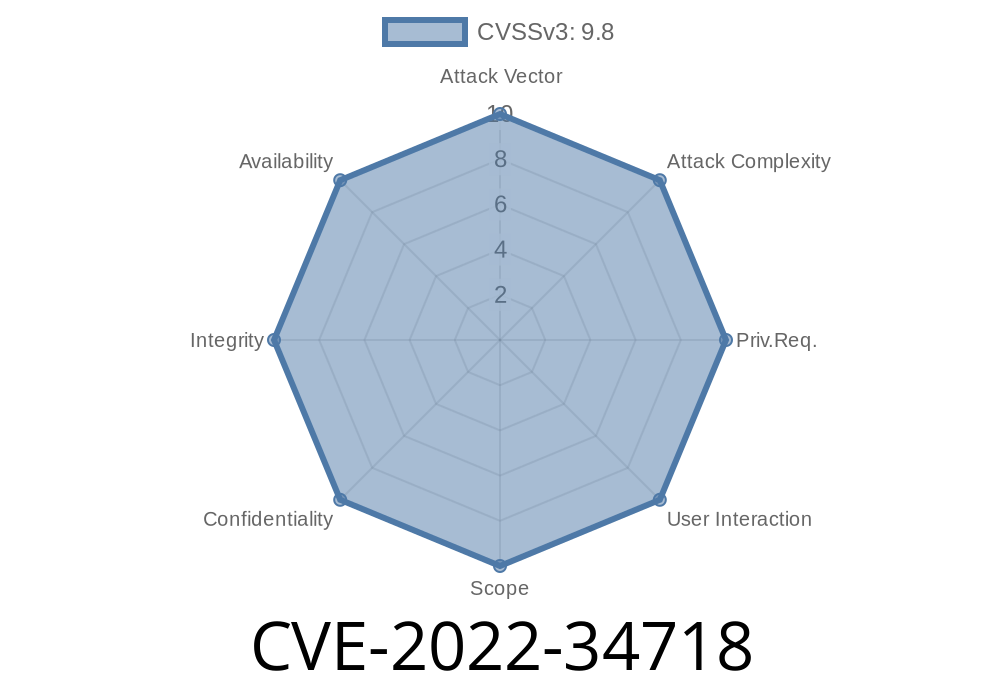
This vulnerability allows remote attackers to compromise vulnerable systems and execute arbitrary code on them.
Affected software
Internet Explorer 6 (all versions)
Internet Explorer 7 (all versions)
Internet Explorer 8 (all versions)
Internet Explorer 9 (all versions)
It is also possible to execute remote code on a vulnerable Windows 8 or Windows Server 2012 machine with IE 11 installed.
Recommendations
It is highly recommended to install all vendor provided updates as soon as they become available.
It is also recommended to install non-vendor provided security updates.
In case you are not in control of the Windows Update infrastructure, then it is necessary to patch the system as soon as possible.
In case you do not have enough privilege to install the updates, then you should limit the damage by blocking access to unpatched components.
In case you do not have enough privilege to install the updates, then you should limit the damage by blocking access to unpatched components. If possible, apply the MS17-010 update.
When possible, apply mitigations such as disabling e-mail, disable remote desktop access, disable remote management, and disable P2P.
References
CVE-2022-34718: Microsoft Internet Explorer CVE-2022-34718
MS17-010: Microsoft Security Bulletin MS17-010 CVE-2017-8759
Internet Explorer 6
(all versions)
The vulnerability in this case is a remote code execution vulnerability that exists due to the way Internet Explorer handles objects in memory.
References: https://www.microsoft.com/en-us/download/details.aspx?id=48145
http://www.kb.cert.org/vuls/id/539379
Windows 10
In this article, we will discuss some of the mitigations that may prevent the exploit from exploiting your system.
It is highly recommended to install all vendor provided updates as soon as they become available.
It is also recommended to install non-vendor provided security updates.
Timeline
Published on: 09/13/2022 19:15:00 UTC
Last modified on: 09/17/2022 01:22:00 UTC