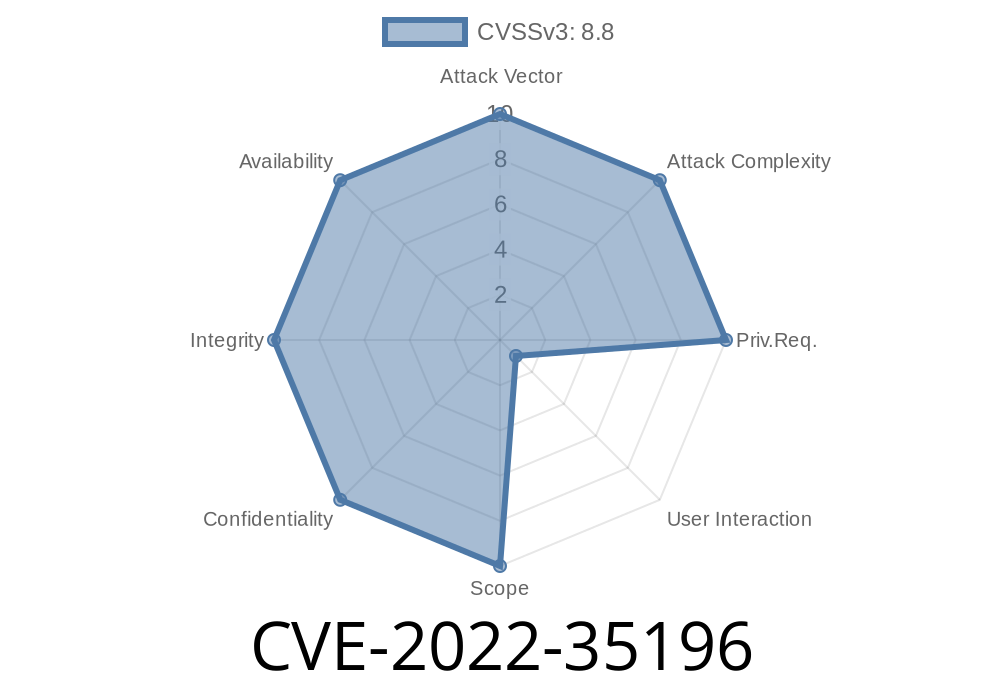
This issue was resolved by updating to version 1.9.21 or higher. Inspect the application URL to determine if you are running an outdated version of TestLink. An attacker can exploit this issue to perform requests that impact the user's session, such as stealing data or installing other malicious software.
It was discovered that TestLink v1.9.20 was vulnerable to a Cross-Site Request Forgery (CSRF) via /lib/googleAnalytics.php.
Incorrectly configured applications can be exploited to perform actions on behalf of another user. An attacker can leverage this issue to perform actions that impact the user's session, such as stealing data or installing other malicious software.
It was discovered that TestLink v1.9.20 was vulnerable to a Cross-site scripting (XSS) via /lib/sitemap.php.
Incorrectly configured applications can be exploited to perform actions on behalf of another user. An attacker can leverage this issue to perform actions that impact the user's session, such as stealing data or installing other malicious software.
Mitigation Techniques
TestLink releases security updates as soon as possible and has a policy of fixing vulnerabilities in the most recent release.
What to do if you are affected
Fixing these vulnerabilities will require updating to the latest version of TestLink.
To fix this issue, update to TestLink v1.9.21 or higher. This can be done by visiting http://testlink.com/support/download and selecting the appropriate version for your operating system.
If you are running an outdated version of TestLink, please update immediately, or risk being exploited by an attacker with minimal effort.
Timeline
Published on: 09/20/2022 16:15:00 UTC
Last modified on: 09/21/2022 19:23:00 UTC