When the server receives the crafted packet, it could cause a heap-based buffer overflow, due to incorrect validation of user-supplied data. An attacker can leverage this vulnerability to execute arbitrary code on the targeted system. In most cases, an attacker requires user-to-user contact to exploit this issue.
Adobe recommends users apply the ColdFusion update as soon as possible. In addition to ColdFusion, Adobe recommends users apply updates for other components as well. End users can also follow best practices to prevent this issue from being exploited in the first place, such as: Restricting network access to trusted individuals only.
Using a network monitoring solution to track traffic entering the network.
Ensuring users follow multifactor authentication to prevent unapproved login attempts. Adobe recommends users immediately apply the ColdFusion update. Update 14 (and earlier) and Update 4 (and earlier) are affected by a Heap-based Buffer Overflow vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue does not require user interaction, the vulnerability is triggered when a crafted network packet is sent to the server.
Adobe Reader and Acrobat Software Updates
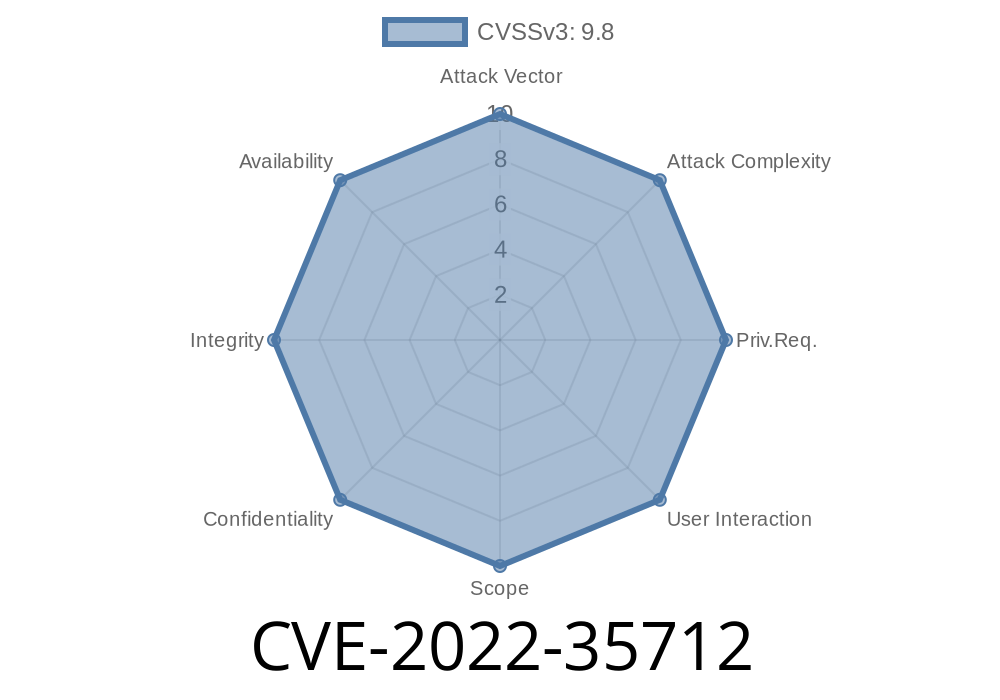
Adobe released updates for Adobe Reader and Acrobat software. The update addresses the vulnerabilities described in CVE-2022-35712 and CVE-2018-4942. Updates have been provided for all impacted versions of Adobe Reader and Acrobat, so it is recommended to apply them as soon as possible.
Adobe recommends users apply the following updates to address the vulnerabilities:
Vulnerability overview
The vulnerability is triggered when a crafted network packet is sent to the server. It causes a Heap-based Buffer Overflow in the browser. There are two different attack scenarios: An attacker can leverage this vulnerability to execute arbitrary code on the targeted system. In most cases, an attacker requires user-to-user contact to exploit this issue. An attacker could exploit this vulnerability by sending a specially crafted HTTP request that would cause the application to crash or execute code of their choice on behalf of the current user.
Adobe recommends users apply the CCF update as soon as possible, as well as updating other components of their software stack, such as Flash and Acrobat Reader. Users can also follow best practices to prevent this issue from being exploited in the first place, such as: Restricting network access to trusted individuals only. Using a network monitoring solution to track traffic entering the network. Ensuring users follow multifactor authentication to prevent unapproved login attempts.
What is the Update 14 (and earlier) vulnerability?
The vulnerability in Adobe ColdFusion that is being discussed is update 14 (and earlier). The update, as mentioned in the title, has a Heap-based Buffer Overflow vulnerability that could result in arbitrary code execution. This can happen when a crafted network packet is sent to the server.
Timeline
Published on: 10/14/2022 20:15:00 UTC
Last modified on: 10/14/2022 20:31:00 UTC