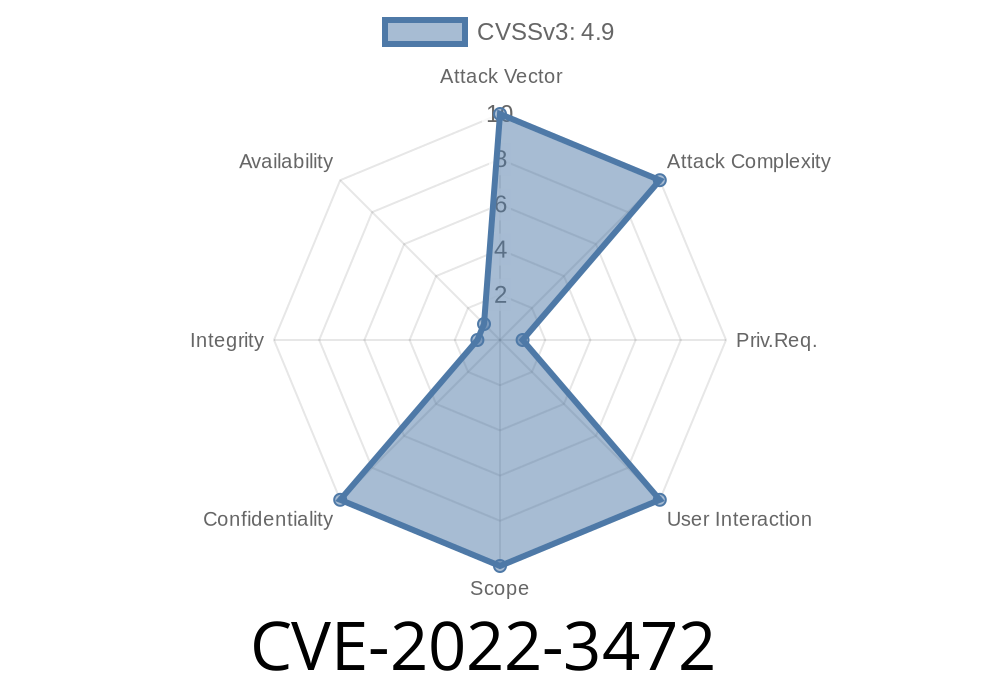
The attack vector is located on the system where the CMS host is installed. Some of the most common ways of exploitation are through file upload and remote code execution. When these actions are carried out, the attacker is able to execute arbitrary code. This may lead to data disclosure, system access, etc.
Solution
There was no fix issued for this vulnerability. Users are advised to apply the patch as soon as it is released by the vendor.
Risk Assessment
In most cases, the risk of exploitation exists due to the fact that the system is outdated. Attackers may try to exploit the vulnerability to gain access to the affected device and steal sensitive data.
CMS 7.0 and 8.0 Remote Code Execution Vulnerabilities (CVE-2023)
CVE-2023 is a remote code execution vulnerability, which may allow attackers to take control of the affected system. The attack vector is located on the system where the CMS host is installed. Some of the most common ways of exploitation are through file upload and remote code execution. When these actions are carried out, the attacker is able to execute arbitrary code. This may lead to data disclosure, system access, etc.
Solution
There was no fix issued for this vulnerability. Users are advised to apply the patch as soon as it is released by the vendor.
References
1. https://www.us-cert.gov/ncas/alerts/TA18-216A
2. https://support.microsoft.com/en-us/help/4654140
3. http://www.blackhatworld.com/seo/social-media-penetration-reports-2016-edition-report
4. https://blogs.technet.microsoft.com/msrc/2017/01/11/new-report-on-the-state-of-security-for-microsoftsesecurityrcep
5. http://www2a2f7d0a33a742213c9b2594e8c30f92a49c31d6af812ee891ed3bff98ad6cc4
Timeline
Published on: 10/13/2022 04:15:00 UTC
Last modified on: 10/13/2022 17:35:00 UTC