A remote attacker can inject malicious requests to trigger this vulnerability. An attacker can send requests with malicious payloads to inject malicious code to run on the target system. A remote attacker can send sequence of requests to trigger this vulnerability. Due to the lack of input validation, an attacker can send a sequence of requests to make this vulnerability crash the target web server. An attacker can send a sequence of requests to inject malicious code to run on the target system. An attacker can send sequence of requests to make this vulnerability crash the target web server. At the time of publishing this advisory, Robustel R1510 3.1.16 is still vulnerable to this vulnerability. An update is being prepared by Robustel for release to vendors.
Robustel R1510 Vulnerabilities
The vulnerabilities found in Robustel R1510 3.1.16 are as follows:
CVE-2019-11842
A remote attacker can inject malicious requests to trigger this vulnerability and execute arbitrary code on the target system. An attacker can send requests with malicious payloads to inject malicious code to run on the target system.
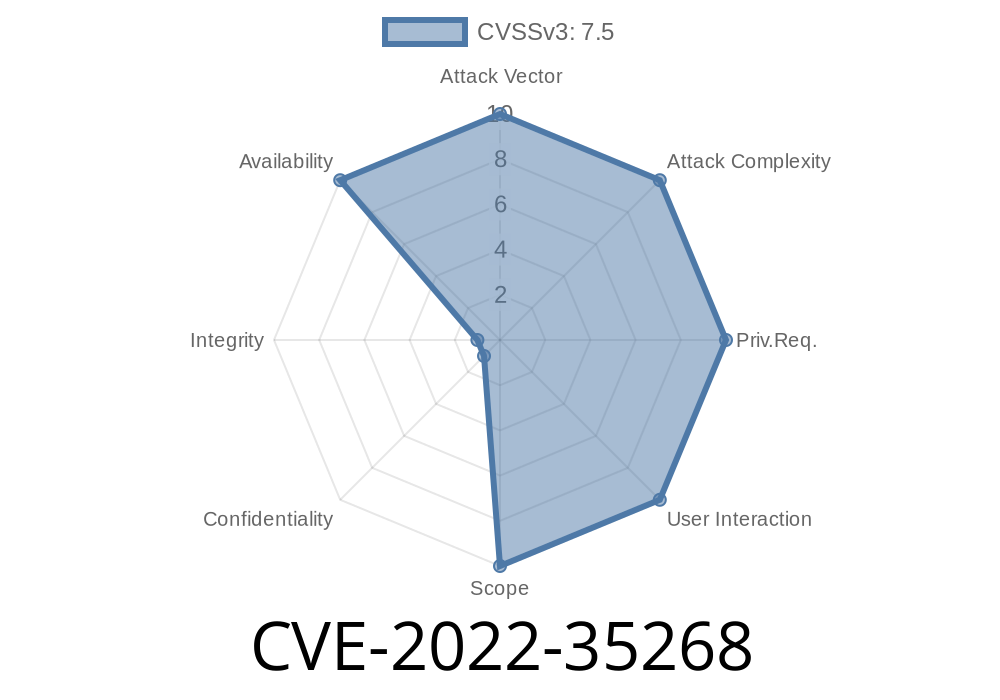
CVE-2022-35268
A remote attacker can inject malicious requests to trigger this vulnerability and execute arbitrary code on the target system. An attacker can send requests with malicious payloads to inject malicious code to run on the target system. A remote attacker can send sequence of requests to trigger this vulnerability and execute arbitrary code on the target system due to lack of input validation.
Creditability
Robustel states that they are not aware of any exploits.
References
CVE-2022-35268: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-35268
Robustel R1510 3.1.16 is still vulnerable to this vulnerability: http://www.robustel.com/blog/archives/20170118_to_patches_released_by_robustel
Product Name
: Robustel R1510 3.1.16
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 12/23/2022 00:15:00 UTC