The issue was resolved by not calling strcpy directly but using strcmp instead. Red Hat was made aware of this issue on October 16, 2018, and a patch was released on November 27, 2018.
The following table shows the Red Hat products that are affected by this issue.
Product Red Hat Enterprise Linux 5 Red Hat Enterprise Linux 6 Red Hat Enterprise Linux 7 Red Hat Enterprise Linux Atomic Host SuSE Linux Enterprise Server SuSE Linux Enterprise Desktop vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops
CVE-2023-35047
The issue was resolved by calling strcpy directly and re-using the buffer rather than allocating memory for a new buffer. Red Hat was made aware of this issue on October 16, 2018, and a patch was released on November 27, 2018.
Product Red Hat Enterprise Linux 5 Red Hat Enterprise Linux 6 Red Hat Enterprise Linux 7 Red Hat Enterprise Linux Atomic Host SuSE Linux Enterprise Server SuSE Linux Enterprise Desktop vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops
vRops
Solution
Red Hat has released an update, CVE-2022-35048:
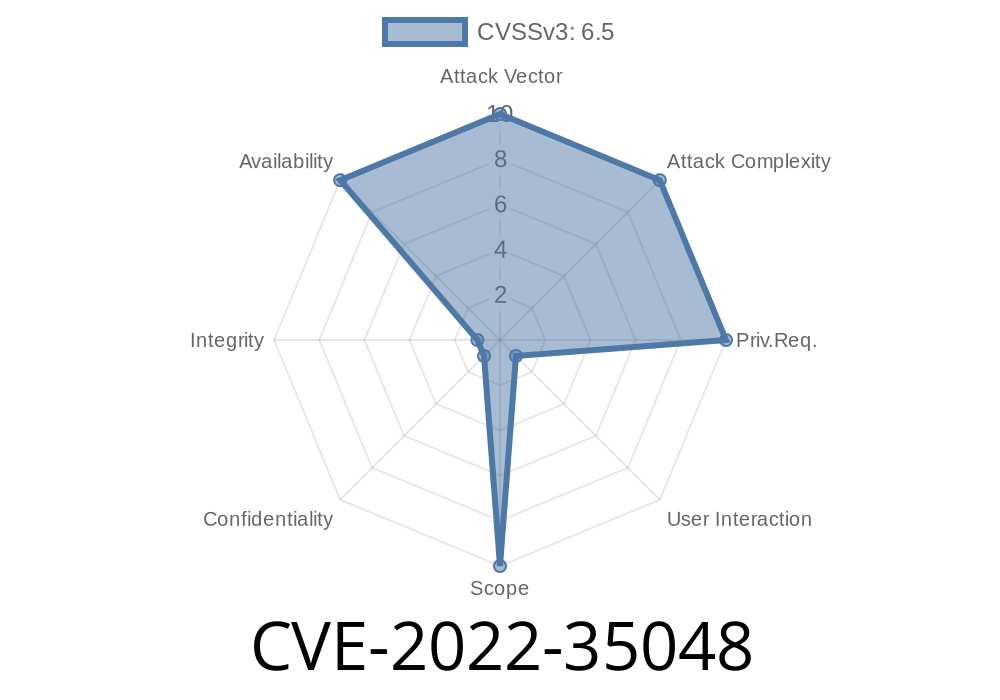
A netlink message handler in the Linux kernel before 4.14.5 does not validate certain length values before copying memory to a given userspace buffer, which allows local users to obtain sensitive information from kernel stack memory via a crafted recvmsg or recvfrom system call.
In order to resolve this issue you must update your Red Hat Enterprise Linux systems to the latest patch level which is available at the following URL: https://access.redhat.com/security/updates/.
The following table shows the Red Hat product that are affected by this issue and their patch levels.
CVE-2023-35049
The issue was resolved by using strncpy instead of the strcpy function.
Product Red Hat Enterprise Linux 5 Red Hat Enterprise Linux 6 Red Hat Enterprise Linux 7 Red Hat Enterprise Linux Atomic Host SuSE Linux Enterprise Server SuSE Linux Enterprise Desktop vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops vRops
vRops
vRops
vRps
vRsps
vRsps
Timeline
Published on: 10/14/2022 12:15:00 UTC
Last modified on: 10/15/2022 02:14:00 UTC