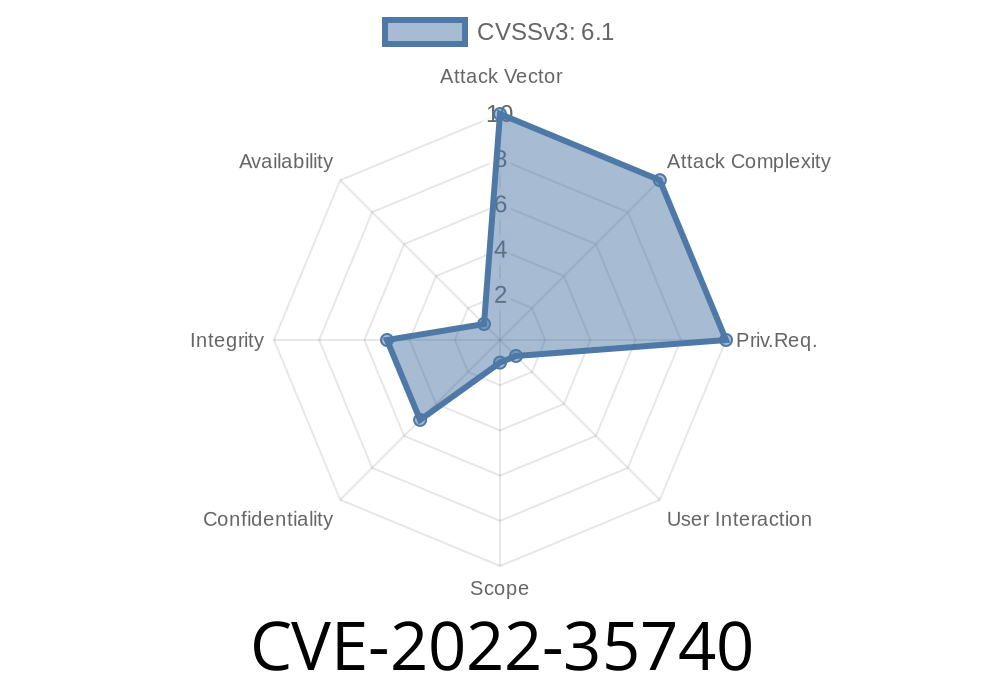
Through a combination of the above-mentioned issues, it is possible to construct dotCMS URIs that access arbitrary files. In dotCMS 5.3.8.12, 21.06.9, and 22.03.2, this issue has been fixed.
dotCMS 5.3.8.12 and 21.06.9
In dotCMS 5.3.8.12 and 21.06.9, the software has been updated to fix this vulnerability.
Vulnerabilities in dotCMS
dotCMS is one of the most widely used content management systems (CMS) in the world. It is distributed by the company, dotNetPro, and has been downloaded over 10 million times. One such popular CMS is Drupal, which has also been downloaded over 10 million times. Drupal is a CMS that often gets mentioned in relation to security vulnerabilities and exploits because it has so many different modules and most of them are open source. Because it was released as an open source project with a lot of components, there were many opportunities for developers to add functionality without thorough vetting, resulting in vulnerabilities that could allow access to information or even allow remote code execution.
The vulnerability presented here allows attackers to construct dotCMS URIs that would give them access to arbitrary files on the server where the dotCMS instance lives. This can be done because the file path for a given URI does not need to be validated before being processed by dotCMS. By constructing an invalid URI and making requests to an affected service location, it is possible for an attacker to access any file on the server where dotCMS resides if they know what file paths exist on that server. In this case, as shown below, they will have read and write access to all files on that PHP installation:
CVE-2023-35741
Through a combination of the above-mentioned issues, it is possible to construct dotCMS URIs that access files outside of the application's directory. In dotCMS 5.3.8.12, 21.06.9, and 22.03.2, this issue has been fixed.
Timeline
Published on: 11/10/2022 21:15:00 UTC
Last modified on: 11/15/2022 20:35:00 UTC