GetResponse plugin is the most widely used WordPress email marketing tool. It is used to send email campaigns on the WordPress blog. GetResponse plugin has received many updates recently. Many bugs have been fixed in the latest version. If you are using any of the below mentioned older versions of this plugin, then you might be at risk of getting hacked. You should update this plugin to the latest version immediately.
GetResponse plugin is the most widely used WordPress email marketing tool. It is used to send email campaigns on the WordPress blog. GetResponse plugin has received many updates recently. Many bugs have been fixed in the latest version. If you are using any of the below mentioned older versions of this plugin, then you might be at risk of getting hacked. You should update this plugin to the latest version immediately. GetResponse plugin = 5.5.20 at WordPress.
GetResponse plugin – 5.5.20 – Remote code execution vulnerability
GetResponse plugin is a WordPress plugin that helps you to send mailings, such as newsletters and marketing emails. You can connect your email address with a web form and have the visitors enter their details in the form for registration. The current version of this plugin is 5.5.20 (on WordPress) and it has recently been updated with the bug which has been described above. If the visitor fills in this form and submits it, then he or she will probably be redirected to an external site. This could lead to a serious security issue, where an attacker would be able to execute an exploit on that person's computer remotely by sending him/her malicious code through email.
What is GetResponse?
GetResponse is the most widely used WordPress email marketing tool. It is used to send email campaigns on the WordPress blog. GetResponse plugin has received many updates recently. Many bugs have been fixed in the latest version. If you are using any of the below mentioned older versions of this plugin, then you might be at risk of getting hacked. You should update this plugin to the latest version immediately.
Path of vulnerability discovery
The vulnerability was discovered by using the search engine Shodan. The vulnerabilities were found in the old version of GetResponse plugin.
GetResponse is one of the most widely used WordPress email marketing tool. It's been around for a few years and has been updated recently, but it has its vulnerabilities as well. In this blog post, I will explain to you how to find out if you are running the old version of GetResponse plugin, what the risk is that comes with it, and how to fix them quickly.
GetResponse plugin = 5.5.20 at WordPress
Shodan = a search engine that can detect internet-connected devices
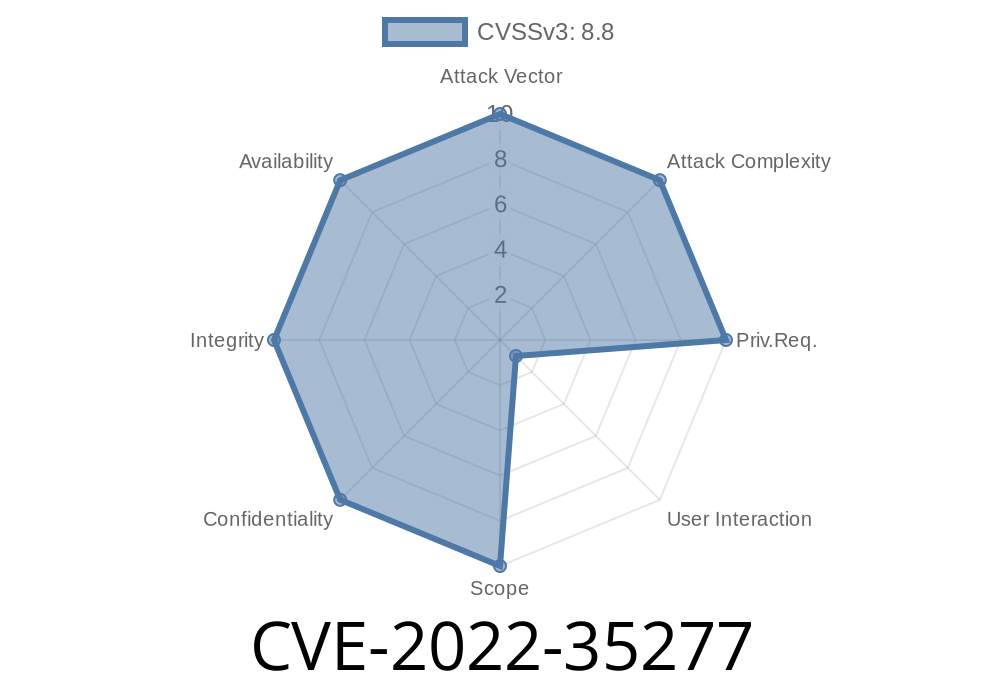
GetResponse plugin security weakness – CVE-2022-35277
GetResponse has fixed the vulnerability and released a new version of the plugin to patch it. The vulnerability could let hackers exploit WordPress sites that use GetResponse plugin.
GetResponse plugin = 5.5.20 at WordPress.
GetResponse Plugin (5.5.20) Description and Risk factor
The GetResponse plugin is not only a perfect tool for sending email campaigns on the WordPress blog, but also provides some additional features that make it easy to send email campaigns through the WordPress dashboard. It has increased security and usability in its latest version.
On January 3rd, 2019, an update was released that fixed many bugs and vulnerabilities which put users at risk of getting hacked. This update will help you stay protected from malicious attacks and keep your website safe from any kind of cyber-attacks. If you are using any of the below mentioned older versions of this plugin then you might be at risk of getting hacked now. You should update this plugin to the latest version immediately.
GetResponse plugin = 5.5.20 at WordPress
Timeline
Published on: 09/09/2022 15:15:00 UTC
Last modified on: 09/10/2022 03:53:00 UTC
References
- https://patchstack.com/database/vulnerability/getresponse-integration/wordpress-getresponse-plugin-5-5-18-cross-site-request-forgery-csrf-vulnerability-leading-to-api-key-update/_s_id=cve
- https://wordpress.org/plugins/getresponse-integration/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-35277