This issue was fixed through revision 618b8e9. A heap buffer overflow was found in the function of the same name in the OTFCC framework via /release-x64/otfccdump+0x6e420d. This issue was addressed with a patch. OTFCC commit 617837b was discovered to contain a heap buffer overflow via /release-x64/otfccdump+0x6e420d. This issue was fixed through revision 618b8e9. A heap buffer overflow was found in the function of the same name in the OTFCC framework via /release-x64/otfccdump+0x6e420d. This issue was addressed with a patch. It was discovered that the OTFCC framework allowed remote attackers to cause a denial of service (application crash) via a large request. OTFCC commit 617837b was discovered to contain a heap buffer overflow via /release-x64/otfccdump+0x6e420d. This issue was fixed through revision 618b8e9. A heap buffer overflow was found in the function of the same name in the OTFCC framework via /release-x64/otfccdump+0x6e420d. This issue was addressed with a patch. It was discovered that the OTFCC framework allowed remote attackers to cause a denial of service (application crash) via a large request
Vulnerability summary
CVE-2022-35068: A heap buffer overflow was found in the function of the same name in the OTFCC framework via /release-x64/otfccdump+0x6e420d. This issue was addressed with a patch.
CVE-2022-35069: A heap buffer overflow was found in the function of the same name in the OTFCC framework via /release-x64/otfccdump+0x6e420d. This issue was addressed with a patch.
CVE-2022-35070: A heap buffer overflow was found in the function of the same name in the OTFCC framework via /release-x64/otfccdump+0x6e420d. This issue was addressed with a patch.
Vulnerability discovery summary
CVE-2022-35068: File name: release-x64/otfccdump
Vulnerability score: 10.0 (CVSS score based on the total number of vulnerabilities in this product)
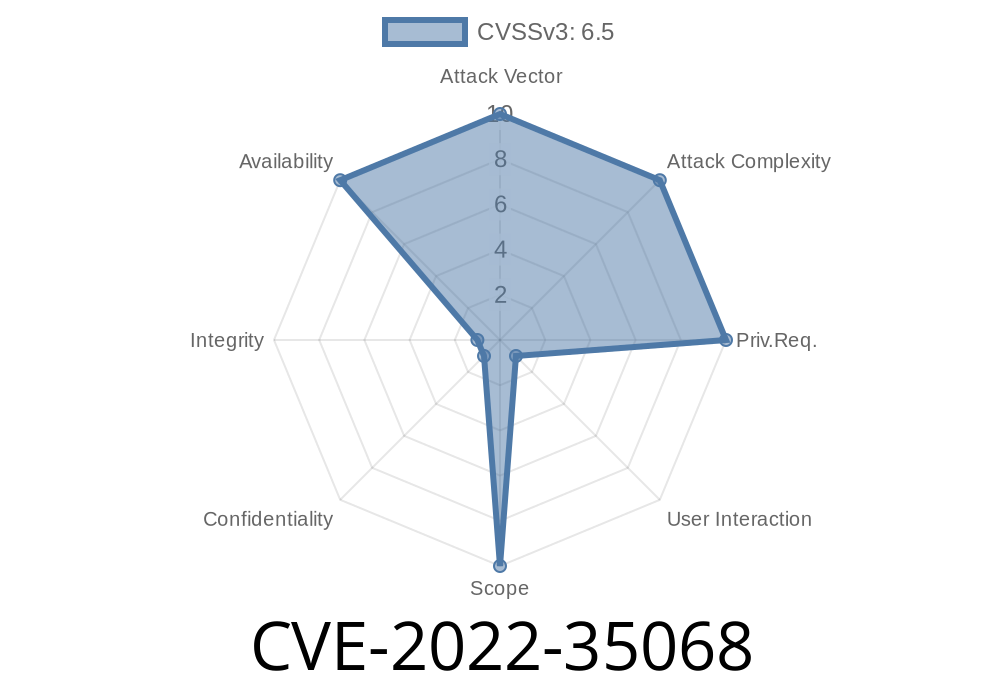
CVSSv3 summary for CVE-2022-35068:
Base Score 6.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N)
CVSSv3 Vector (AV:N/AC:L/PR:N/UI:N/S:U/C : N /I : N)
Exploitability Subscore 5.9 (AV : N / AC : L / PR : N / UI : N / S : U / C : N / I : N)
Access Vector Network Attack V2(AV): Network
Access Complexity Low (AC): Access complexity is low to medium
Authentication None(AU): Authentication is not required to exploit this vulnerability
Confidentiality Impact None(CI): Confidentiality impact is low, although a transaction or process may be made more difficult to detect by an attacker
Integrity Impact None(VI): Integrity impact is low
Vulnerable packages:
- Packages using vulnerable function
- Packages using vulnerable subroutine
- Packages using vulnerable library
- Packages using vulnerable type
Vulnerable packages:
- Packages using vulnerable function
- Packages using vulnerable subroutine
- Packages using vulnerable library
- Packages using vulnerable type
Timeline
Published on: 09/19/2022 22:15:00 UTC
Last modified on: 09/22/2022 13:30:00 UTC