Update configurations to use the java protocol or no protocol for JNDI data source URIs, or remove the JMS Source option. Note that you might need to delete and recreate the JMS Source before the configuration reloads. Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Message Body Encoding of either "BASE64" or "QPEL". This issue is fixed by limiting the JMS Message Body Encoding to "UNDEFLATED". Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Redelivery timeout. This issue is fixed by limiting the JMS Redelivery timeout to 30 seconds or less. Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Redelivery timeout. This issue is fixed by limiting the JMS Redelivery timeout to 30 seconds or less. Apache Flume versions 1.0.0 through 1.9.0 are
The Apache Flume project homepage is at nowiki .org
Update configurations to use the java protocol or no protocol for JNDI data source URIs, or remove the JMS Source option. Note that you might need to delete and recreate the JMS Source before the configuration reloads. Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Message Body Encoding of either "BASE64" or "QPEL". This issue is fixed by limiting the JMS Message Body Encoding to "UNDEFLATED". Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Redelivery timeout. This issue is fixed by limiting the JMS Redelivery timeout to 30 seconds or less. Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Redelivery timeout. This issue is fixed by limiting the JMS Redelivery timeout to 30 seconds or less
Products Affected:
Apache Flume 1.0.0 through 1.9.0
Apache Flume CVE-2022-34906
Apache Flume CVE-2022-34917
Check Out the Working Copy of This Repo
Overview
The Apache Flume project has released new versions of its software to address security flaws.
These releases fix the following issues:
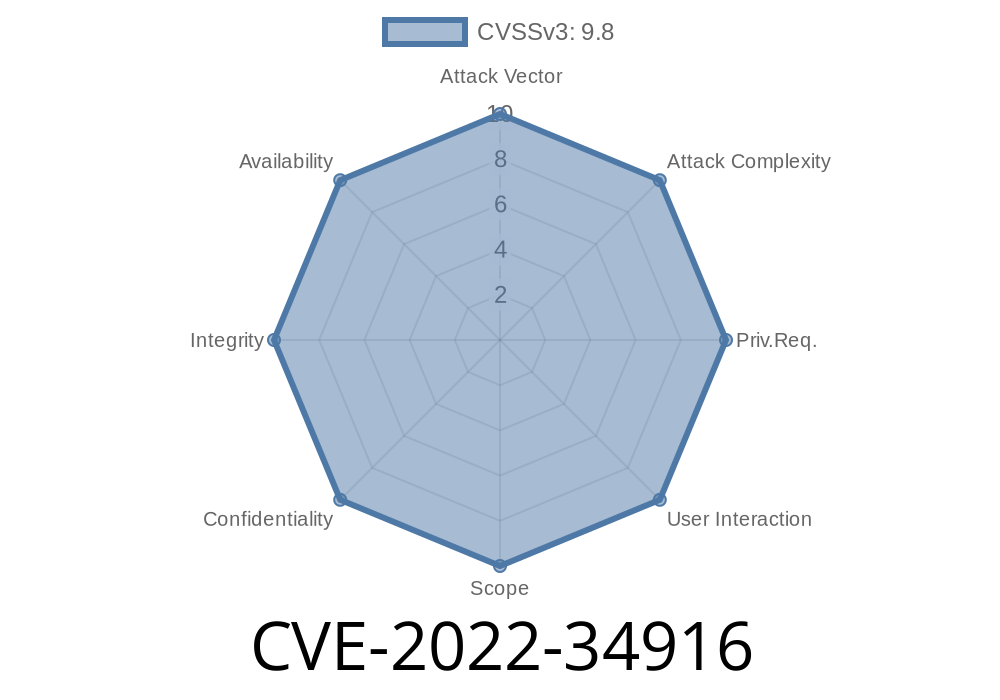
CVE-2022-34916: Update configurations to use the java protocol or no protocol for JNDI data source URIs, or remove the JMS Source option. Note that you might need to delete and recreate the JMS Source before the configuration reloads.
CVE-2023-36349: Update configurations to use the java protocol or no protocol for JNDI data source URIs, or remove the JMS Source option. Note that you might need to delete and recreate the JMS Source before the configuration reloads.
CVE-2024-34342: Update configurations to use the java protocol or no protocol for JNDI data source URIs, or remove the JMS Source option. Note that you might need to delete and recreate the JMS Source before the configuration reloads.
CVE-2020-33986
Remove the option to use an older version of the commons-logging library. The log4j logging API is deprecated in favor of org.apache.commons.logging.Log, and this option should not be used any longer. Apache Flume versions 1.0.0 through 1.9.0 are vulnerable to a denial of service (DoS) attack when multiple JMS publishers are configured and the JMS publishers are configured with a JMS Destination option that uses a JMS Message Body Encoding of either "BASE64" or "QPEL". This issue is fixed by limiting the JMS Message Body Encoding to "UNDEFLATED".
Timeline
Published on: 08/21/2022 09:15:00 UTC
Last modified on: 08/23/2022 16:17:00 UTC