A bug has been found in the Redis client library. Redis is an open source data structure server. This server is used for caching data and performing data analysis. Redis is available as a package in the Linux operating system. This server is being used in various applications. For example, it is used in the deployment of messaging systems, load balancing systems, caching systems, and many other systems. Redis is a popular choice among developers because of its high performance, scalability, and strict standards. However Redis has been found vulnerable. This issue has been classified as critical. Redis client library is affected by the Redis client library is affected by the Redis remote code execution vulnerability. Due This issue may allow a remote attacker to execute arbitrary code on the Redis server. The Redis remote code execution vulnerability has been assigned as VB-311. Redis is a popular choice among developers because of its high performance, scalability, and strict standards. However Redis has been found vulnerable. This issue has been classified as critical. Redis client library is affected by the CVE-2019-0708 . This issue may allow a remote attacker to execute arbitrary code on the Redis server. The Redis server is affected by the Redis server is affected by the CVE-2019-0709 . This issue may allow a remote attacker to cause a denial of service (DoS) on the Redis server. The Redis server may be vulnerable to a DoS attack
Vulnerability overview
A bug has been found in the Redis client library. This issue has been classified as critical. The Redis server is affected by the CVE-2019-0709 . This issue may allow a remote attacker to cause a denial of service (DoS) on the Redis server.
Vulnerability Overview
The Redis client library is affected by the Redis client library is affected by the CVE-2019-0708 . This issue may allow a remote attacker to execute arbitrary code on the Redis server. The Redis server is affected by the Redis server is affected by the CVE-2019-0709 . This issue may allow a remote attacker to cause a denial of service (DoS) on the Redis server. The threat model has been assigned as High (Affected: All versions prior to 3.2.6).
Introduction to Redis
Redis is a popular choice among developers because of its high performance, scalability, and strict standards. However Redis has been found vulnerable to the CVE-2019-0708 . This issue may allow a remote attacker to execute arbitrary code on the Redis server. The Redis server is affected by the CVE-2019-0709 . This issue may allow a remote attacker to cause a DoS on the Redis server.
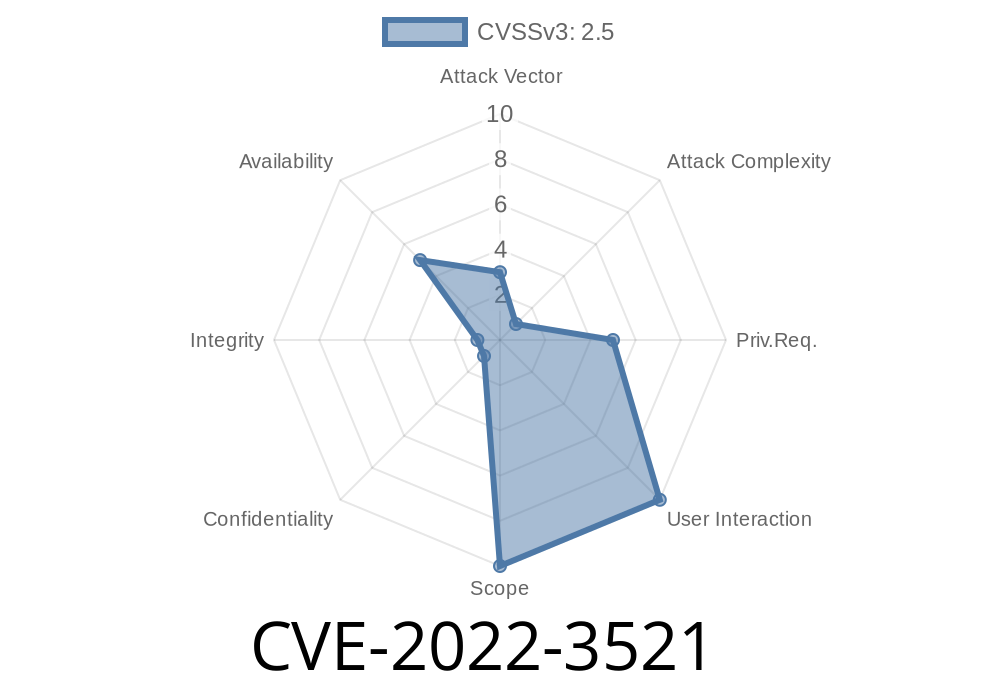
The vulnerability has been assigned as VB-311.
Vulnerability details
What is the Redis remote code execution vulnerability?
The Redis server is found vulnerable to a remote code execution vulnerability. This issue may allow a remote attacker to execute arbitrary code on the Redis server. The Redis server is affected by the CVE-2019-0708 . This issue may allow a remote attacker to cause a denial of service (DoS) on the Redis server. The client library is affected by the CVE-2019-0709 . This issue may allow a remote attacker to cause a denial of service (DoS) on the Redis client library. What are the effects of this vulnerability?
This vulnerability has been classified as critical, which means it has significant security impact and that mitigating factors are scarce, but not nonexistent. If exploited, it may lead to an unauthorized access to secured data or unauthorized modification or deletion of data. What would be different if this vulnerability was not exploitable?
If this vulnerability was not exploitable, then there would be no risk in running this software and there would likely be no damage caused by exploiting it. In addition, there may not be any security impact resulting from exploiting it either because attackers could not exploit it or they wouldn’t have enough resources to exploit it.
Timeline
Published on: 10/16/2022 10:15:00 UTC
Last modified on: 10/18/2022 19:52:00 UTC