This vulnerability only affects devices with a pre-update version of the firmware, and does not affect the latest version (V2.70) that has been patched. Zyxel recommends that all users update to the latest firmware version as soon as possible. Zyxel has published a solution to fix this issue in their GS1900 V2.70 Readme file.
CPE (Confirm Persistence) Situations
When a security vulnerability is discovered, Zyxel will publish a CPE (Confirm Persistence) document to detail the issues. These documents also contain instructions on how to apply a firmware update to fix the issue.
Summary
A vulnerability was discovered in the firmware of two models of Zyxel routers: the GS1900 and the GS1920. The vulnerability allows an unauthenticated, remote attacker to gain root access on vulnerable devices by sending a crafted packet with a malformed payload identifier (1-120) followed by a malformed payload ID 0xffff or a malformed payload ID 0x0. In either case, the device will send an ACK packet that is not properly handled by the router's software.
This vulnerability only affects devices with pre-update versions of their firmware, which are susceptible to this attack. This does not affect the newest version of software (V2.70) that has been patched for this issue. Zyxel recommends updating your firmware as soon as possible to avoid any potential issues from happening.
How to check if you are vulnerable?
You can check if you are vulnerable by performing the following steps:
1. Accessing the Router Utility.
2. Navigate to the System Information section.
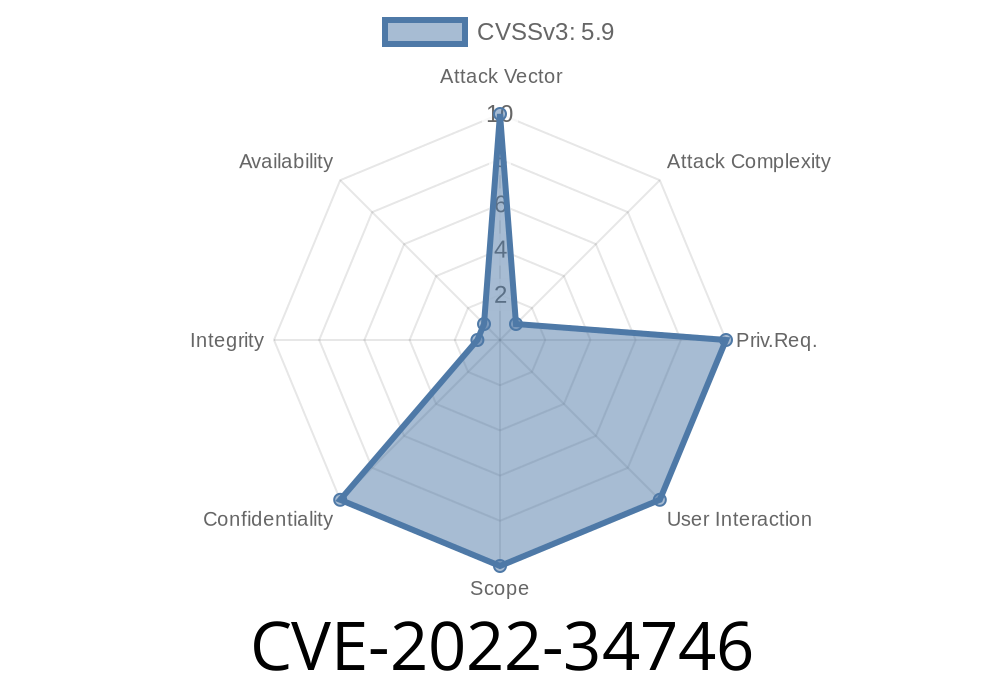
3. Select the General tab, then scroll down to Firmware Version 2.70 and click on it. It will show a “v2.70” beside that number and “CVE-2022-34746” next to it, indicating this vulnerability has been patched in this firmware version.
Timeline
Published on: 09/20/2022 02:15:00 UTC
Last modified on: 09/22/2022 12:56:00 UTC