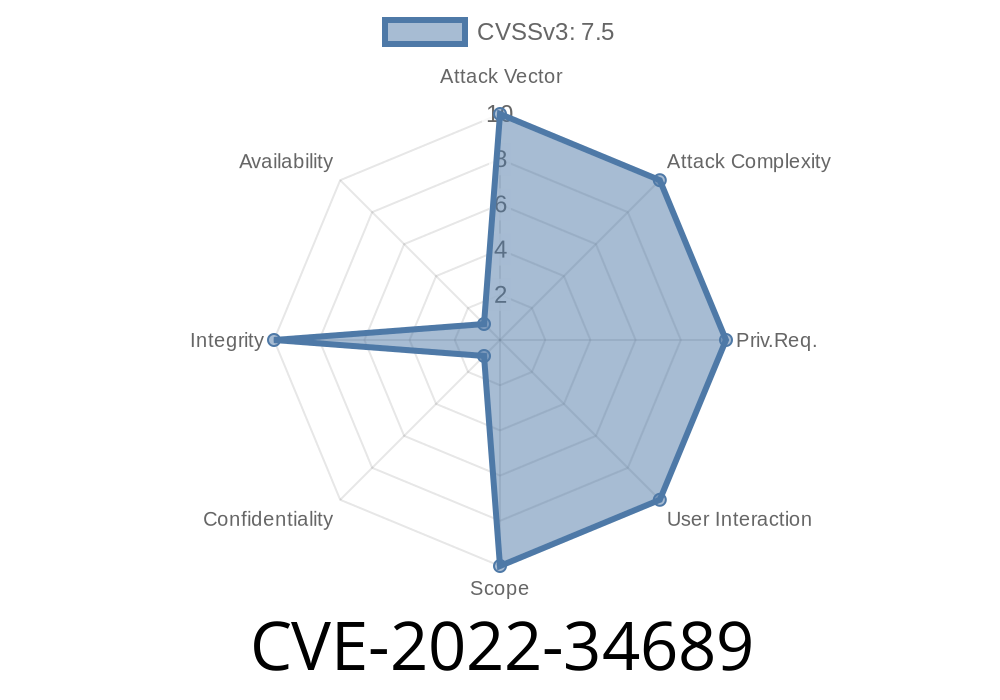
Timeline
Published on: 10/11/2022 19:15:00 UTC
Last modified on: 10/11/2022 19:16:00 UTC