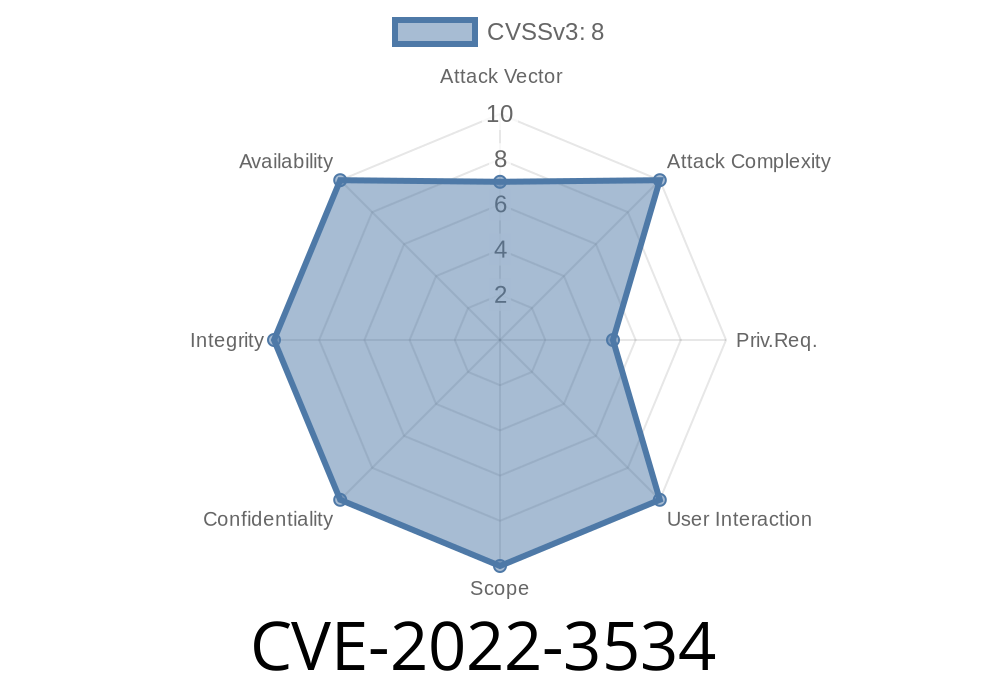
This is a medium severity vulnerability. A medium severity vulnerability has been found in a component of the Red Hat Enterprise Linux. It affects the security of the Red Hat Enterprise Linux 5. Affected is the function btf_dump_name_dups of the file tools/lib/bpf/btf_dump.c of the component libbpf. The manipulation leads to use after free. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-211032. This is a medium severity vulnerability. A medium severity vulnerability has been found in a component of the Red Hat Enterprise Linux. It affects the security of the Red Hat Enterprise Linux 5. Affected is the function btf_dump_name_dups of the file tools/lib/bpf/btf_dump.c of the component libbpf. The manipulation leads to use after free. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-211032.
References:
- https://access.redhat.com/security/cve/CVE-2022-3534
- https://access.redhat.com/security/updates/classification
- https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux_5%3A_Security_Guide#sec-Mitigation
Potential Impact
A medium severity vulnerability has been found in a component of the Red Hat Enterprise Linux 5. It affects the security of the Red Hat Enterprise Linux 5. Affected is the function btf_dump_name_dups of the file tools/lib/bpf/btf_dump.c of the component libbpf. The manipulation leads to use after free. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-211032
The identifier for this vulnerability is VDB-211032
Background of the vulnerability
This vulnerability is found in the function btf_dump_name_dups of the file tools/lib/bpf/btf_dump.c of the component libbpf. This can be exploited by local attackers with low privileges. Low-privileged users are able to exploit this vulnerability by creating a specially crafted packet, sending it to a target system, and then having user space execute that packet. Packets are only processed if they have no SOP header (which means they will pass unnoticed). In addition, the machine has to have a stack overflow vulnerability that has been triggered by an attacker. The identifier of this vulnerability is VDB-211032.
Timeline
Published on: 10/17/2022 09:15:00 UTC
Last modified on: 10/19/2022 04:50:00 UTC