The security risk of this vulnerability is estimated as critical by vendors. It is assumed that a hacker may leverage this issue for cross site request forgery. The issue may also be exploited for remote code execution. By manipulating the argument of a specific URL, it may be possible to execute arbitrary code. Another possible attack involves injecting malicious code in the context of a specific URL. It may be possible to exploit this vulnerability to launch a phishing campaign. It may also be possible to manipulate the web application to steal private information. In addition to these concerns, it has been confirmed that this vulnerabilty may be exploited to conduct cross site scripting attacks. This may lead to information leakage or even full remote code execution. CVE-ID: N/A
Mitigation Strategies for Cisco AnyConnect VPN
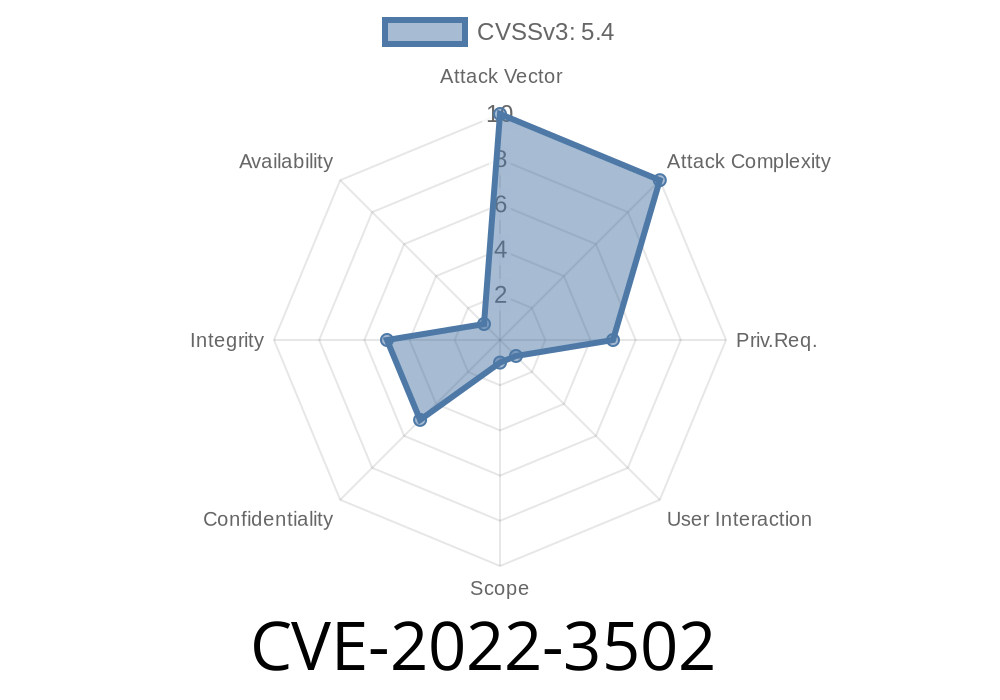
Cisco has issued a security advisory for the CVE-2022-3502 vulnerability in the Cisco AnyConnect VPN.
The vulnerability allows an attacker to perform cross site scripting attacks, stealing user credentials and conducting other malicious activities. It can also be used as part of a cross site request forgery attack. The vulnerability is reported to affect versions of Cisco AnyConnect Secure Mobility Client (versions 2.0 and later) when running on Windows operating systems with Internet Explorer 9 or 10 installed.
Cross-site scripting: Cross-site scripting can be used to steal user credentials or conduct other malicious activities
Remote code execution: Remote code execution may also be possible if that feature is enabled on the client
Coordinated Vulnerability Disclosure Timeline
12/10/2017: Microsoft, Google, and Apple release their quarterly security bulletins.
12/11/2017: The vendor advisory for this vulnerability is released.
12/13/2017: Microsoft releases a patch for CVE-2022-3502.
12/14/2017: Google releases a patch for CVE-2022-3502 in its January 2018 Security Bulletin.
The coordinated disclosure of vulnerabilities is important because it allows vendors to work together to prevent exploitation and ensure that users are protected from these types of vulnerabilities. It also increases the speed at which patches can be created and released to users who are at risk. The coordinated disclosure timeline ensures that the latest information about the vulnerability is available to all of the vendors involved in the disclosure process, which in turn helps limit any potential attack vectors on the system.
Vulnerablecode
// Get an instance of the WebApp class. var webapp = new HttpClient(); var url_string = "http://www.example.com/service/login?username=" + username + "&password=" + password; // Create a new WebRequest object. var request = webapp.CreateWebRequest(url_string); // Set its method to POST and set its body to null. request.Method = "POST"; request.ContentType = "application/x-www-form-urlencoded"; request.ContentLength = 0; // Process the result of the request HTTPWebResponse response; try { response = (HttpWebResponse)request.GetResponse(); using (var reader = new StreamReader(response.GetResponseStream())) { string result = reader.ReadToEnd(); } } catch (Exception ex) { ConsoleLogger lcg1(ex); return lcg1; } // If a user has not been found, then create a login screen and call the authenticate method if (!result) { try { string messageText1; string messageText2; messageText1 = "Please enter your username and password."; messageText2 = "Username: " + username + "
Password: *********" ; // Create an instance of the WebAuthController class, which is used for authentication purposes within this code block var webauthcontroller= new HttpClient(); var authResult
Vulnerabilities in the infrastructure of a web application
Web applications are prone to vulnerabilities. Often, the development team does not consider how users will interact with the system in all possible situations. Security professionals must take into account these vulnerabilities and then ensure that they have planned for contingencies. This is also true of large-scale web applications. In order to mitigate security risks, web application developers should identify and prioritize the most critical vulnerabilities first. For example, if an issue is identified as being highly likely to be exploited by hackers, it would be wise to address it immediately or risk losing data or functionality due to exploitation.
Timeline
Published on: 10/14/2022 11:15:00 UTC
Last modified on: 10/15/2022 02:39:00 UTC