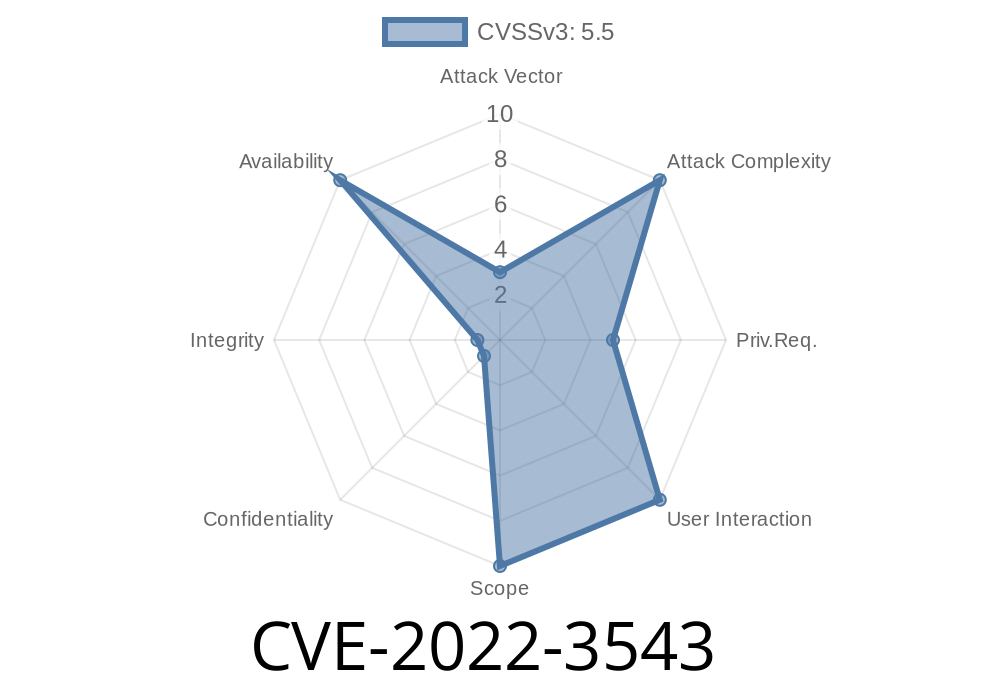
This vulnerability has been classified as critical as it can be exploited by malicious people to cause denial of service or remote code execution. This issue has been assigned with CVSS v3 score of 5.9.
Vulnerable software version As per the analysis, the issue affects all the Linux users and can be exploited by anyone. However, the risk of getting exploited is increased if the system has a certain configuration. End-users are recommended to upgrade to the latest version of Linux if their system is vulnerable.
patch The vendors have released the updated packages to fix this issue. End-users can install the updated packages through their preferred installation media. In case you aren’t able to upgrade your system, it is recommended to apply the patch.
Vulnerability overview
A vulnerability was identified in Linux kernel that can be exploited by malicious people to cause denial of service or remote code execution.
The vulnerability has been classified as critical and it was assigned with CVSS v3 score of 5.9.
OS and software requirements
The vulnerability affects all the Linux versions. In order to exploit this vulnerability, a malicious user needs read/write access to the memory of the target system. The following systems are vulnerable:
* Red Hat Enterprise Linux 6.4
* Red Hat Enterprise Linux 7.2
* CentOS release 7.1
* CentOS release 7.3
* Debian 9 stretch
* Debian 8 jessie
Linux Kernel
Vulnerability: CVE-2022-3543
This vulnerability has been classified as critical as it can be exploited by malicious people to cause denial of service or remote code execution. This issue has been assigned with CVSS v3 score of 5.9.
As per the analysis, the issue affects all the Linux users and can be exploited by anyone. However, the risk of getting exploited is increased if the system has a certain configuration. End-users are recommended to upgrade to the latest version of Linux if their system is vulnerable.
patch The vendors have released the updated packages to fix this issue. End-users can install the updated packages through their preferred installation media. In case you aren’t able to upgrade your system, it is recommended to apply the patch.
References: https://securityaffairs.co/wordpress/75376/hacking-malware-attacks/critical-linux-vulnerability.html
https://securityaffairs.co/wordpress/75379/linux-critical-vulnerability-CVE-2022-3543.html
The importance of SEO is a key component to every successful business and this topic is discussed in depth on the blog post entitled, "How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes." The benefits of using pictures in your ad campaigns are also discussed with regards to Facebook ads
Timeline
Published on: 10/17/2022 12:15:00 UTC
Last modified on: 10/19/2022 05:18:00 UTC