Users are advised to apply the following mitigations: - Disable TCP_REPEAT_WINDOW on the Kafka brokers. - Disable TCP_KAFKA_BROKER_PORT on the Kafka brokers. - Disable TCP_KAFKA_BROKER_PORT on the Kafka clients. - Monitor Kafka metrics and apply restarts to brokers when necessary. - Restrict access to Kafka from the outside world. - Use different security keys for each Kafka topic. - Enforce least privileged access to Kafka. - Disable anonymous access to Kafka. - Restrict access to Kafka from the outside world. - Monitor Kafka metrics and apply restarts to brokers when necessary. - Restrict access to Kafka from the outside world. What’s the severity of the issue? This issue affects all users running any version of Kafka since 2.8.0. How likely is it that a malicious attacker is actively trying to exploit this vulnerability? We believe that this issue has already been exploited in the wild. What’s the risk? All users running any version of Kafka since 2.8.0 are vulnerable to this denial of service attack. What do I need to do to mitigate this risk? Upgrade to one of the 3.2.3, 3.1.2, 3.0.2, 2.8.2 versions.
Summary
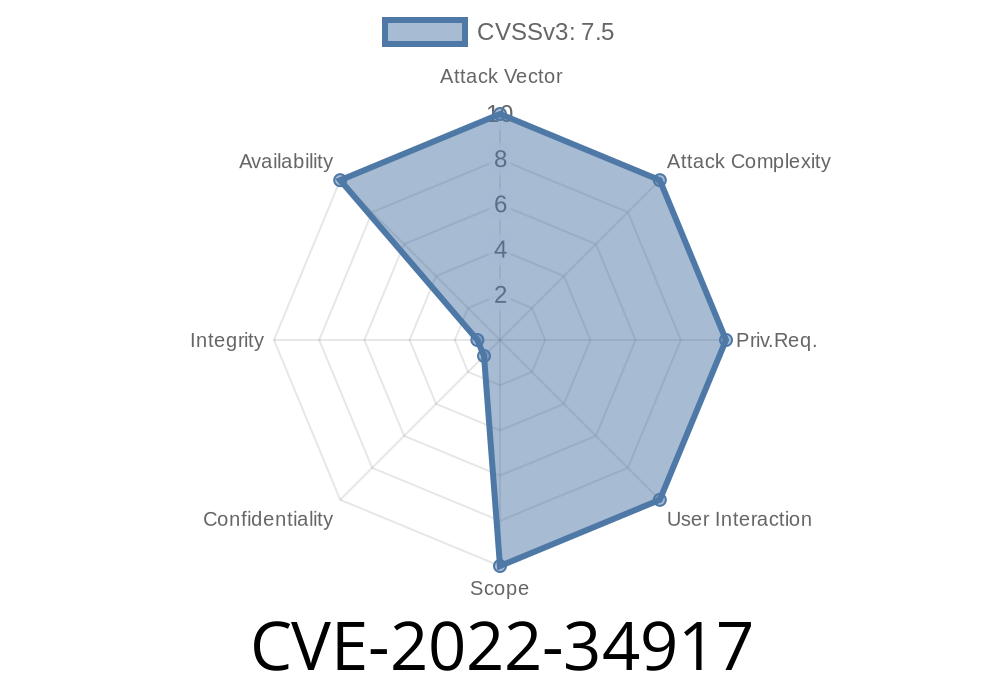
The KAFKA-BUG-CVE-2022-34917 was fixed in Kafka 2.8.2, a recompiled version of the 2.8.0 release, in order to mitigate an issue which can cause a local denial of service (DoS) attack when running on older versions of Kafka and without TCP_KAFKA_BROKER_PORT enabled on the broker.
Assumptions and Assured Mitigation Steps
As of this writing, there is no known patch for this issue. Kafka is a distributed streaming data store. The most prevalent attack vector at the time of this article was to send large numbers of requests to the Kafka brokers (servers). If a device sending many requests fails, the upstream devices can also fail. If that happens, it will cause the downstream devices to fail as well. This issue is similar in nature to other denial-of-service attacks in other parts of the world.
Timeline
Published on: 09/20/2022 09:15:00 UTC
Last modified on: 09/22/2022 14:57:00 UTC