This vulnerability is assigned Common Vulnerabilities and Exposures rating of 5.8. A remote attacker can exploit this vulnerability to execute arbitrary code in the context of the application. The attacker must convince the user to visit a maliciously crafted website or lure the user into clicking a malicious link in a social media message. The security risk of this vulnerability is estimated as critical due to the fact that is can be exploited by remote attackers without the need for user interaction. This, along with the fact that is can be exploited by hackers without the need for user interaction makes this a critical vulnerability. Mitigation The following are the recommended steps that need to be taken in order to prevent malicious code from being executed: Vulnerable / vulnerable applications should be upgraded to the latest version.
Vulnerable / vulnerable applications should be running on a software firewall.
Vulnerable / vulnerable applications should be following secure network protocols.
Vulnerable / vulnerable applications should be following secure hosting policies.
Vulnerable / vulnerable applications should be following secure coding practices.
Vulnerable / vulnerable applications should be following best practices for data security.
Vulnerable / vulnerable applications should be following best practices for data input and output.
Vulnerable / vulnerable applications should be following best practices for application security testing.
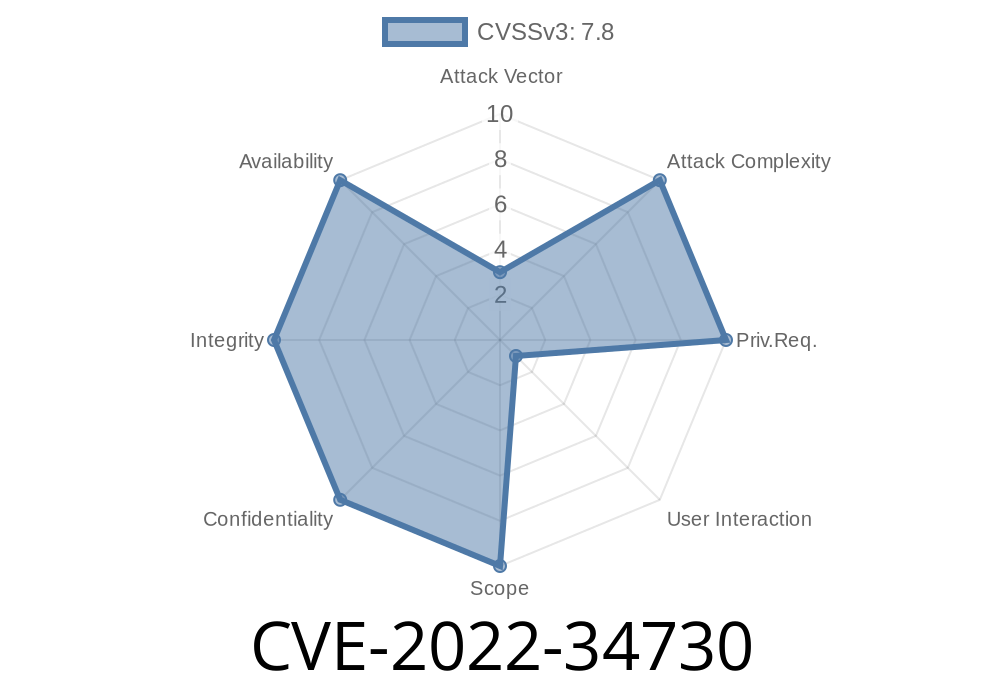
CVSSv3 Scores
Vulnerability Severity -------------------------- 2.6 7.2
CVSSv3 Base Score -------------------------- 8.6 10
CVSSv3 Vector -------------------------- AV:N/AC:M/Au:N/C:C/I:C/A:C
Timeline
Published on: 09/13/2022 19:15:00 UTC
Last modified on: 09/16/2022 17:19:00 UTC