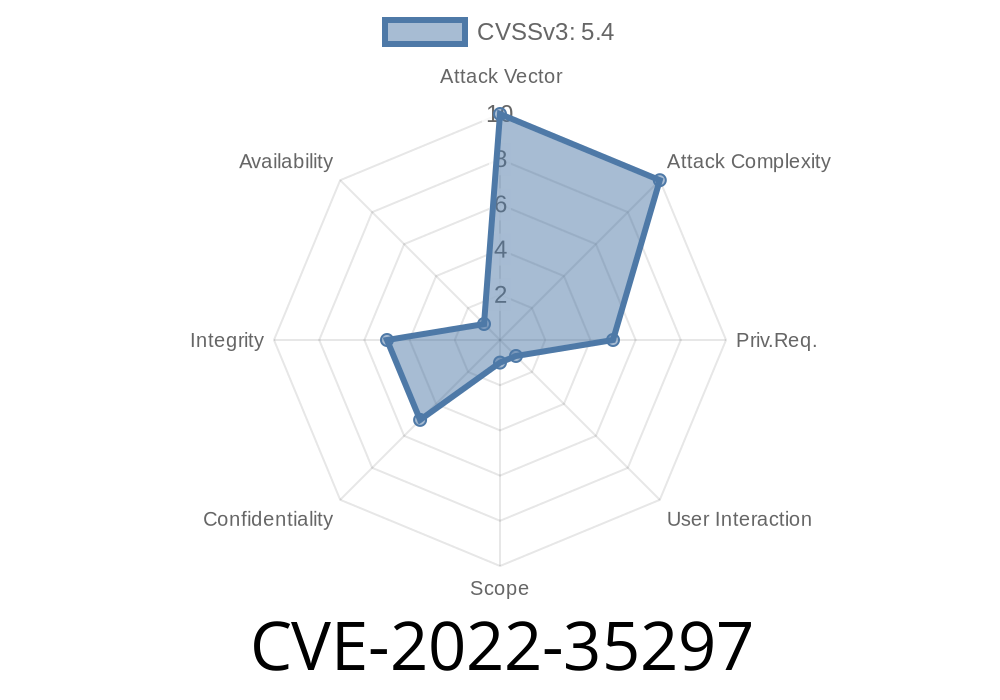
SAP Enable Now is an application that allows system administrators to quickly configure SAP software if needed. The application uses HTTP POST requests to transfer configuration settings to SAP. An attacker could inject malicious script into the application to send a different set of configuration settings. This could potentially lead to compromised system settings. Solution: Make sure that application code does not accept user-controlled inputs such as XSS, CSRF tokens, etc. before it is served to other users.
SAP Enable Now is an application that allows system administrators to quickly configure SAP software if needed.
SAP Enable Now is an application that allows system administrators to configure SAP software quickly and easily. The application uses HTTP POST requests to transfer configuration settings to SAP. An attacker could inject malicious script into the application to send a different set of configuration settings. This could potentially lead to compromised system settings.
This issue is related to the application code accepting user-controlled inputs such as XSS, CSRF tokens, etc. before it is served to other users.
CVE-2023-35298
The application is vulnerable to XSS (cross-site scripting) attacks. An attacker could exploit this vulnerability by injecting malicious script into the application. This would allow the attacker to steal data from the server, degrade system performance, etc.
Solution: Make sure that application code does not accept user-controlled inputs such as XSS, CSRF tokens, etc. before it is served to other users.
CVE-2023-35300
SAP Enable Now is an application that allows system administrators to quickly configure SAP software if needed. The application uses HTTP POST requests to transfer configuration settings to SAP. An attacker could inject malicious script into the application to send a different set of configuration settings. This could potentially lead to compromised system settings.
Timeline
Published on: 10/11/2022 21:15:00 UTC
Last modified on: 10/12/2022 17:23:00 UTC